White Papers
Abstract
Part 3 of this multi-part article series discusses DataPower AAA policies, form login policies, and their role in supporting the OAuth 2.0 protocol. Since the form login policy provides value beyond its OAuth role, a form-based authentication service proxy is implemented with a multi-protocol gateway to demonstrate how the AAA policies and form login policies work together. As mentioned in Part 2, the WTS wizard is employed in a form-based OAuth scenario to demonstrate the automation of many of the manual MPGW steps.
Content
AAA is a framework within the WebSphere DataPower firmware. It stands for authentication, authorization, and auditing. DataPower takes advantage of AAA extensively to support the OAuth 2.0 protocol. AAA is used to authenticate both the resource owner's and OAuth client's identities. It is also used for authorizing a request. In release 3.8.1, DataPower introduced form-based authentication, which is tied closely with the web application firewall service. As of the 5.0 firmware release, its support was expanded to other service objects. In Part 3 of the series, we cover how AAA is used for OAuth support and explain how form-based authentication works with DataPower. You cannot use form-based authentication in an XML Firewall service. There are two types of support for OAuth within DataPower; both rely heavily on AAA. For an overview of the OAuth protocol, refer to Part 1 of this series, Introducing OAuth 2.0 support in DataPower. An OAuth client is identified by the client id and optionally verified through a client secret. The resource owner grants permission to an OAuth client to access the owner's resource within a resource scope, without sharing the resource owner's credential with the OAuth client. Figure 1 shows an overview of AAA. AAA is made up of seven phases. Some phases consume the results from a previous phase. Note: From firmware 5 to 6, the names of the AAA phases changed from verbs to nouns. For example, "Extract Identity" became "Identity extraction." The following sections describe the role of each AAA phase in terms of its relevance to OAuth scenarios. The action taken in a phase depends on the OAuth role addressed. The three roles are: Table 1 provides a column for each of these roles. Each row corresponds to a box in Figure 1. It lists the configuration for that AAA phase pertinent to the role. Post-processing is optional in the native OAuth protocol support. For DataPower acting as an enforcement point, with Federated Identity Manager as an authorization server, you can use PP to generate the token produced by the AAA policy. Figure 2 illustrates steps for the case where the service proxy is an enforcement point rather than an authorization server. Figure 3 describes AAA policy configuration in the case of an authorization server. Form-based login authentication presents a user with an HTML login form. The user enters his or her credential (for example, name and password), and submits the form. These credentials are used for authentication. For OAuth, the resource owner can be presented with a form for authentication. In this section, we cover how DataPower supports form-based authentication and how it can be used as part of the OAuth flow by use of the web token service (WTS) or multi-protocol gateway (MPGW) as the service gateway. Note that the XML Firewall is not supported for form-based authentication. Then, we demonstrate how AAA policies can be created to implement a simple form-based authentication service proxy that uses a MPGW. This scenario is independent of OAuth. Next, we import an OAuth-specific AAA policy and use it to create a WTS that uses the wizard. An OAuth-specific AAA policy references client registration objects and uses special EI settings for OAuth. These details are covered in each of the scenario-oriented articles in Parts 4, 5, and 6. In this article, we undertake the following tasks: In Part 2, you imported an HTML form-based login policy and AAA action and then used them to create a WTS manually (without the wizard). In this part, we are creating them explicitly and incorporating them into a MPGW. The Downloadable resources section of this article provides the following files: After the form-login policy has been created, there is now two: the one you created and the one that was imported (to be used later). You now have three AAA policies: the one you imported and two you created. The one you imported is used later for the WTS creation wizard. The two you created is used in policy rules of the MPGW created in the next step. In this section, you use the two form-based AAA policies created to configure a Multi-Protocol Gateway that implements form-based authentication. This demonstrates the form-based authentication capability beyond its application to OAuth. This completes the configuration of a form-based authentication service proxy. Here are some things to keep in mind regarding this simple example. In the previous exercise, we demonstrated how form-based login policies and AAA policies are used to implement a form-based login authentication service proxy. It was not an OAuth scenario; but, it employed tools that are heavily used in OAuth scenarios. It required creating all the multi-step policy rules from scratch, which served to give us a deeper understand of how these elements work together. In this section, we create a WTS using an imported AAA policy named OAuth-FormLogin-AAA. This AAA policy is similar to PlainFormLoginAAA that we configured earlier. It differs by specifying OAuth in some of the AAA stages and referencing client registration objects that can be covered in the scenario-driven articles later in this series (Parts 4, 5, 6, and 8). This sample shows how the WTS wizard generates much of what we created manually in the previous section for an OAuth-based form login. Note the following about the panel in Figure 13: This article explained how the AAA policy is used to support OAuth within DataPower. Additionally, it covered how to configure form-based authentication in AAA for user identity extraction. The article also showed how the wizard for the Web Token Service simplifies the complexity of form-based resource owner authentication when used by the OAuth authorization server. The authors would like to thank Martin Lansche and John Rasmussen for reviewing this article.Introduction
Types of OAuth support in DataPower
Overview of AAA
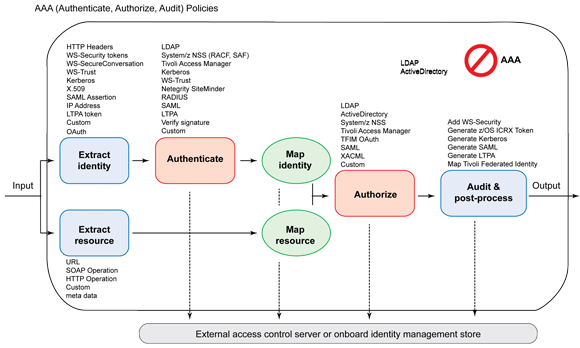
AAA phase Authorization server PEP standalone PEP with FIM EI
Extract OAuth client credential with any method. AU Define how to authenticate the resource owner from EI. Select Pass Identity Token to Authorize Step since the access token was verified in the EI phase. Client authentication can be performed using any method. MC Define how to map the resource owner's credential from EI or AU. Select None. There is no resource owner in step. The access token was verified in the EI step. Select None. ER
Use any method to extract the resource. MR Select any addition verification that is needed for the scope. Usually it is None. (Optional) Verify scope from the access token against output from the ER phase. The method is "custom," requiring a stylesheet. Use any method to map the resource. AZ Select Allow Any Authenticated Client. You can select a different option if you wish to restrict an authenticated resource owner's access to a scope. Select Allow Any Authenticated Client. Select Contact OAuth STS.


Form-based authentication
Domain preparation
cert: folder.
Create an HTML form login policy
html in the search box under the "Control Panel" and select Add, as shown in Figure 4. 
ACME-LoginForm5030. This is the listing port for the submission. This matches the listening port on the MPGW or WTS that uses the AAA referencing this form login policy.Appliance. This indicates all the necessary HTML pages for supporting form-based login is stored on the appliance.
Create an AAA policy for form-based authentication support
AAA in the search box under the Control Panel and click Add as shown in Figure 6. 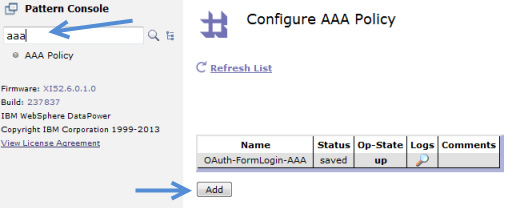
PlainFormLoginAAA
UnAuthPlainFormLoginAAA.Create the Multi-Protocol Gateway using AAA policies
MP-Form-Based.http://127.0.0.1:5001.HTTPS_5030.5030. This must match the port defined in the HTML Forms Login Policy that the AAA policies are referencing.MP-Form-Based-Policy.MP-Form-Based-Favicon-Rule and set Rule Direction to Client to Server (see Figure 8). This rule is handle favicon.ico to avoid processing the icon requests from the browser. It uses the following three actions:
/favicon.ico.var://service/mpgw/skip-backside = 1.
MP-Form-Based-Authenticate-RuleMatchAuthenticated. In the Main tab set the Match with PCRE to on. In the Matching Rule tab, add a URL match with the following regular expression (no spaces), /(getAccountBalance|j_security_check), as the match rule. Click Apply and Done to save the match action.
MP-Form-Based-LoginPage-RuleMatchLogin. In the Main tab, set the Match with PCRE to on. In the Matching Rule tab, add a URL match with the following regular expression (no spaces), /(Login|Error)Page\.htm(l)?(\?originalUrl=.*)?, as the match rule. Click Apply and Done to save the match action.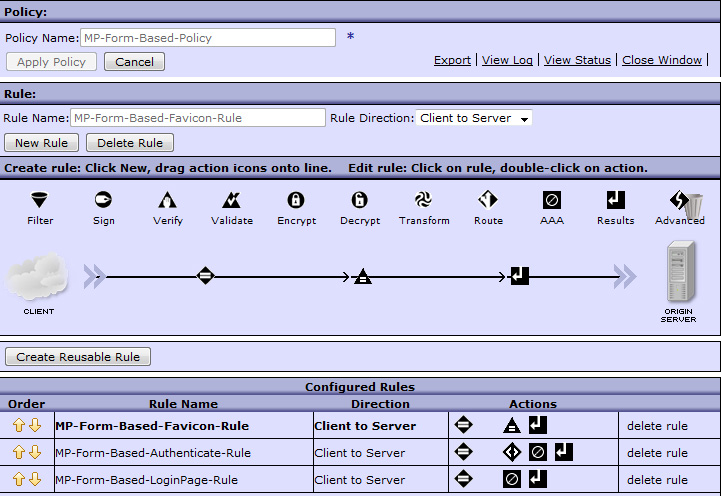
store:///AAAInfo.xml file in this sample. But, you can copy this file to local:///AAAInfo.xml and add your own users. You can reference LDAP or use any of the other authentication methods./getAccountBalance or /j_security_check. The getAccountBalance URL is the only one authenticated. No other URL is authenticated. In practice, there needs to be a default rule that catches "other URLs" and handles them.https://host:5030/getAccountBalance, where <host> is your DataPower application IP. Use "fred" and "smith" for the user name and password, respectively since these are defined in the default AAAInfo.xml file. The authentication succeeds and allow the AccountLoopback to reply with the account balance.Create the Web Token Service using the AAA policy
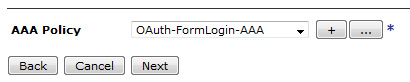
web token in the search box under the Control Panel. Select New Web Token Service. For Web Token Service Name, enter ACME-OAuth-AZSvr and click Next, as shown in Figure 9. 




Conclusion
Acknowledegements
Was this topic helpful?
Document Information
Modified date:
08 June 2021
UID
ibm11109463