Objective: identify whether there are resource profiles that have ACL entries where the permitted access level is equal to the UACC level set for that resource profile.
If you find any occurrences, most likely for the vast majority this situation is a result of bad RACF security administration. However, there are certain occasions where such a setting does make sense:
-
When for example, UACC=READ, group “SYSPROG” is permitted with “UPDATE”, and you want to make an exception for one of the “SYSPROG” group members by permitting “READ” access to the pertinent user ID.
-
Another valid exception that you might encounter is when UACC=NONE is set on a profile and yet, you discover permissions with access level “NONE”. This setting makes sense only for user IDs that have the OPERATIONS attribute, or users that that are connected with OPERATIONS to a group.
- The UACC<>NONE and you find user ID permissions with the same access level for user IDs that have the restricted attribute. Remember that restricted user IDs are not allowed to access resources based on the defined UACC level.
All other findings, where the permitted access is equal to the UACC, are most likely obsolete permissions. In that case, you must delete the pertinent permission, adjust the permitted access level, or change the defined UACC level.
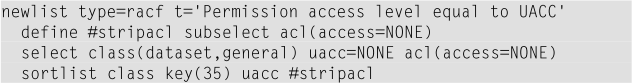
Here is an example CARLa program to find resource profiles with a UACC of “NONE” that also have ACL entries with access level “NONE” permitted:
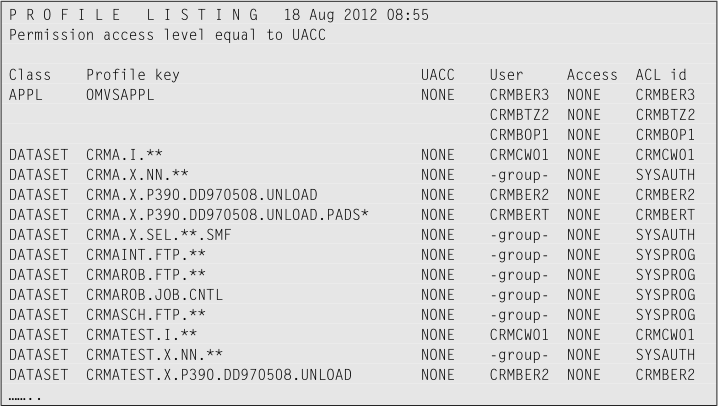
The output must look something like this screen capture:
Exercise:
-
Change the CARLa program to show the user IDs that are connected to the groups that are permitted on the ACL.
-
Now adjust the CARLa program to also find permissions with EXECUTE on profiles with UACC EXECUTE, and so on, for all access levels!
- Now instead of producing a report, automatically generate PERMIT DELETE commands. However, because the RACF command syntax differs for data set and general resource classes, generate only PERMIT DELETE commands for general resource class profiles.
View Suggested samples and answers
Continue with Finding accessible resources
© Copyright IBM Corp. 2012, 2020
IBM, the IBM logo and ibm.com are trademarks of International Business Machines Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at "Copyright and trademark information" at www.ibm.com/legal/copytrade.shtml.