Objective: find resource profiles where the universal access defined allows update or higher access.
In most modern day RACF shops, the auditors do not like to find any resource profiles where the UACC level set exceeds access level “READ”. Now attempt to report those resource profiles for which such a UACC setting applies on this system.

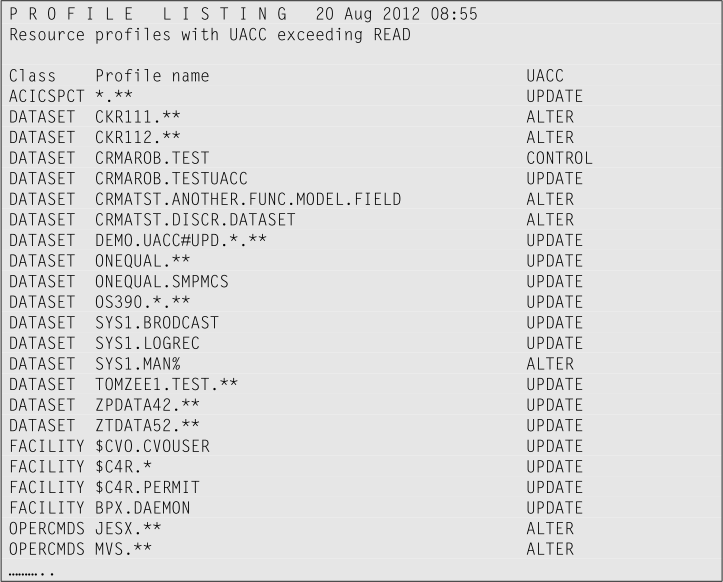
From the first output generated, you might learn that for some resource classes the UACC access level is used in a different way. In this case, these profiles must not be included in your report.
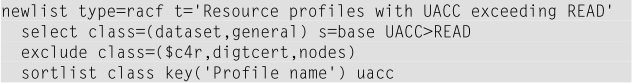
The output might now look like this screen capture:
However, many RACF shops use ID(*) as an alternative to using the UACC for allowing locally defined RACF user IDs access to a resource.
Now adjust the previous report to verify whether ID(*) is used and include those resource profiles where the permitted access level to ID(*) exceeds “READ”.
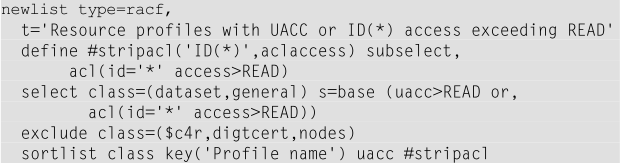
Note with the DEFINE #STRIPACL statement, you select only the ACL entry that is permitted to ID(*) with an access level higher than “READ”. In the SELECT statement, you must repeat that same clause. That clause avoids selecting any profiles that do not have a permission for ID(*) or the permitted access is less or equal to “READ”.
This screen capture is what the output might look like:
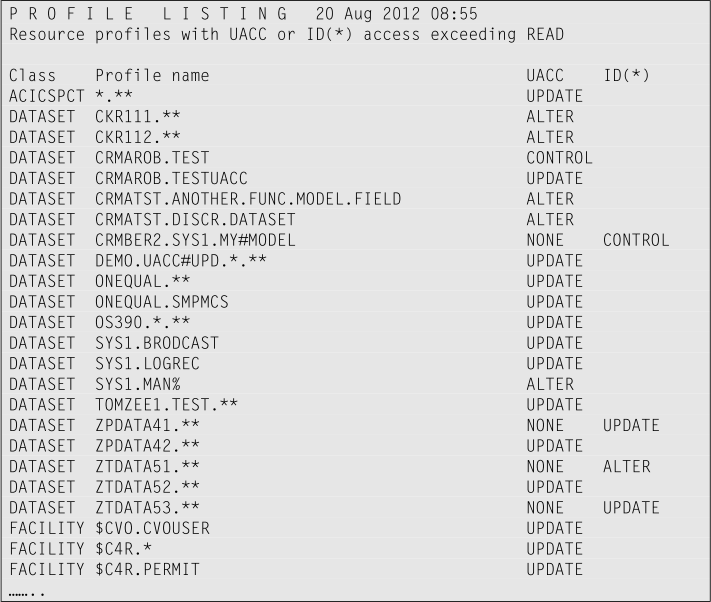
Continue with Finding permits same as UACC
© Copyright IBM Corp. 2012, 2020
IBM, the IBM logo and ibm.com are trademarks of International Business Machines Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at "Copyright and trademark information" at www.ibm.com/legal/copytrade.shtml.