Start your interactive tour now
Click the white prompts to discover how IBM Security® QRadar® EDR identifies and remediates a threat.
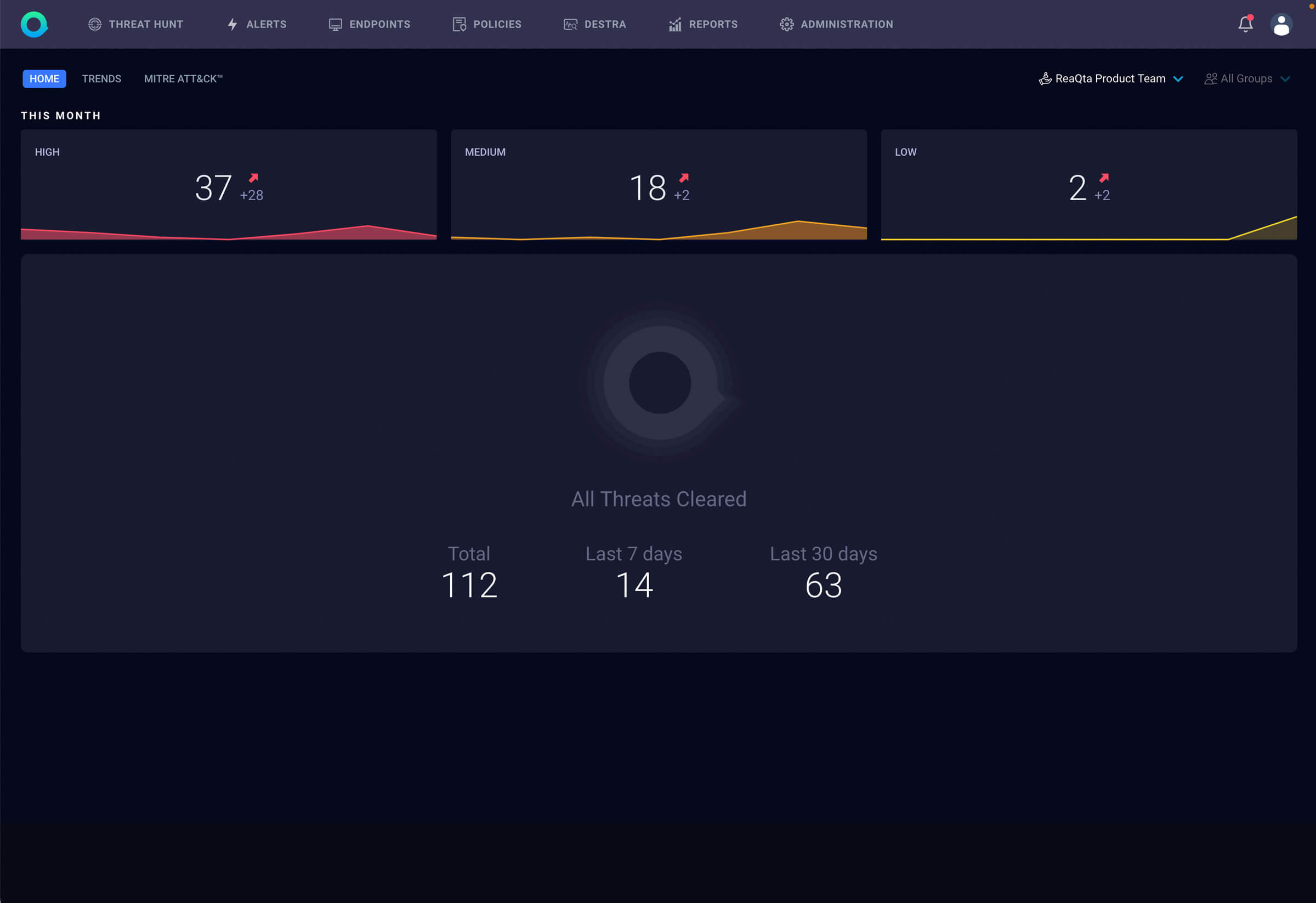
Endpoint detection and response (EDR) solutions are more important than ever, as endpoints remain the most exposed and exploited part of any network. The rise of malicious and automated cyber activity targeting endpoints leaves organizations struggling against attackers who easily exploit zero-day vulnerabilities with a barrage of ransomware attacks.
IBM QRadar EDR provides a more holistic EDR approach that:
Regain full control over all endpoint and threat activity with heightened visibility across your environment. Designed to be undetectable by adversaries, NanoOS technology provides deep visibility into the processes and applications running on endpoints.
Our continuously-learning AI detects and responds autonomously in near real time to previously unseen threats and helps even the most inexperienced analyst with guided remediation and automated alert handling.
Get ahead of attackers with easy-to-create detection and response use cases that return results in seconds, leaving dormant threats with no room to hide. Easy-to-build use cases are deployed across the organization without interrupting endpoint uptime.
All detections (low, medium, high severity) are investigated, analyzed and managed, without extra effort from the local security team.
Analysts will respond against active threats by way of termination and removal of malicious files or processes, creation of blocking policies or by isolating the endpoints.
Proactive threat hunting is powered by X-Force threat intelligence and done continuously by the QRadar EDR console, which searches for potential indicators of attack and compromise.
Assess your threat strategies, unite network security operations and response, improve your security posture and migrate to the cloud confidently.
Help security analysts improve their threat hunting skills and minimize the impact of a breach by preparing teams, processes and controls.
A global team of hackers hired to break into organizations and uncover risky vulnerabilities.