All supply chains are digital
Supply chains have been predominantly physical in nature. But today, digital technology plays a central role. Digitalization creates both efficiency benefits and new, underappreciated cybersecurity risks.
With dark web cybercrime marketplaces maturing rapidly, cyber adversaries are sharing resources in a booming cybercrime-as-a-service business—empowering threat actors to launch cyberattacks by preying on weak links in global supply chains. Hackers often target niche suppliers with fewer resources and more vulnerabilities for their supply chain attacks. In other words, the companies that make up the lion’s share of large supply chain networks.
Hundreds—even thousands—of third-party vendors are connected directly or indirectly, offering bad actors a myriad of paths and backdoors into critical systems. The resulting security breaches put revenue and brand reputations on the line. One study found that a data breach originating through a business partner costs nearly 12% more than other types of data breaches.
To better understand how cybersecurity factors are shaping the resilience of value chains, supply chains, and ecosystems, the IBM Institute for Business Value (IBM IBV) partnered with Microsoft to conduct a global survey of 2,000 cross-industry security and operations executives. The findings indicate a disturbing lack of attention to supply chain security. Only 30% of respondents prioritize a secure, connected ecosystem for their supply chain operations.
Our research also shows that those who view cyber risk and supply chain risk management as connected and intertwined see notably less disruption. Yet for too many organizations, siloed priorities and weak information security hygiene fuel negative outcomes, clouding visibility into potential threats and operational impact.
In this report, we explore three critical cyber risk management challenges that emerged from our research. We also present an opportunity for how to address each challenge with best-practice security measures and controls that can strengthen supply chain resilience.
Challenge: Digital supply chain operations—and third-party risks—are rapidly multiplying.Respondents report a massive web of direct and indirect suppliers, up to 6,400 total for nearly half or the organizations surveyed. Such a vast supplier network makes it difficult, if not impossible, for teams to anticipate potential security incidents stemming from third parties, let alone coordinate an effective response. Opportunity: A secure-by-design approach enhances both cyber and supply chain resilience.Organizations that integrate cyber risk and supply chain risk management cultivate a culture where supply chain cybersecurity is elevated in importance from initial design, to sourcing materials and suppliers, to distribution, to the end of the product lifecycle. And those that do it well are seeing better business outcomes. |
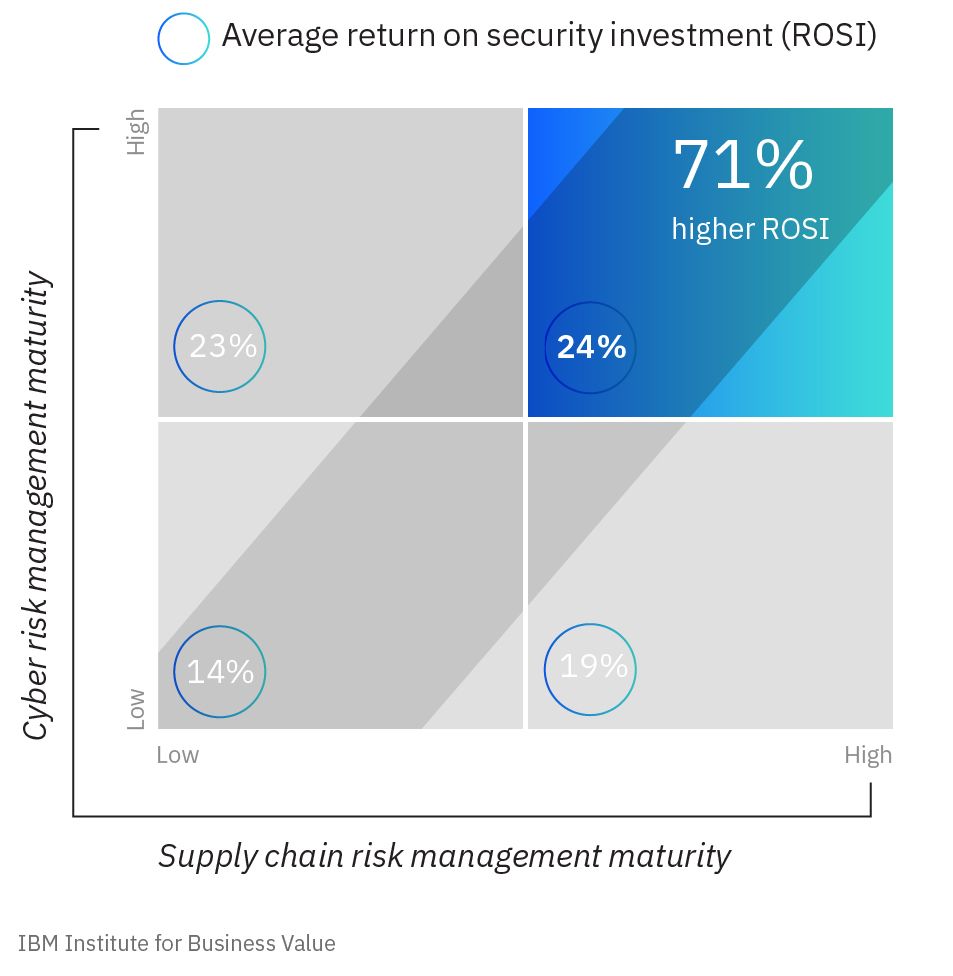
Integration pays off: Organizations with mature cyber risk and supply chain risk management capabilities see greater value from their security investments.
Challenge: Fragmented management blocks views into risks.Risk management lives in a house divided with responsibilities spread across the C-suite. But severe risks are typically cross-functional. Our data shows that organizations lack a holistic view that bridges accountability for risks across both physical and digital supply chains. Opportunity: Better internal visibility and coordination—backed by AI and automation—fuels external results.Respondents are turning to technologies such as cloud services, IoT, and AI to facilitate real-time communication, collaboration, governance, and data sharing. These critical capabilities can then transcend boundaries both internally and across the supplier base. |
Challenge: Many service provider partners come up short in security hygiene.When conducting risk assessments of suppliers, only around half of surveyed executives factor data and information security into their procurement process. And respondents indicate their direct and indirect suppliers exhibit low adoption of recommended security practices—practices that can prevent or limit the impact of software supply chain attacks. Opportunity: A strong, shared security culture across suppliers creates greater resilience for all.Transformation begins by ramping up the organization’s own adoption of software supply chain management best practices. Then leaders must make a point of investing in business partners committed to risk management and resilience. |
Download the report to explore these challenges and opportunities in more detail. A brief action guide for each opportunity provides specific steps leaders can take to initiate better integration of cyber risk and supply chain risk management across their organizations and ultimately their ecosystems.
Meet the authors
Kaivan Karimi, Mobility Partnerships, and Manufacturing & Mobility OT Security, MicrosoftFabio Campos, Managing Partner, Global Cyber Strategy & Risk Cybersecurity Services, IBM Consulting
Brett Drummond, Partner, Cybersecurity Services, IBM Consulting
Gerald Parham, Global Research Leader, Security and CIO, IBM Institute for Business Value
Originally published 24 May 2024


