How To
Summary
Windows event ID 5156 'The Windows Filtering Platform permitted a connection' can generate unnecessary EPS for some users as the event is generated each time a connection is allowed between an application or process with a TCP or UDP port. The number of events generated can vary depending on the configuration of the agent and some administrators might need to filter event ID 5156 to reduce noise caused by WinCollect activity.
Objective
Steps
Disabling successful connection events with an audit policy
Our recommended approach is to disable the successful connection Event IDs (5156) by issuing the following command from an administrative command prompt on the local machine:
auditpol /set /subcategory:”Filtering Platform Connection” /success:disable /failure:enable
Filtering event ID 5156 in WinCollect 7
In WinCollect 7, administrators can filter all event ID 5156 events from all applications or filter event ID 5156 events generated by wincollect.exe.
Option 1. To filter all event ID 5156 events
Administrators can add an exclusion filter to the log source for event ID 5156.
Note: Adding a global filter excludes all 5156 event IDs from being monitored by QRadar, including connections generated by other applications on the Windows host. If filtering all events is not an option, see Option 2. Use an XPath Query to selectively filter wincollect.exe events.
- Edit the log source used to monitor the Windows host.
- In the Security Log Filter Type field, select Exclusion Filter.
- In the Security Log Filter field, type 5156.
- Click Save.
- From the Admin tab, click Deploy Changes.
Results
After the deploy completes, the change is complete. For managed WinCollect agents, the log source is updated on the next polling interval. For stand-alone agents, the agentconfig.xml file is updated and filtering is applied.
Option 2. Use an XPath Query to selectively filter wincollect.exe events
In WinCollect 7.x, you can create a custom XPath query to eliminate event ID 5156 from being collected when the application is wincollect.exe. The XPath Query allows administrators to collect event ID 5156 from applications that need to be monitored for security purposes and exclude WinCollect agent activity.
Note: In a high EPS environment XPath queries can slow host performance. The Windows host is required to filter events at the source to complete the query and return the data to the WinCollect agent.
- In the Event Viewer, verify the path to wincollect.exe in event ID 5156.

Note: If you have more than one disk or special partitions configured, the Application Name path can differ from the example in this technical note. - Edit the log source the agent uses to monitor the Windows host.
-
In the XPath Query field, add the following query:
Note: The path to your WinCollect agent can differ based on the installation location for your WinCollect agent. The Data field in the XPath Query must match the path defined in the Application Name field of event ID 5156 for wincollect.exe.<QueryList> <Query Id="0" Path="Security"> <Select Path="Security">*</Select> <Suppress Path="Security">*[EventData[Data[@Name='Application'] and (Data='\device\harddiskvolume2\program files\ibm\wincollect\bin\wincollect.exe') ]]</Suppress> </Query> </QueryList> - Click Save.
- From the Admin tab, click Deploy Changes.
Results
After the deploy completes, the change is complete. For managed WinCollect agents, the log source is updated on the next polling interval. For stand-alone agents, the agentconfig.xml file is updated and filtering is applied.
Filtering event ID 5156 in WinCollct 10
Administrators who want to filter event ID 5156 on WinCollect 10 agents can edit the security log source and enable a filter to exclude events when the source application is wincollect.exe.
- Launch the IBM WinCollect 10 Console.
- Edit the log source for your security events.
- Click the Filter enabled check box.
- In the drop-down field, select WinCollect specific 5156 connection events filtered out.
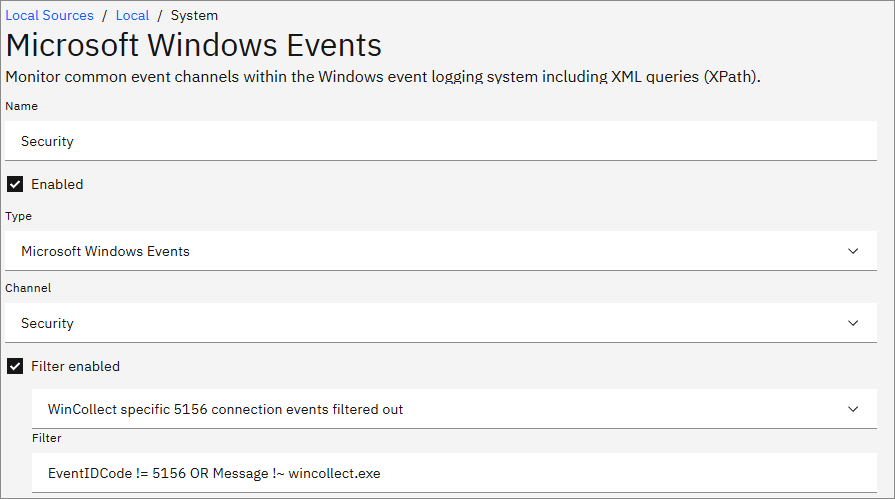
- Click Save.
- Click View pending change.
- Click Apply Changes to update the log source configuration.
ResultsThe WinCollect agent filters event ID 5156 events where the application name contains wincollect.exe. This allows administrators to filter for other applications in the security log where the Windows Filtering Platform permitted a connection that might need to be monitored.
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
09 May 2023
UID
ibm16857547