When there are 2 or more personal certificates on a WebSphere Control or Servant region keyring, the default personal certificate should be set to guarantee that the correct certificate is used for inbound SSL and outbound client authentication.
The default setup for a Network Deployment configuration will have a cell scoped SSL configuration "CellDefaultSSLSettings" used by the Deployment Manager, and a node scoped SSL configuration "NodeDefaultSSLSettings" used by the Node Agent and Application Servers. The steps illustrate how to set the default personal certificate for inbound SSL to the Deployment Manager and Application Server, and how to set the default personal certificate for outbound client authentication from the Application server.
1. Set the Default server certificate alias and Default client certificate alias to (none) for the SSL configuration
2. Set the default personal certificate for inbound SSL for the Deployment Manager.
3. Set the default personal certificate for inbound SSL for the Application Server.
4. Set the default personal certificate for outbound client certificate authentication for the Application Server.
WebSphere Application Server for z/OS allows you to set the default personal certificate on the SSL configuration panel or on the Manage Endpoint Security Configurations panel. The settings on the SSL Configuration panel apply to both the Control and Servant region. The Default server certificate alias and Default client certificate alias on the SSL Configuration panel should only be used if the personal certificate is installed on both the Control region and Servant region userid keyrings. For example, installing a SITE certificate on both the Control region userid keyring and Servant region userid keyring. Attempting to set a Default server certificate alias or Default client certificate alias on an SSL configuration when the personal certificate exists on only one (either Control or Servant region) keyring can result in errors when the other region's address space (Control or Servant region) attempts to find that personal certificate label and it does not exist on its keyring.
It is recommended that the default personal certificate be set on the Manage Endpoint Security Configurations panel, since a typical WebSphere for z/OS cell will have unique personal certificates on either the Control or Servant region keyring, but not both.
The steps describe how to set up a default personal certificate on the Manage Endpoint Security Configurations panel.
1. Set the Default server certificate alias and Default client certificate alias to none for the SSL configuration
a. On the administrative console
SSL certificate and key management > SSL configurations > CellDefaultSSLSettings
Default server certificate alias = none
Default client certificate alias = none
SSL certificate and key management > SSL configurations > NodeDefaultSSLSettings
Default server certificate alias = none
Default client certificate alias = none
2. Set the default personal certificate for inbound SSL to the Deployment Manager.
a. Identify the list of personal certificates on the Control region keyring.
RACDCERT LISTRING(WASKeyring2048) ID(DMCR1)
Where WASkeyring2048 is the keyring defined for the Deployment Manager control region userid (DMCR1).
Digital ring information for user DMCR1:
Ring:
>WASKeyring2048<
Certificate Label Name Cert Owner USAGE DEFAULT
-------------------------------- ------------ -------- -------
WebSphereCA2048 CERTAUTH CERTAUTH NO
PersonalCert1 ID(DMCR1) PERSONAL NO
PersonalCert2 ID(DMCR1) PERSONAL NO
b. On the administrative console
SSL certificate and key management > Manage endpoint security configurations
Select the cell scoped SSL configuration "CellDefaultSSLSettings" under the Inbound topology tree.
c. Select the personal certificate (PersonalCert1) to be used as the default personal certificate.
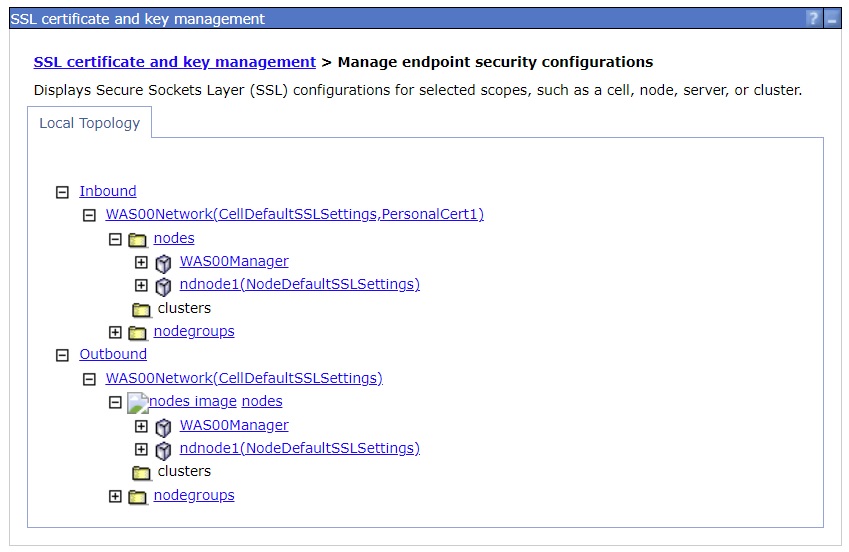
d. Confirm the personal certificate (PersonalCert1) is set as the default.
On the administrative console
SSL certificate and key management > Manage endpoint security configurations
The default certificate (PersonalCert1) used for inbound SSL for the Deployment Manager will be shown after the SSL configuration CellDefaultSSLSettings.
3. Set the default personal certificate for inbound SSL for the Application Server.
a. Identify the list of personal certificates on the Control region keyring.
RACDCERT LISTRING(WASKeyring2048) ID(ASCR1)
Where WASkeyring2048 is the keyring defined for the Application Server control region userid (ASCR1).
Digital ring information for user ASCR1:
Ring:
>WASKeyring2048<
Certificate Label Name Cert Owner USAGE DEFAULT
-------------------------------- ------------ -------- -------
WebSphereCA2048 CERTAUTH CERTAUTH NO
PersonalCert3 ID(ASCR1) PERSONAL NO
PersonalCert4 ID(ASCR1) PERSONAL NO
b. On the administrative console
SSL certificate and key management > Manage endpoint security configurations
Select the cell scoped SSL configuration "NodeDefaultSSLSettings" under the inbound topology tree.
c. Select the personal certificate (PersonalCert3) to be used as the default personal certificate.
d. Confirm the personal certificate (PersonalCert3) is set as the default.
On the administrative console
SSL certificate and key management > Manage endpoint security configurations
The default certificate (PersonalCert3) used for inbound SSL for the Node will be shown after the SSL configuration NodeDefaultSSLSettings.
4. Set the default personal certificate for outbound client certificate authentication for the Application Server.
a. Identify the list of personal certificates on the Servant region keyring.
RACDCERT LISTRING(WASKeyring2048) ID(ASSR1)
Where WASkeyring2048 is the keyring defined for the Application Server servant region userid (ASSR1).
Ring:
>WASKeyring2048<
Certificate Label Name Cert Owner USAGE DEFAULT
-------------------------------- ------------ -------- -------
PersonalCert5 ID(ASSR1) PERSONAL NO
PersonalCert6 ID(ASSR1) PERSONAL NO
WebSphereCA2048 CERTAUTH CERTAUTH NO
b. On the administrative console
SSL certificate and key management > Manage endpoint security configurations
Select the cell scoped SSL configuration "NodeDefaultSSLSettings" under the outbound topology tree.
c. Select the personal certificate (PersonalCert6) to be used as the default personal certificate.

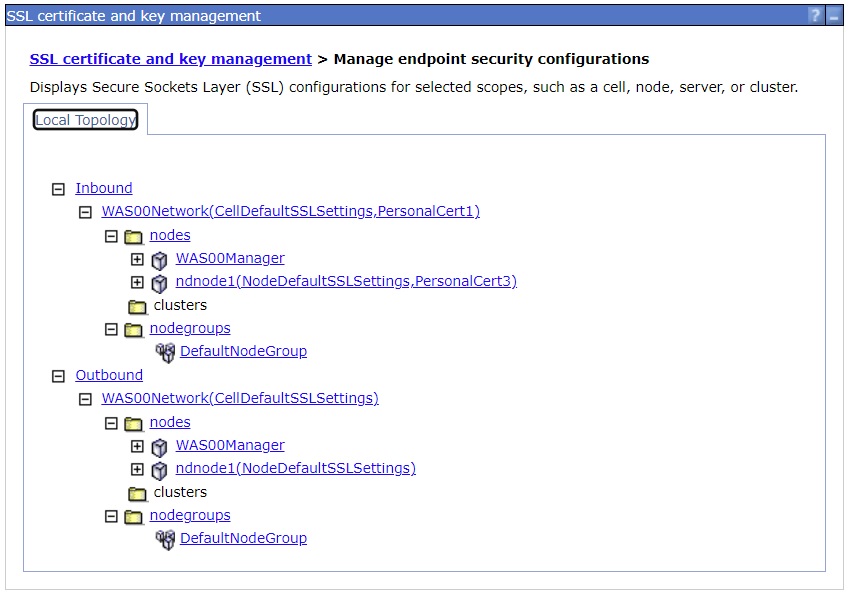
d. Confirm the personal certificate (
PersonalCert6) is set as the default.
On the administrative console
SSL certificate and key management > Manage endpoint security configurations
The default certificate (PersonalCert6) used for outbound SSL for the Node will be shown after the SSL configuration NodeDefaultSSLSettings.
The Manage Endpoint Security Configurations shows:
- PersonalCert1 as the default personal certificate for Inbound SSL to the Deployment Manager
- PersonalCert3 as the default personal certificate for Inbound SSL to the ApplicationServer
- PersonalCert6 as the default personal certificate for Outbound client authentication from the Application Server
The Inbound topology tree represents inbound SSL connections to a Deployment Manager and Application server control region. The Outbound topology tree represents outbound SSL connections from the Deployment Manager and Application server Servant region.
The DEFAULT column which specifies that the certificate is the default certificate for a keyring has no affect in Java.
[{"Type":"MASTER","Line of Business":{"code":"LOB45","label":"Automation"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SS7K4U","label":"WebSphere Application Server for z\/OS"},"ARM Category":[{"code":"a8m50000000CcyMAAS","label":"WebSphere Application Server traditional-All Platforms-\u003ESecurity-\u003ESSL"}],"ARM Case Number":"","Platform":[{"code":"PF035","label":"z\/OS"}],"Version":"All Versions"}]







 d. Confirm the personal certificate (PersonalCert6) is set as the default.
d. Confirm the personal certificate (PersonalCert6) is set as the default.