News
Abstract
Administrators with QRadar Risk Manager appliances in their deployment are being alerted to changes in Configuration Source Manager due to the approaching end of life of Adobe Flash. Due to removal of Adobe Flash, the Configuration Source Management (CSM) functionality is integrated in to the Configuration Monitor. The updated Configuration Monitor interface is available to administrators who upgrade their QRadar deployment in upcoming fix pack releases.
Content
QRadar Risk Manager administrators are being alerted to an upcoming user interface change to the Configuration Source Management (CSM) component. Due to the End of Life (EOL) announcement for Adobe Flash, QRadar Risk Manager has deprecated the default Configuration Source Management interface and integrated device backup and configuration functionality in to the Configuration Monitor. The Configuration Monitor interface includes the same device backup functionality, but was developed without Adobe Flash to ensure that administrators can comply with Adobe's 31 December 2020 end of life announcement. Administrators who are in corporate environments who are required to remove Adobe Flash can discuss upgrades to a QRadar version that includes the updates to the Configuration Monitor. All created schedules (Scheduled Discovery, jobs) are automatically moved from the legacy Admin tab Configuration Source Management interface to the Configuration Monitor on the Risks tab after you upgrade.
Product versions
- QRadar Risk Manager 7.4.1 fix pack 1 and later
- QRadar Risk Manager 7.3.3 fix pack 5 and later
How to identify the issue

Figure 1: Legacy Configuration Source Management user interface for Adobe Flash.

Figure 2: Browsers which block Adobe Flash by default do not display the Configuration Source Management user interface.
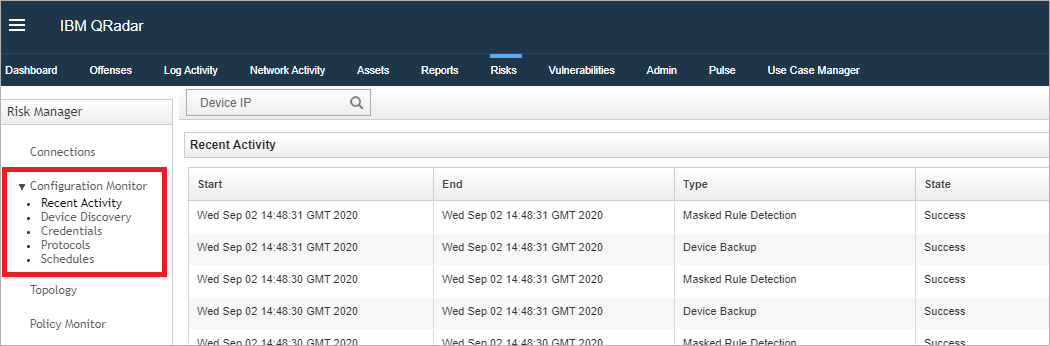
Locating the Configuration Monitor
Procedure
- Log in to QRadar.
- Click the Risks tab.
Schedules and device backups
Schedules Configuration for QRadar Risk Manager allows administrators to define backup jobs or device discovery in the Configuration Monitor. Schedules are now setup using the Configuration Monitor. Devices can be added to the schedule and a trigger defines the time and recurrence for the backup or device discovery, which can occur either once, daily, weekly, monthly, or defined as a cron job expression.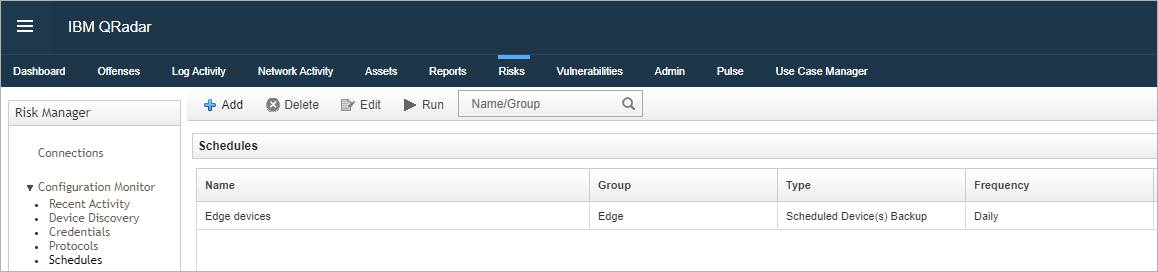 Figure 4: Schedules are now defined in the Configuration Monitor for the Risk Manager versions defined in this technical note.
Figure 4: Schedules are now defined in the Configuration Monitor for the Risk Manager versions defined in this technical note.
- Click the Risks tab.
- Expand the Configuration Monitor and select Schedules.
- On the Scheduled page, click Add to create a new schedule or select and existing schedule and click Edit.
- Type a unique Name for the schedule.
- Select a Group from the drop-down list or type a new Group name.
- Select a schedule type:
Note: If a discovery schedule exists, you must select Backup. You cannot change the Type of an existing schedule.Select a schedule type to either backup or discover new devices Option Description Backup Backup schedules allow users to collect device configuration changes from discovered network devices. Discovery Updates the telemetry (neighbor) information for devices and adds newly discovered network devices. - If you are creating a discovery schedule and want to add newly discovered devices to a product, select Crawl.
- If you are creating a backup schedule, click Edit and add or remove devices to be targeted for backup. Then perform one of the following actions
- Use the arrows to move devices from the Available Devices list to the Selected Devices list.
- Select Search to configure a search to dynamically target devices based on IP address, operating system, model, or hostname.
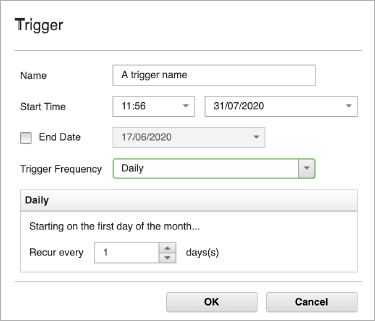
Tip: You can search for Admin or Interface IP addresses with a comma-separated list of IP addresses or CIDR ranges. - Select a Trigger to specify the frequency you want the schedule to run.
- Once
- Daily
- Weekly
- Monthly
- Cron
Note: Cron expressions that repeat more than once per hour are not accepted.
- Click Save.
Device discovery
Device Discovery is now located in the Configuration Monitor on the Risks tab for the QRadar Risk Manager versions discussed in this technical note. Device Discovery streamlines adding network devices through network management appliances, such as Check Point Management Servers, Palo Alto Panorama, Juniper NSM, or by crawling the network with SNMP for discoverable IP addresses. The Device Discovery functions in QRadar Risk Manager allow users to set up multiple networks and run discovery to automatically add new firewalls, IPS, and other network devices so they can be backed up and added to the Topology. It is important that administrators do not add overlapping address ranges or CIDR addresses when discovering devices to prevent duplicates. Figure 5: Device Discovery in the Configuration Monitor displays the status or logs for added devices.
Figure 5: Device Discovery in the Configuration Monitor displays the status or logs for added devices.
Credentials
Device credentials can be added to access and download the configuration of devices such as firewalls, routers, switches, or IPSs in the Configuration Monitor on the Risks tab. Administrators can add credentials for individual devices or for multiple network devices that use the same credentials and prioritize the credential order QRadar Risk Manager uses to back up network device configurations.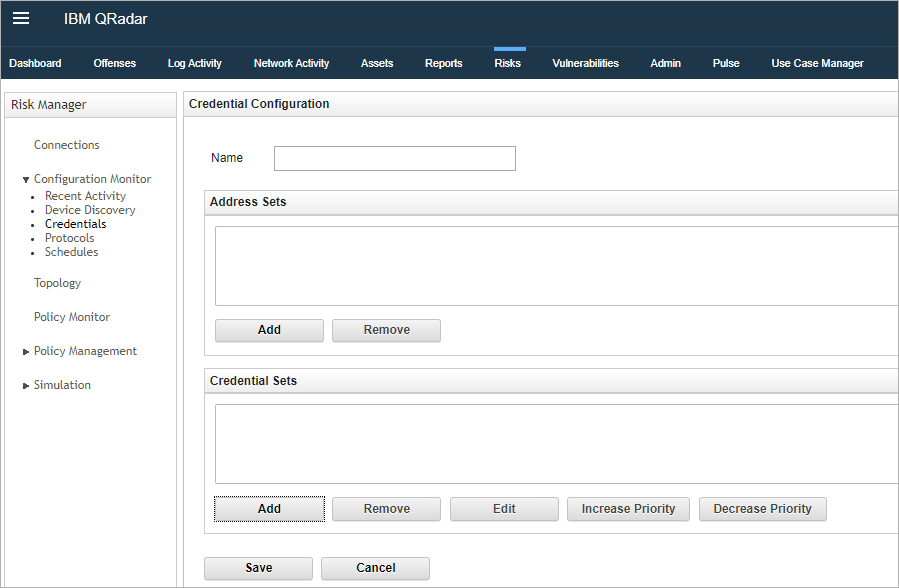
Figure 6: Device credentials can be added in the Configuration Monitor.
Configuring protocols
Procedure
- On the Risk tab, click Configuration Monitor.
- In the navigation menu, click Protocols.
- Select Add from the toolbar.
- Type a Name for the protocol set.
- In the Address Sets section, click Add.
- In the Add Address field, type the IP address or CIDR range that you want to apply to the network group, then click OK.
Tip: You can use IP4 or IP6 address or CIDR ranges. - Select the check box for each protocol you want to enable.
Tip: Select a protocol and click Increase Priority or Decrease Priority to adjust the order you want the protocols to be used. - Select a protocol to configure its relevant properties. You can configure the following values for the protocol parameters:
Table 1. Protocol parameters Protocol Parameter description SSH Configure the following parameters:
- Port- Type the port on which you want the SSH protocol to use when communicating with and backing up network devices. The default SSH protocol port is 22.
- Version- Select the version of SSH that you want this network group to use when communicating with network devices. The available options are as follows:
- Auto- This option automatically detects the SSH version to use when communicating with network devices.
1 - Use SSH-1 when communicating with network devices.
2 - Use SSH-2 when communicating with network devices.
Telnet Type the port number you want the Telnet protocol to use when communicating with and backing up network devices. The default Telnet protocol port is 23.
HTTPS Type the port number you want the HTTPS protocol to use when communicating with and backing up network devices. The default HTTPS protocol port is 443
HTTP Type the port number you want the HTTP protocol to use when communicating with and backing up network devices. The default HTTP protocol port is 80. SCP Type the port number you want the SCP protocol to use when communicating with and backing up network devices. The default SCP protocol port is 22.SFTP Type the port number you want the SFTP protocol to use when communicating with and backing up network devices. The default SFTP protocol port is 22. FTP Type the port number you want the FTP protocol to use when communicating with and backing up network devices. The default SFTP protocol port is 22. TFTP The TFTP protocol does not have any configurable options. SNMP Configure the following parameters:
- Port - Type the port number you want the SNMP protocol to use when communicate with and backing up network devices.
- Timeout(ms) - Select the amount of time, in milliseconds, that you want to use to determine a communication timeout.
- Retries - Select the number of times you want to attempt to retry communications to a device.
- Version - Select the version of SNMP you want to use for communications. The options are v1, v2, or v3.
- V3 Authentication - Select the algorithm you want to use to authenticate SNMP traps.
- V3 Encryption - Select the protocol you want to use to decrypt SNMP traps.
- Click Save.
Tip: After you create your protocol sets, select a protocol set and click Increase Priority or Decrease Priority to adjust the order you want the protocol sets to be checked.
Was this topic helpful?
Document Information
Modified date:
08 October 2020
UID
ibm16326009