Troubleshooting
Problem
Log source integrations with certificates like TLS or HTTPS fail with checkCertificatePinning failed errors in /var/log/qradar.log.
Diagnosing The Problem
Run the following command to find the Certificate Pinning error messages in the logs:
grep 'checkCertificatePinning failed' /var/log/qradar.log
Output example::
[Akamai Kona REST API Protocol Provider Thread: class com.q1labs.semsources.sources.akamaikonarestapi.AkamaiKonaRESTAPIProvider44225] com.q1labs.frameworks.crypto.trustmanager.CertificateValidator:
[ERROR] [NOT:0000003000][x.x.x.x./- -] [-/- -]checkCertificatePinning failed.
Another error message sample:
[INFO] Audit logging msg:(ecs-ec-ingress) Server Certificate Validation failed. chain:
[0]X509Certificate : { SubjectDN : CN=sample.com, O="sample.com, inc.", L=Sample, ST=Sample, C=Sample, IssuerDN : CN=DigiCert TLS RSA SHA256 2020 CA1, O=DigiCert Inc, C=US},[1]X509Certificate : { SubjectDN : CN=DigiCert TLS RSA SHA256 2020 CA1, O=DigiCert Inc, C=US, IssuerDN : CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCertInc, C=US},
exception:com.q1labs.frameworks.crypto.trustmanager.exceptions.Q1CertificateException:
checkCertificatePinning failed.
Resolving The Problem
Find next two guides to pull the certificates, use the one that best fits your scenario:
How to pull only the server certificate.
This process uses the QRadar script called getcert.sh.
- SSH to QRadar as the root user.
- Optional: If you are using as the Target Event Collector a different host than the console, SSH to that host.
- Run the following command to obtain server certificate. This command pulls the server cert, it gives it a name with the format endpoint_port.crt. and place it in /opt/qradar/conf/trusted_certificates:
Command example:/opt/qradar/bin/getcert.sh <Source Endpoint>
Example of the command output:/opt/qradar/bin/getcert.sh sqs.us-west-2.amazonaws.com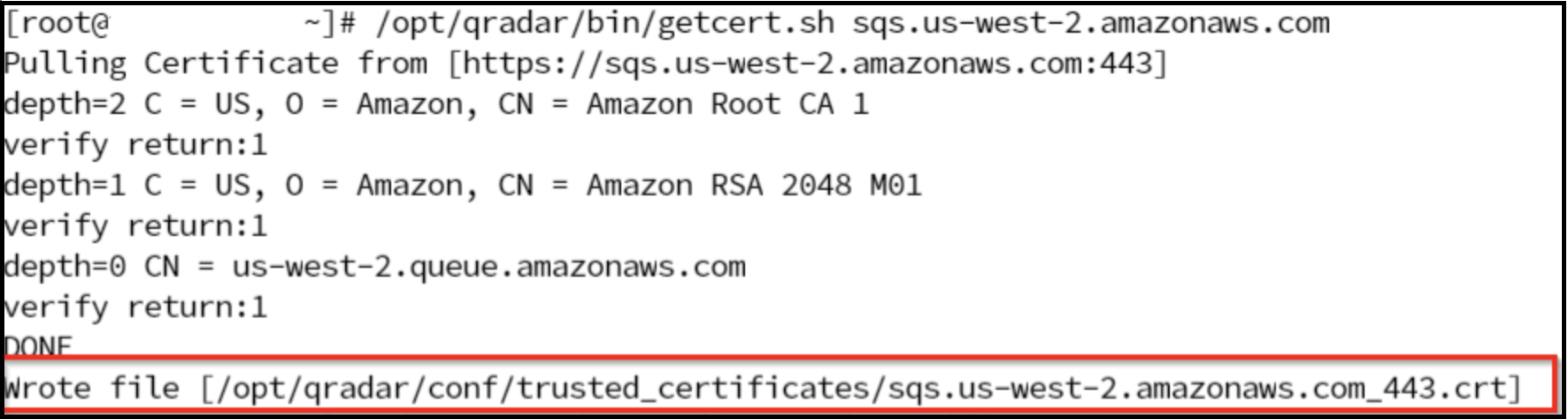
- Run the following command to verify that the new certificate is placed into /opt/qradar/conf/trusted_certificates:
ls -la /opt/qradar/conf/trusted_certificates - Reload the certificates, run the following command to restart ecs-ec-ingress service, the restart reloads the certificates:
Note: For more information about the impact of restarting the ecs-ec-ingress process, check the following link : QRadar: Core services and the impact of restarting services.systemctl restart ecs-ec-ingress
Result:
The certificate is pulled and placed in /opt/qradar/conf/trusted_certificates.
How to pull the full certificate chain.
This process uses the openssl command to get full certificate chain.
- SSH to QRadar as the root user.
- Optional: If you are using as the Target Event Collector a different host than the console, SSH to that host.
- Run the following command to go to the trusted_certificate directory
cd /opt/qradar/conf/trusted_certificates/ - Create a file named script.txt.
- Copy the following text into the file named script.txt. Replace <ServerFQDN> with the fully qualified domain name and <PORT> with the port number. The full command goes from 'openssl' until 'done':
openssl s_client -showcerts -verify 5 -connect <serverFQDN>:<PORT> < /dev/null | awk '/BEGIN CERTIFICATE/,/END CERTIFICATE/{ if(/BEGIN CERTIFICATE/){a++}; out="cert"a".pem"; print >out}' ## Command two for cert in *.pem; do newname=$(openssl x509 -noout -subject -in $cert | sed -nE 's/.*CN ?= ?(.*)/\1/; s/[ ,.*]/_/g; s/__/_/g; s/_-_/-/; s/^_//g;p' | tr '[:upper:]' '[:lower:]').pem echo "${newname}"; mv "${cert}" "${newname}" done - Run the following command to provide execute permissions to the script.txt file:
chmod a+x script.txt - Execute the script with the following command:
./script.txt - List the files on trusted_certificates directory and confirm the new pulled certificates were successfully created:
ls -la /opt/qradar/conf/trusted_certificates/
All the certs are saved with a .pem extension, for example: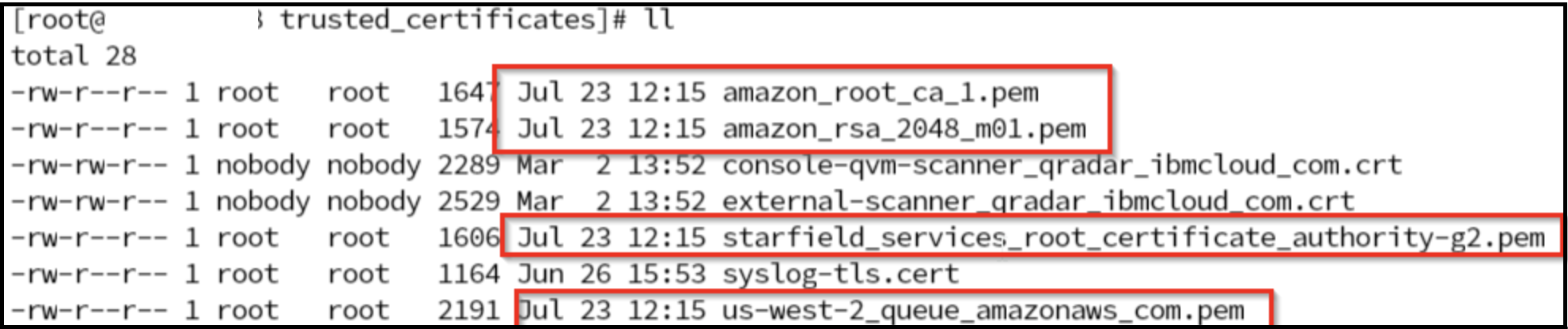
- If the certs are in place, restart ecs-ec-ingress service on the target event collector to reload certificates into configuration:
Note: For more information about the impact of restarting the ecs-ec-ingress process, check the following link : QRadar: Core services and the impact of restarting services.systemctl restart ecs-ec-ingress
Result:
The full chain of certificates are pulled and placed on the /opt/qradar/conf/trusted_certificate path.
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB24","label":"Security Software"},"Business Unit":{"code":"BU048","label":"IBM Software"},"Product":{"code":"SSBQAC","label":"IBM Security QRadar SIEM"},"ARM Category":[{"code":"a8m0z000000cwt0AAA","label":"Log Source"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions"}]
Was this topic helpful?
Document Information
Modified date:
23 July 2024
UID
ibm17157276