I am getting asked more about security these days. Perhaps there is renewed focus on this area as we hear about hacker groups taking information from organisations and companies in the News every day. This article was the response to a recent email question on what AIX offers on the security side, spotting vital files being changed and what parts of PowerSC to use for quick wins.
For AIX security, the three "big hitters" for "out of the box" AIX hardening are:
1) Remove the "telnet" and "ftp" commands
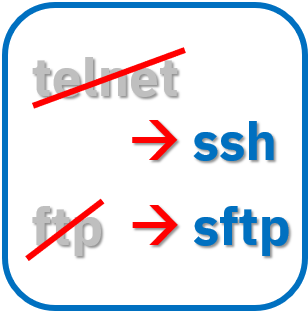
Ban the use of telnet, AIX tn, and ftp commands. The problem with these commands is fairly obvious as any computer room that uses them has no security at all from network packet sniffers! I learned about the risks of these two commands, when 5 years ago. I tried the Open Source Ethereal software and suddenly thought "Hang on you can see all the ftp and telnet password with no effort at all!" Network administrators need to monitor for the use of these protocols and set alarm bells ringing on each packet. Instead of these old command, use secure ftp (sftp) and Secure Shell (ssh). The ssh command is installed with AIX as default for many years.
The latest AIX 7.2 allows you to remove the AIX package that includes these two commands.
2) The "aixpert" AIX command

The aixpert command is a regular AIX tool that uses a policy file to automatically locks down AIX. It has various rule sets like low, medium, high, and SOX/Corbit. More rule sets have been added since this article was written. The policy has well over a hundred rules and tools that it runs in all the regular areas like: password aging and lockout on failed log-ins, SUID bit programs, disabling services, blocking port scanning, and many more features. The high setting needs care or you might never get to log back in. Before using aoxpert's high setting, change the root password or it might immediately decide the root user password is too old and block the root user account. It is best to try aixpert on a test machine. You can practice disabling security rules for thing you do need to use. For example, I had to enable DNS server and NFS for my webserver as it provides these functions too. Enabling involves commenting out the rules that you do not want to be applied. This same command is used to get a report of violations to the policy. Once you have sane set of rules, you can roll out the policy across many machines and run one command for a consistent hardening. Using aixpert is like getting the IBM AIX Security team with decades of experience working for you with regular rule improvements (with AIX upgrades). Using aixpert is the only way to cope with large teams of expert hackers.
See my video for get you started information at http://www.youtube.com/watch?v=L1MmuZOntxI
3) Roll based Access Control
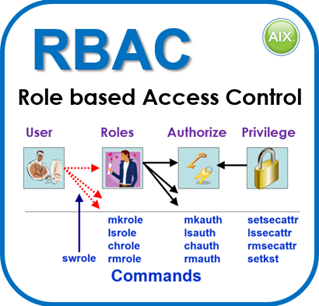
Roll based Access Control (RBAC) was built in to the first AIX 6 release and enhanced over later releases. RBAC is used to stop people logging in as root or super-user for simple tasks. RBAC allows handing-off specific tasks on specific resources to lesser user accounts. RBAC drastically limits the damage that the root user can make by simple mistakes.
See my video for get you started information at http://www.youtube.com/watch?v=CvylFrQX93U Note: this video was made before specific resource control was added.
4) PowerSC Express Real-Time Alerts

PowerSC Express Real-Time Compliance (RTC) alerts is an extra package to monitor vital files and emails specific users or cuases SNMP traps when specific files are changed or their RWX permissions change. You can add your own critical files to the list. For example, the famous init.ora file for Oracle settings. RTC functions are handled by direct kernel notifications so we are talking subsecond times to raise alerts not polling or daily cron scripts. RTC means you catch the mistake or even find out you are being hacked, while it happens so you can react quickly.
See my video for get you started information at http://www.youtube.com/watch?v=5OFELpnzeFA
AIX RTC (part of PowerSC) is quick to understand, implement, and get the benefit. I estimate 30 minutes at most. Then, roll it out across all your AIX servers.
The IBM PowerSC (security and Compliance) package offers other large security tools. The tools are powerful weapons but some take time to learn and implement fully.

Other quick wins from PowerSC are:
- 5) PowerSC Trusted Firewall
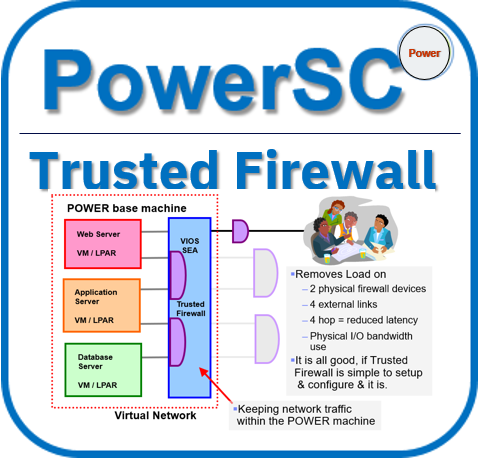
PowerSC Trusted Firewall (short-cut) is mostly a performance boost item on the virtual networks. Trusted Firewall can:
- Save money as external Firewall devices receive less network traffic and uses less bandwidth, so less expensive devices can be deployed.
- Boost network performance by drastically reduce network latency.
See my video for get you started information at http://www.youtube.com/watch?v=5PT2Ggwu0lg
- 6) PowerSC Trusted Logging
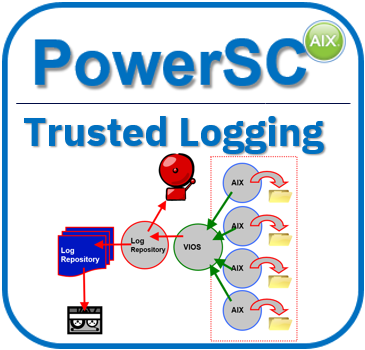
If you don't already remotely ship your AIX logs to a log archive, then this feature ships the logs to your Virtual I/O Servers. Any excellent first step to block hackers modifying log files to hid their tracks. Trusted Logging is easy to set up as it uses your vSCSI VIOS client to VIOS connection over memory. You now have the information that allows a postmortem analysis of "what just happened!"
See my video for get you started information at http://www.youtube.com/watch?v=fQ8hE1NH8CY
- 7) PowerSC Compliance Automation

PowerSC Compliance Automation automates and adds extra aixpert style profiles to cover further industry standards. It allows Systems Director to roll out the policies and produce reports on many 100's of machines.
For more information, read the PowerSC Redbook chapter 3 http://www.redbooks.ibm.com/abstracts/sg248082.html

I hope this article:
- Adds a few extra tools for your war against the hackers.
- Spurs you into action to get started and to understand these basics tools, which are quick to implement.
- Informs you that security help and tools are available.
- IBM has many experts working hard for you and don't forget you can engage IBM Lab Services and IBM Business Partners to quickly get you started.
Good hunting and crushing those nasty hackers!









