Question & Answer
Question
How to modify, mask or remove parameters and header fields using the API Connect Redact policy and gateway scripts
Answer
Author: Werner Tod
Reviewer: Sila Kissuu
Customers often need to properly handle sensitive data in requests processed by API Connect.
This data (e.g. user ids and passwords) can reside in request parameters as well as header fields.
The referenced sample API yaml file demonstrates the use of the DataPower Redact policy, as well as the modification of header fields using gateway scripts in the API.
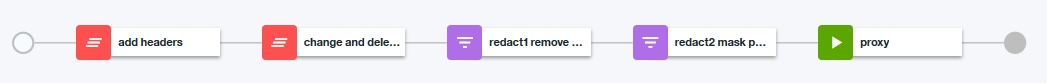
The API flow looks as follows:
Link to yaml file:
Test_Redact_1.0.0.yaml_.txt
Description of the flow components:
'add headers': this gateway script adds two header fields to the incoming request. One of them will later be changed (X-a-header-i-want-to-add) and one will be deleted (X-another-header-i-want-to-add).
'change and delete headers': in this gateway script X-another-header-i-want-to-add gets deleted; X-a-header-i-want-to-add gets changed.
'redact1 remove parameter': this policy call to Redact removes the sample parameter myParam1 that is defined for the API.
'redact2 mask parameter': this policy call to Redact masks the sample parameter myParam2.
NOTE: Events stored in the API Connect Analytics are not redacted and remain visible. Data is only redacted during processing of the request and logging.
If you need to protect sensitive data in the Analytics context 4 options are available:
(1) Enable access to analytics data in the API Connect user interfaces. This is the default setting for each API Connect event type. Anyone with access to the Analytics UI also has access to the request data.
(2) Disable access to analytics data in API Connect and instead re-route the data streams to one or more third-party systems.
When you select this method the data is not written to API Connect analytics.
(3) Enable access to analytics data in API Connect and simultaneously stream the data to one or more third-party systems.
(4) Completely disable access to analytics data.
IMPORTANT: disabling access to analytics data is a global setting so it applies to all provider and developer organizations in the entire API Connect cloud.
Establishing a separate analytics data server allows one to define separate access controls that can be more restrictive than default access settings in the Analytics UIs. Additional filtering or encryption can also be applied there, depending on the chosen data server solution.
There is one more thing that you can do to prevent logging of API calls:
you can put an Activity Log at the end of the assembly and in there set Content and Content on error to none:
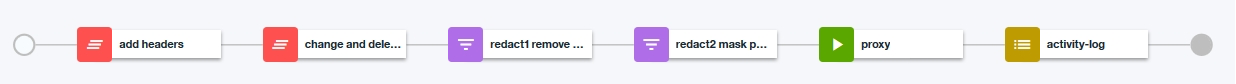
This way, API calls from outside the APIC consoles will not be logged in the Analytics log at all.
Please note that calls made from the internal APIC test client will still be logged.
Link to the extended yaml file:
Test_Redact_1.0.0_new.yaml_.txt
There is one of the out-of-the-box feature of API Connect that is extremely useful when trying to mask or remove authentication-related sensitive data from incoming requests. The header field Authorization gets sanitized/masked by default. Thus it can be used as a container for sensitive information that must not be logged in clear text. The following sample API demonstrates how you can use the default sanitization of API Connect for the Authorization header field to sanitize client id client secret or basic authentication credentials. In the sample we include the code to move either client id and client secret or basic authentication to the Authorization field. Just comment out the corresponding lines of code in the gateway script setauthheader as needed.
Link to the yaml file:
testsanclientauth_1.0.0.yaml_.txt
Reviewer: Sila Kissuu
Customers often need to properly handle sensitive data in requests processed by API Connect.
This data (e.g. user ids and passwords) can reside in request parameters as well as header fields.
The referenced sample API yaml file demonstrates the use of the DataPower Redact policy, as well as the modification of header fields using gateway scripts in the API.
The API flow looks as follows:

Link to yaml file:
Test_Redact_1.0.0.yaml_.txt
Description of the flow components:
'add headers': this gateway script adds two header fields to the incoming request. One of them will later be changed (X-a-header-i-want-to-add) and one will be deleted (X-another-header-i-want-to-add).
'change and delete headers': in this gateway script X-another-header-i-want-to-add gets deleted; X-a-header-i-want-to-add gets changed.
'redact1 remove parameter': this policy call to Redact removes the sample parameter myParam1 that is defined for the API.
'redact2 mask parameter': this policy call to Redact masks the sample parameter myParam2.
NOTE: Events stored in the API Connect Analytics are not redacted and remain visible. Data is only redacted during processing of the request and logging.
If you need to protect sensitive data in the Analytics context 4 options are available:
(1) Enable access to analytics data in the API Connect user interfaces. This is the default setting for each API Connect event type. Anyone with access to the Analytics UI also has access to the request data.
(2) Disable access to analytics data in API Connect and instead re-route the data streams to one or more third-party systems.
When you select this method the data is not written to API Connect analytics.
(3) Enable access to analytics data in API Connect and simultaneously stream the data to one or more third-party systems.
(4) Completely disable access to analytics data.
IMPORTANT: disabling access to analytics data is a global setting so it applies to all provider and developer organizations in the entire API Connect cloud.
Establishing a separate analytics data server allows one to define separate access controls that can be more restrictive than default access settings in the Analytics UIs. Additional filtering or encryption can also be applied there, depending on the chosen data server solution.
There is one more thing that you can do to prevent logging of API calls:
you can put an Activity Log at the end of the assembly and in there set Content and Content on error to none:

This way, API calls from outside the APIC consoles will not be logged in the Analytics log at all.
Please note that calls made from the internal APIC test client will still be logged.
Link to the extended yaml file:
Test_Redact_1.0.0_new.yaml_.txt
There is one of the out-of-the-box feature of API Connect that is extremely useful when trying to mask or remove authentication-related sensitive data from incoming requests. The header field Authorization gets sanitized/masked by default. Thus it can be used as a container for sensitive information that must not be logged in clear text. The following sample API demonstrates how you can use the default sanitization of API Connect for the Authorization header field to sanitize client id client secret or basic authentication credentials. In the sample we include the code to move either client id and client secret or basic authentication to the Authorization field. Just comment out the corresponding lines of code in the gateway script setauthheader as needed.
Link to the yaml file:
testsanclientauth_1.0.0.yaml_.txt
[{"Business Unit":{"code":"BU053","label":"Cloud \u0026 Data Platform"},"Product":{"code":"SSQTW3","label":"IBM On Demand Consulting for Hybrid Cloud"},"Component":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions","Edition":"","Line of Business":{"code":"","label":""}}]
Was this topic helpful?
Document Information
Modified date:
18 August 2021
UID
ibm10778965