How To
Summary
Default Self signed Guardium GIM SSL certificates are due to expire in May of 2024.
This technote describes how to check if action is required to update certificates on any appliances in a central manager (CM) environment
Objective
Steps
- GIM Clients are connected
- Default self signed GIM certificate, expiring May 2024 is present
- In cli run - show certificate summary
- Check the lines with Alias Name gim
- If the Valid To date is May/26/2024 or May/27/2024 then the problem is present and action is required
- The date might be different depending on the time zone of the appliance
- Example line with a problem:
-
Alias Name Valid From Valid To Subject File Name
------------------ ----------- ----------- ------------------------------------------------------ ----------------------------
gim May/29/2014 May/26/2024 xxxx CN=GIM, OU=xxx, O="xxx", L=xxx, ST=xxx, C=xxx .keystore
-
- On the CM only, install the correct ad-hoc patch for your CM version
-
CM major version Patch zip file Patch md5sum 12 2989785a58fb74a4d8603d96ef186319
11 c12391b52c585a529bb81420ab57d0a4
10 8bbc802d95f9284a244ebfbc9e6e7195
-
Download the zip file from this technote and unzip to get the patch, or contact Guardium support to provide
-
- After patch install completed, collect the results file
- From the CM fileserver, opt-ibm-guardium-logs, download results csv file called - enterprise_gim_cert_results_<date>_<time>.csv
- A new csv file is created for each time the patch is installed, collect the latest one based on date and time
- Review and understand the results file
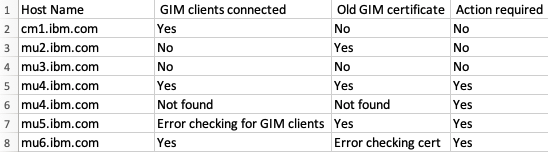
- Example output:
- Understanding the results:
- The patch checks the CM and all active MUs
- If "GIM clients connected" and "Old GIM certificate" column values are both yes - The checks succeeded and "Action required" is yes
- Actions from IBM Security Guardium default Self Signed Guardium Installation Manager (GIM) SHA128 Certificates set to expire in May of 2024 must be taken on that appliance
- If "GIM clients connected" or "Old GIM certificate" column values are no - The checks succeeded and "Action required" is no
- No action is needed on this appliance, because there are no GIM clients or the certificates are already updated
- If "GIM clients connected" and "Old GIM certificate" column values are both "Not found" - The patch was not able to check this appliance
- The root passkey might not be set or the appliance is down
- Action is required to check the appliance directly, or set the root passkey and re-install the patch
- If "GIM clients connected" or "Old GIM certificate" column values have an error - The patch was able to check the appliance but the commands did not work as expected
- Action is required to check the appliance directly
- If a large number of appliance have this problem, see troubleshooting steps section
- Example output:
- The patches can be reinstalled multiple times
- If appliances are down or root passkeys not set, re-install after resolving the problem and check the newest results csv
- If any unexpected result is found, contact Guardium support and provide:
- Results csv file
- Log file from CM fileserver opt-ibm-guardium-logs, download file called - gim_cert_expiry_check_<date>_<time>.log, with date and time matching the csv file
- Patch and system_db issues must gathers from CM
- From one of the MUs with a problem:
- Output of cli - show certificate summary
- Output of cli - support show passkey root
- Patch and system_db issues must gathers
Additional Information
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
19 February 2024
UID
ibm17115254