Troubleshooting
Problem
When accessing the Red Hat OpenShift Web Console, you are prompted with "Application is not available".
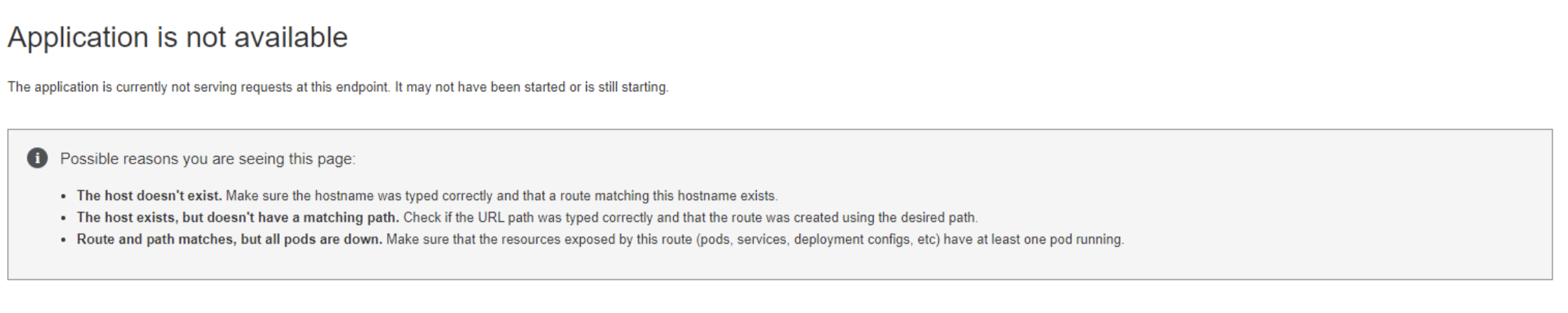
Symptom
- The web console is not accessible, however the cluster is accessible via 'oc login' command.
- There is "505 server internal error" in the console of browser.
Cause
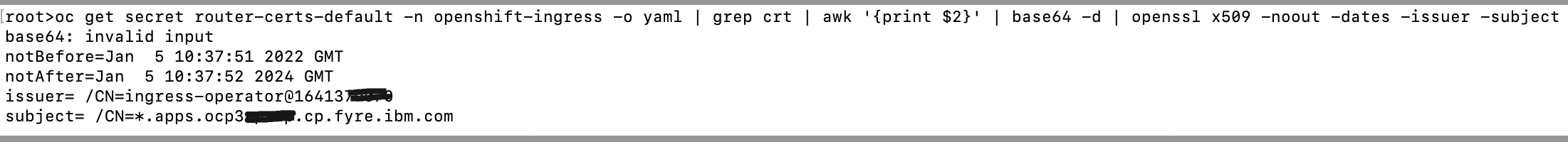
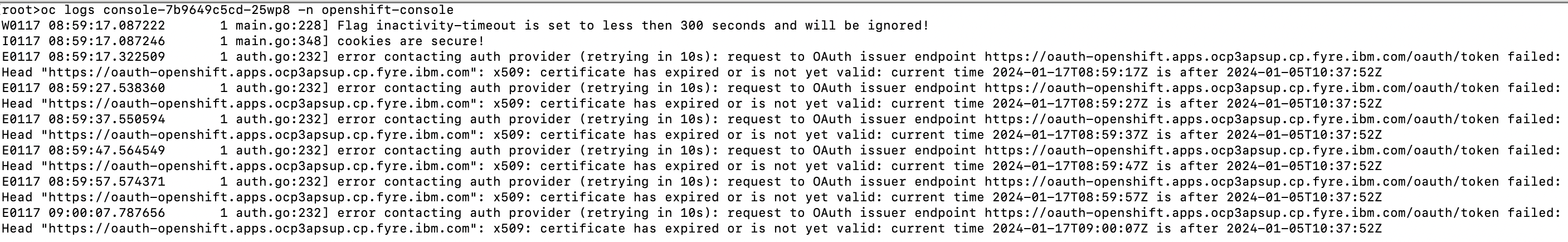
The OpenShift 4 web console is not accessible due to the default ingress certificate being expired. There is no alert when the default ingress certificate is about to be expired, refer to the details in RFE-4269.
Environment
RedHat OpenShift Platform 4.10
RedHat Openshift Platform 4.11
RedHat Openshift Platform 4.12
Diagnosing The Problem
Login the Cluster, check the validity of the ingress certificate by this command:
$ oc project openshift-ingress
$ oc get secret router-certs-default -o yaml | grep crt | awk '{print $2}' | base64 -d | openssl x509 -noout -dates -issuer -subject
Refer to the following sample output result:
The certificate error is encountered in logs of the console pod in 'openshif-console' namespace:
Resolving The Problem
Both, the ingress Certificate Authority (CA) and the ingress default certificate signed by this ingress CA, have a validity of 2 years. If the default ingress certificate is expired, then the ingress CA is also over its validity. The ingress CA has to be renewed firstly followed by the ingress wildcard certificate to avoid the CA mismatch.
Before replacing the CA and the certificate, take the existing secret backups and delete the secret containing the ingress CA and the default ingress certificate from the openshift-ingress-operator and openshift-ingress namespaces respectively. It is required to restart the respective pod.
First renew the ingress CA then create a new wild-card certificate using the new ingress CA.
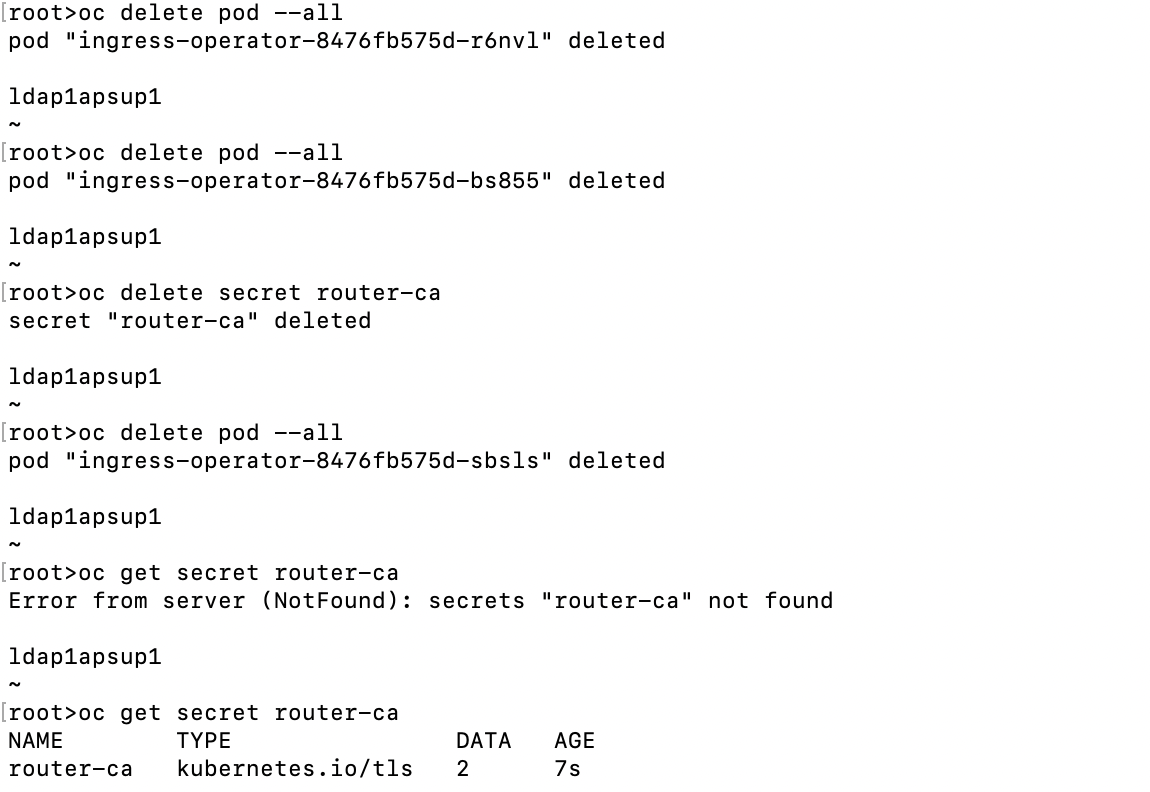
1. Refer to the following commands to renew the ingress CA:
$ oc project openshift-ingress-operator
$ oc get secret router-ca -o yaml > router-ca.yaml
$ oc delete secret router-ca
$ oc delete pod --all
$ oc get secret router-ca
$ oc get pod
And the snippet of sample output result:
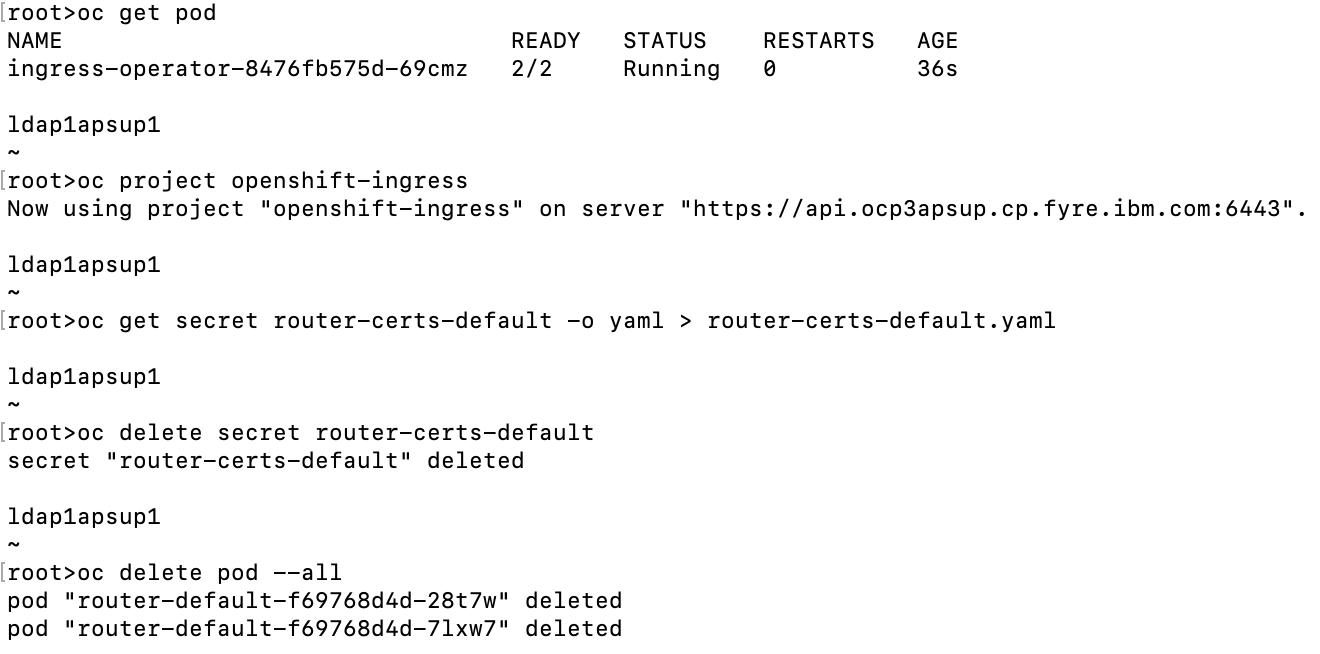
2. Refer to the following commands to re-create the wild-card ingress certificate using the new ingress CA:
$ oc project openshift-ingress
$ oc get secret router-certs-default -o yaml > router-certs-default.yaml
$ oc delete secret router-certs-default
$ oc delete pod --all
$ oc get secret router-certs-default
$ oc get pod
And the snippet of sample command output:
Optional: After the renewal of default ingress certificates, you may face "x509: Certificate signed by unknown authority" error while performing 'oc login' from the bastion host. In this case, users need to copy the router-ca and add it to the bastion host's trust store:
$ oc -n openshift-ingress-operator get secret router-ca -o jsonpath="{ .data.tls\.crt }" | base64 -d -i > ingress-ca.crt
$ cp /root/ingress-ca.crt /etc/pki/ca-trust/source/anchors/
$ update-ca-trust
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB10","label":"Data and AI"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSBYVB","label":"IBM Cloud Pak for Business Automation"},"ARM Category":[],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"21.0.2;21.0.3;22.0.1;22.0.2;23.0.1;23.0.2"}]
Product Synonym
CP4BA OCP RHOCP
Was this topic helpful?
Document Information
Modified date:
30 January 2024
UID
ibm17112004