Troubleshooting
Problem
You want to know how many rules contributed to an offense in the last few days.
Resolving The Problem
This process can be completed in two methods:
Method 1: Generating a list of Rules that generated an offense through the UI
Create a Custom Event Property (CEP) named "ruleId" that extracts the ruleId value from the "Offense Created" event.
Create a Custom Event Property (CEP) named "ruleId" that extracts the ruleId value from the "Offense Created" event.
-
Log in to the QRadar Console.
-
Click the Admin tab.
-
Click the Custom Event Property button.
-
Click the Add button.
-
For the Property Type Selection, keep it as Extraction Based
- Enable "Enable for use in Rules, Forwarding Profiles and Search Indexing"
- Set the Log Source Type to SIM Audit
- Search for the Event Name "Offense Created", with a QID of 28250369.
- Add in the following for Regex:
ruleId="([0-9]*)"\s - Add in the following payload as the Test Field:
Feb 9 05:27:29 127.0.0.1 [parent=[hostname]] | [Action] [Offense] [OffenseCreated] OffenseProperties ( id="111", type="BY_REG_LOGSOURCE_ANOMALYTRIGGER", direction="OffenseDirectionType: Remote to Remote", createdDate="1675938449333", ruleId="121196" ) - Click the Test button to verify that it captures the values after ruleId.
- Click the Save button.
Result
You created the "ruleId" CEP with the following configurations: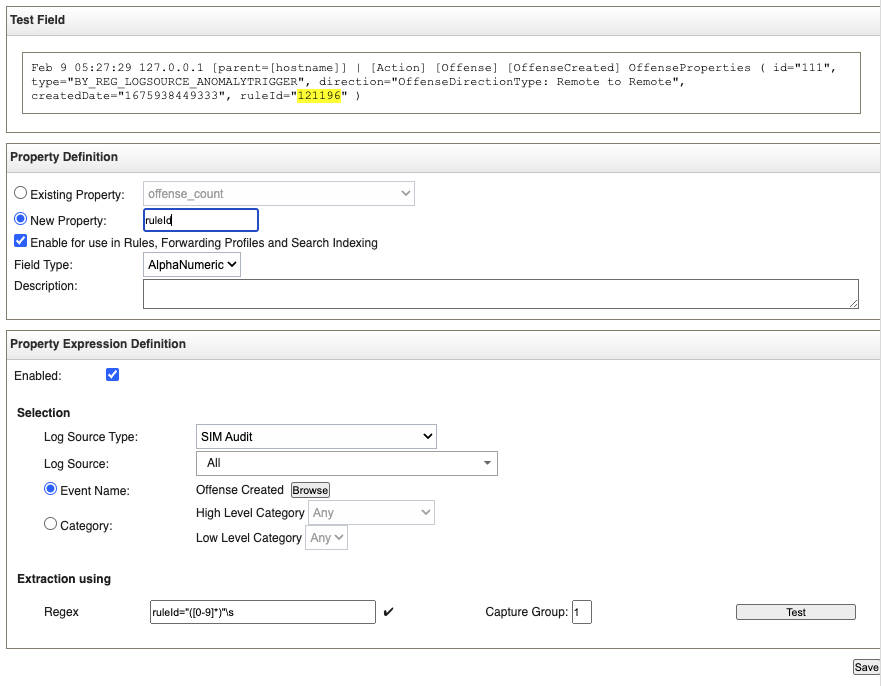
Conduct an AQL search in the Log Activity tab
- Click the Log Activity tab.
- Change the filter to Advanced Search.
- Modify this AQL query to the time frame as needed. In this example, it is searching for the last 2 days:
SELECT rulename("ruleId") AS 'Custom Rule', QIDNAME(qid) as 'Event Name',LONG(COUNT()) as "Count" FROM events WHERE qid = 28250369 GROUP BY "Custom Rule" order by "Count" desc LAST 2 DAYS - Click the Search button.
Result
You conduct a search that lists the Rules that generated an offense in the last 2 days: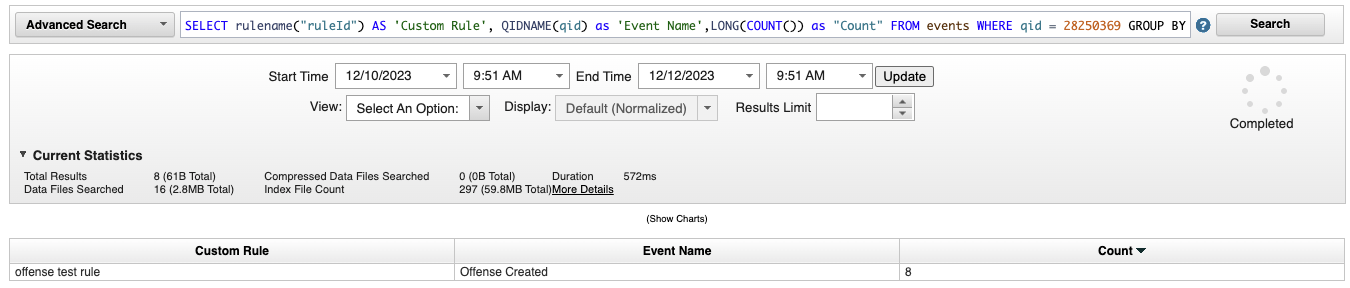
Method 2: Generating a list of Rules that contributed to an offense from the backend
- SSH to the Console
- Run the following command, modify the time frame in the
interval 'x'section as needed. More details on how that syntax works can be found in this documentation - Date/Time Functions and Operators :psql -U qradar -c "select rule_name, count(id) from offense_cre_agg where to_timestamp(start_time/1000) > now() - interval 'x' group by rule_name order by 1 desc;"
Results
You generated a list of Rules that made an offense in the last 2 days through the backend:# psql -U qradar -c "select rule_name, count(id) from offense_cre_agg where to_timestamp(start_time/1000) > now() - interval '2 days' group by rule_name order by 1 desc;"
rule_name | count
-------------------+-------
offense test rule | 8
(1 row)
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB24","label":"Security Software"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSBQAC","label":"IBM Security QRadar SIEM"},"ARM Category":[{"code":"a8m0z000000cwthAAA","label":"Offenses"},{"code":"a8m0z000000cwtrAAA","label":"Rules"}],"ARM Case Number":"","Platform":[{"code":"PF016","label":"Linux"}],"Version":"All Versions"}]
Was this topic helpful?
Document Information
Modified date:
19 December 2023
UID
ibm17091953