Release Notes
Abstract
Wi-Fi profiles using 802.1x EAP with certificates failed to deploy to Android 13 devices with the latest security patches. As a result, the Wi-Fi profiles were stuck in the Pending state on the Settings page of the MaaS360 for Android app.
Content
Affected devices
The devices currently affected by this issue are Pixel devices running Android 13 and above, with the latest security patches (May 2023 or later). However, it is important to note that Google's planned deployment of this change extends beyond Android 13 Pixel devices with the latest security update.
Resolution
In the latest Google security patch, a new mandatory validation for server certificate parameters was added for a Wi-Fi profile that uses 802.1x EAP with a certificate. For the validation to succeed, the Wi-Fi profile must have a root certificate set, and either domain prefix match or alternate subject match must be set.
Note: Administrators must ensure that the MaaS360 for Android app is upgraded to version 8.26.
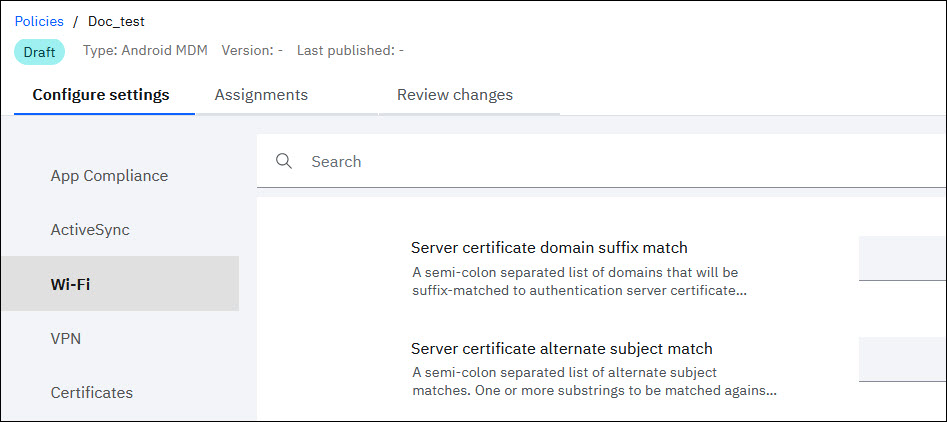
MaaS360 added two text fields in the Wi-Fi section of the Android Enterprise MDM policy, and these fields are visible only when the 802.1x EAP has been set as the Wi-Fi configuration type.
One of the following two fields must be configured in the Wi-Fi profile for the profile to deploy on the device:
| Policy Setting | Description |
|---|---|
| Server certificate domain suffix match |
A semi-colon separated list of domains that will be suffix-matched to authentication server certificate alternate subject dNSName elements.
Example: domain.com;example.com Matches: A certificate with domain.com, example.com, or any subdomains of those domains, in the dNSName of the SubjectAltName. Note: Wildcards are not supported. This field performs a suffix-match, i.e. domain.com will match test.domain.com, but not test-domain.com. This is the recommended field to use in general. |
| Server certificate alternate subject match |
A semi-colon separated list of alternate subject matches. One or more substrings to be matched against the alternate subject of the authentication server certificate. Example: DNS:server.example.com;EMAIL:server@example.com Matches: A certificate with a dNSName of server.example.com (or subdomains), or with an Email of server@example.com in the SubjectAltName. Note: This is an advanced field that should generally only be needed if domain suffix match is not possible. |
Note: If no domain suffix is set using the Server certificate domain suffix match, and no alternate subject match is set using the Server certificate alternate subject match field, then the Wi-Fi profile may fail to configure on the device with the latest security update, and will be stuck in a Pending state.
Customer administrators: How to fill the domain or alternate subject match fields
The domain suffix match or alternate subject match fields must match the Subject Alternative Name respective elements in the RADIUS Server Certificate.
To get the correct values to set in the policy:
- Go into the RADIUS server that is validating the 802.1x Wi-Fi connections.
- Find the RADIUS Server Certificate. This is the certificate presented to all devices that authenticate to the Wi-Fi network.
Note: The procedure depends on the RADIUS server product used. The product vendor and network administrator can be contacted for assistance.
- Find the Subject Alternative Name section in the certificate.
- Look for "DNS Name" elements. These element(s) can be added in the domain suffix match fields in the MaaS360 policy. At least one domain must match in the policy for the connections to succeed.
Note:
- Do not include wildcards in the MaaS360 policy. For example if the "DNS Name" element in the certificate is *.example.com, add "example.com" in the MaaS360 policy.
- If the certificate has no "DNS Name" fields but has other fields such as "Email", these can be used in the alternate subject match field of the MaaS360 policy.In the majority of cases the "DNS Name" elements should be present.
Required policy changes
- Open an Android MDM policy and go to Android Enterprise Settings > Wi-Fi.
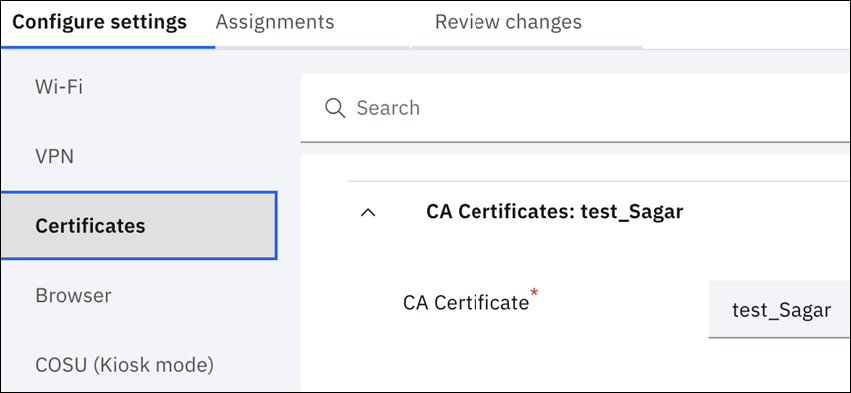
- Make sure a Root Certificate has been set in the Wi-Fi profile.
- Configure one of the following fields:
- Server certificate domain suffix match
- Server certificate alternate subject match
- Go to the Certificates section of Android Enterprise Settings and make sure the Root Certificate previously selected in the Wi-Fi profile is being distributed in the CA Certificate policy.
- Republish the policy.
Was this topic helpful?
Document Information
Modified date:
12 June 2023
UID
ibm17003265