How To
Summary
With the release of the Turbonomic SaaS offering, we've modified the steps to target AWS accounts using IAM Roles. The IAM Role will need to be created in every AWS account you would like Turbonomic to manage.
Steps
Check your Turbonomic SaaS URL to determine which instructions to follow for AWS Role-based targeting.
|
Turbonomic SaaS URL Naming Convention |
Turbonomic SaaS Location |
|---|---|
|
xxxxxx.customer.turbonomic.ibmappdomain.cloud |
AWS US |
|
xxxxxx.euc1.turbonomic.ibmappdomain.cloud |
AWS EU (Frankfurt) |
| xxxxxx.euw2.turbonomic.ibmappdomain.cloud | AWS UK (London) |
| xxxxxx.apse2.turbonomic.ibmappdomain.cloud | AWS AP (Sydney) |
| xxxxxx.turbonomic.io | GCP US |
SaaS in AWS US, EU, or UK
For customers with URLs matching the following naming conventions:
· AWS US: xxxxxx.customer.turbonomic.ibmappdomain.cloud
· AWS EU: xxxxxx.euc1.turbonomic.ibmappdomain.cloud
· AWS UK: xxxxxx.euw2.turbonomic.ibmappdomain.cloud
· AWS AP: xxxxxx.apse2.turbonomic.ibmappdomain.cloud
1. Create an Identify Provider
a. Navigate to Identity and Access Management (IAM)
b. In Access Management select Identity Providers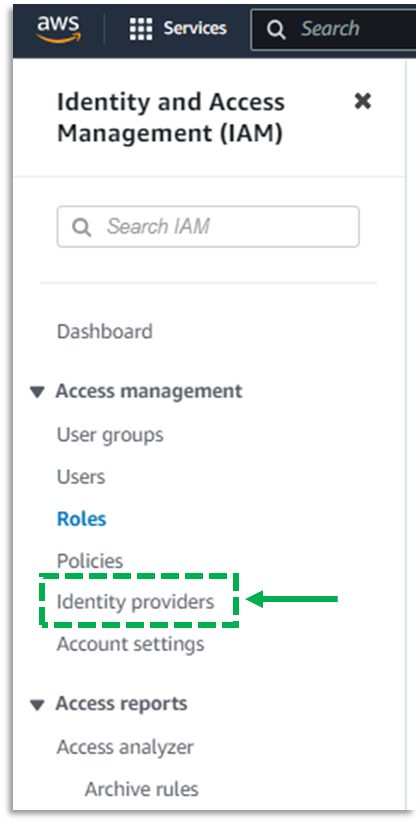
c. Click Add Provider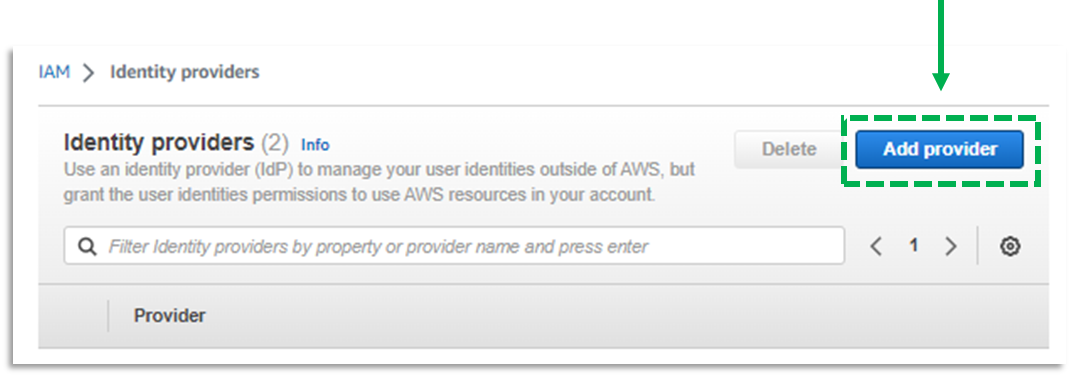
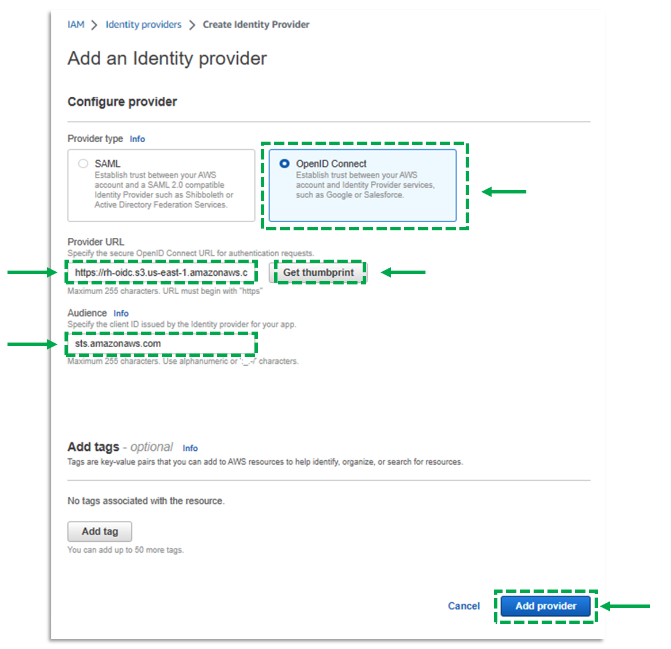
d. Select OpenID Connect
e. For Provider URL enter the URL based on the location of your Turbonomic SaaS instance:
https://rh-oidc.s3.us-east-1.amazonaws.com/22ejnvnnturfmt6km08idd0nt4hekbn7https://rh-oidc.s3.us-east-1.amazonaws.com/23e3sd27sju1hoou6ohfs68vbno607trhttps://rh-oidc.s3.us-east-1.amazonaws.com/23ne21h005qjl3n33d8dui5dlrmv2tmghttps://rh-oidc.s3.us-east-1.amazonaws.com/24jrf12m5dj7ljlfb4ta2frhrcoadm26f. Click Get thumbprint
g. For Audience enter:sts.amazonaws.com
h. Click Add provider
2. Create an IAM Role
a. Navigate to Identity and Access Management (IAM)
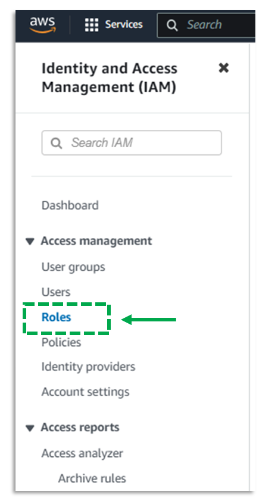
b. In Access Management select Roles
c. Click Create role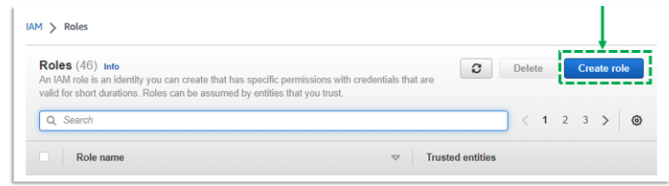
d. Select Web identity
e. For Identity provider, select the Identity Provider you created in step 1.
https://rh-oidc.s3.us-east-1.amazonaws.com/22ejnvnnturfmt6km08idd0nt4hekbn7https://rh-oidc.s3.us-east-1.amazonaws.com/23e3sd27sju1hoou6ohfs68vbno607trhttps://rh-oidc.s3.us-east-1.amazonaws.com/23ne21h005qjl3n33d8dui5dlrmv2tmghttps://rh-oidc.s3.us-east-1.amazonaws.com/24jrf12m5dj7ljlfb4ta2frhrcoadm26f. For Audience, select:sts.amazonaws.com
g. Click Next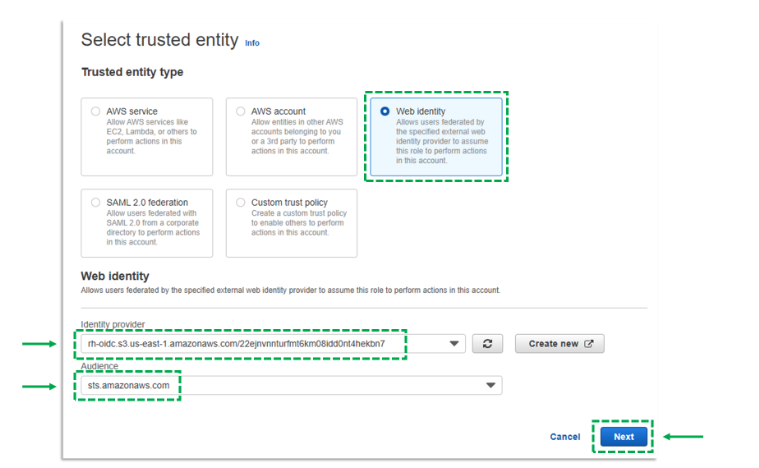
h. Add permissions to the Role.
From the 4 options below, select the desired level of permissions you would like Turbonomic to have when managing AWS accounts. You can choose to leverage the existing “AWS Managed” policies or create your own “Customer Managed” policy for even more granular access. For more details on permissions, view Turbonomic Documentation: AWS Permissions.
i. AWS Managed Permissions: Read-Only
Leverages existing AWS Policies to define read-only access for Turbonomic.
· AmazonEC2ReadOnlyAccess
· AmazonS3ReadOnlyAccess
· AmazonRDSReadOnlyAccess
· AWSConfigRoleForOrganizations (only required for consolidated billing with the master account)
ii. AWS Managed Permissions: Action Execution
Leverages existing AWS Policies to allow Turbonomic users to execute actions.
· AmazonEC2FullAccess
· AmazonS3ReadOnlyAccess
· AmazonRDSFullAccess
· AWSConfigRoleForOrganizations (only required for consolidated billing with the master account)
iii. Customer Managed Permissions: Minimum Read-Only
Create a custom policy that defines the bare-minimum permissions required for Turbonomic read-only access.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeTags",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListTagsForResource",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeRegions",
"ec2:DescribeReservedInstances",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeTags",
"ec2:DescribeVolumes",
"ec2:DescribeVolumesModifications",
"ec2:DescribeVolumeStatus",
"elasticloadbalancing:DescribeInstanceHealth",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"iam:GetUser",
"organizations:DescribeOrganization",
"organizations:ListAccounts",
"pi:GetResourceMetrics",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameters",
"rds:DescribeOrderableDBInstanceOptions",
"rds:ListTagsForResource",
"rds:ListTagsForResource",
"servicecatalog:SearchProducts",
"savingsplans:DescribeSavingsPlans"
],
"Resource": "*"
}
]
}
iv. Customer Managed Permissions: Minimum Execution
Create a custom policy that defines the bare-minimum permissions required for Turbonomic users to execute actions.
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": [
"autoscaling:CreateLaunchConfiguration",
"autoscaling:DeleteLaunchConfiguration",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeTags",
"autoscaling:ResumeProcesses",
"autoscaling:SuspendProcesses",
"autoscaling:UpdateAutoScalingGroup",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListTagsForResource",
"ec2:DeleteVolume",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeInstanceStatus",
"ec2:DescribeRegions",
"ec2:DescribeReservedInstances",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeReservedInstancesOfferings",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeTags",
"ec2:DescribeVolumes",
"ec2:DescribeVolumesModifications",
"ec2:DescribeVolumeStatus",
"ec2:ModifyInstanceAttribute",
"ec2:ModifyVolume",
"ec2:StartInstances",
"ec2:StopInstances",
"elasticloadbalancing:DescribeInstanceHealth",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"iam:GetUser",
"KMS:CreateGrant",
"organizations:DescribeOrganization",
"organizations:ListAccounts",
"pi:GetResourceMetrics",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameters",
"rds:DescribeOrderableDBInstanceOptions",
"rds:ListTagsForResource",
"rds:ModifyDBInstance",
"servicecatalog:DescribeProduct",
"servicecatalog:DescribeRecord",
"servicecatalog:ListLaunchPaths",
"servicecatalog:ProvisionProduct",
"servicecatalog:SearchProducts",
"savingsplans:DescribeSavingsPlans"
],
"Resource": "*"
}
]
}
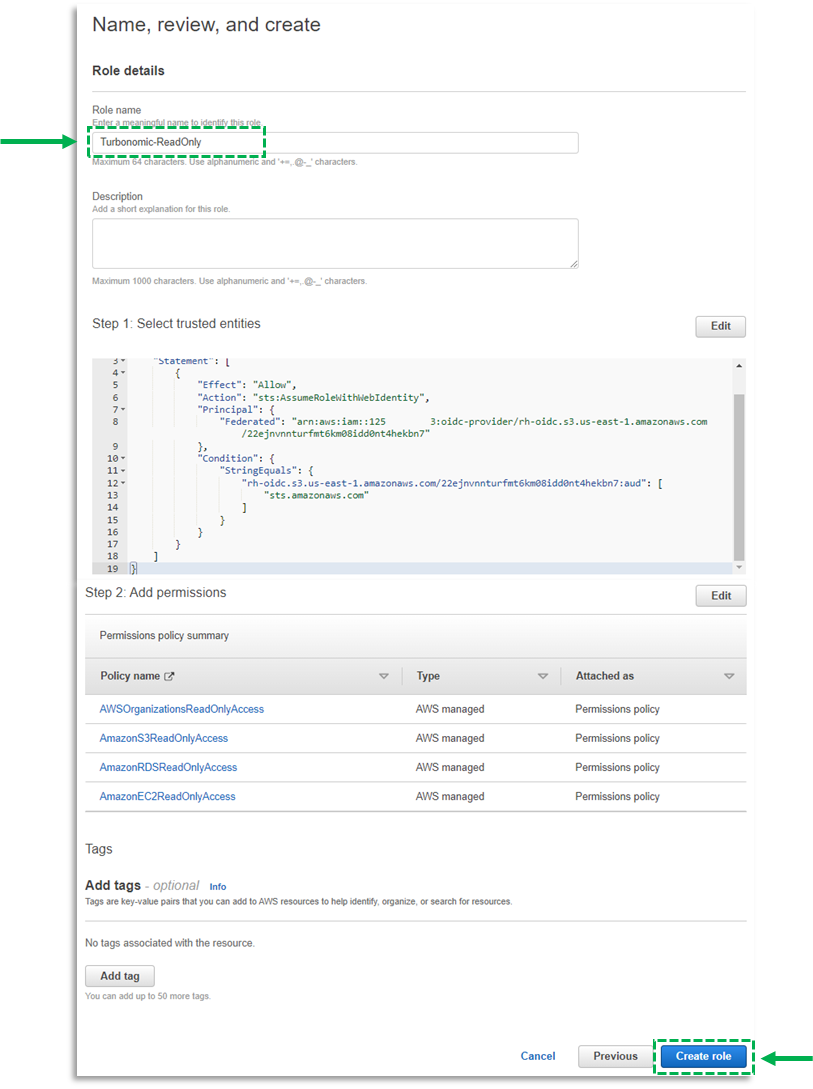
i. Once you’ve assigned your desired permissions, click Next
j. For Role name, provide a name for your role.
k. Click Create role
3. Attach the Trust Relationship to the Role:
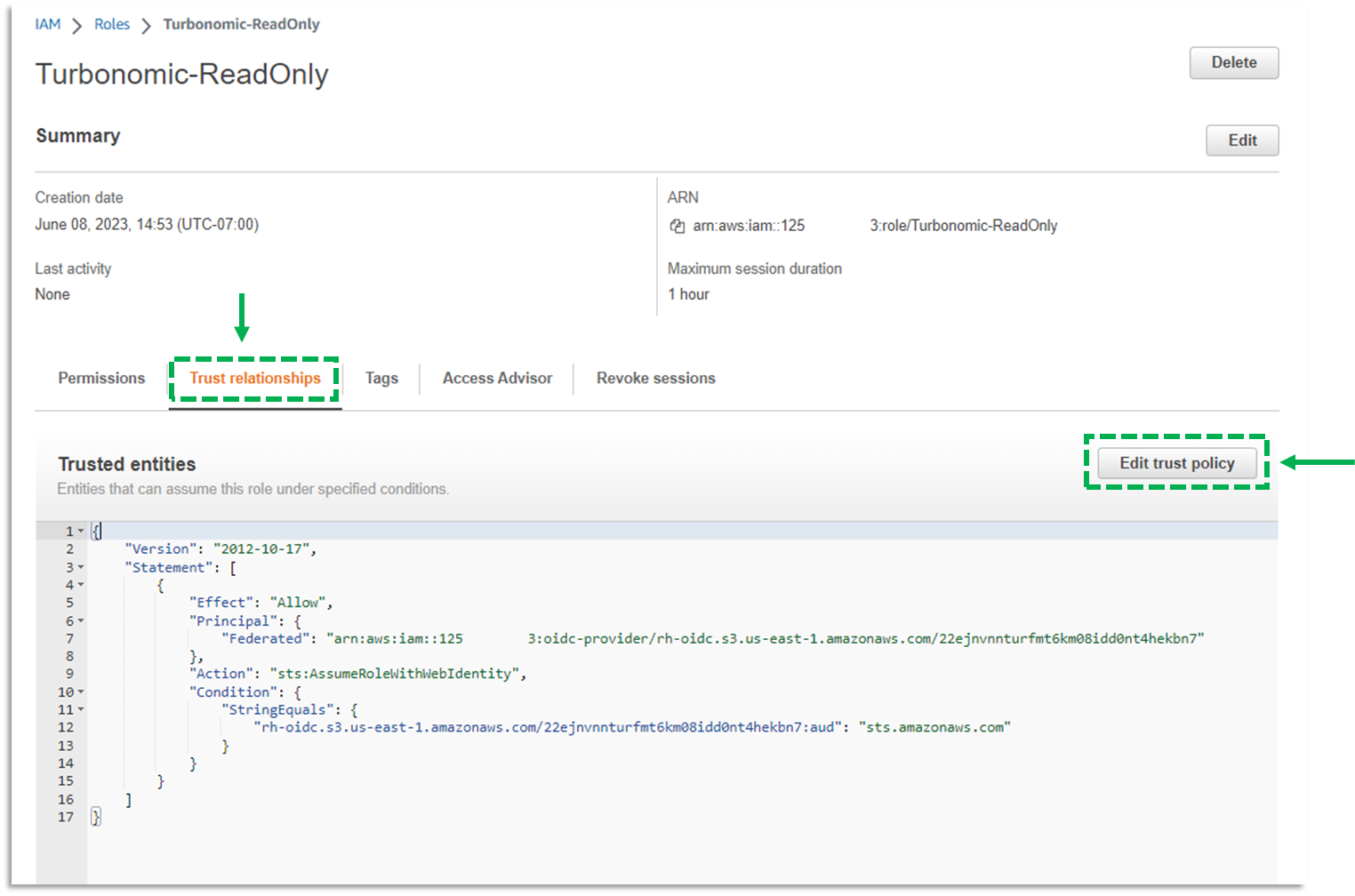
a. Navigate to Identity and Access Management (IAM)
b. In Access Management select Roles
c. Locate the Role you created in step 2 and select it.
d. Click on Trust relationships
e. Click Edit trust policy
f. Overwrite the existing policy with the one below. Choose the policy that corresponds with where your Turbonomic SaaS instance is hosted. Replace the following variables in the JSON:
- <YOUR_AWS_ACCOUNT_NUMBER>
- <TENANT_ID> Contact your Turbonomic account team if you do not have this information.**
- <TENANT_SVC_ACCOUNT> Contact your Turbonomic account team if you do not have this information.**
**For SaaS Trial users, where the URL begins with "trb" (Example: trb87654321.customer.turbonomic.ibmappdomain.cloud) the <TENANT_ID> and <TENANT_SVC_ACCOUNT> are derived from the unique ID in the URL. For example, using the URL above, the unique ID is trb87654321. Therefore, my <TENANT_ID> and <TENANT_SVC_ACCOUNT> are as follows:
- <TENANT_ID> = trb87654321
- <TENANT_SVC_ACCOUNT> = trb87654321-sa
· Hosted in AWS US
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<YOUR_AWS_ACCOUNT_NUMBER>:oidc-provider/rh-oidc.s3.us-east-1.amazonaws.com/22ejnvnnturfmt6km08idd0nt4hekbn7"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"rh-oidc.s3.us-east-1.amazonaws.com/22ejnvnnturfmt6km08idd0nt4hekbn7:sub":"system:serviceaccount:<TENANT_ID>:<TENANT_SVC_ACCOUNT>"
}
}
}
]
}
· Hosted in AWS EU
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<YOUR_AWS_ACCOUNT_NUMBER>:oidc-provider/rh-oidc.s3.us-east-1.amazonaws.com/23e3sd27sju1hoou6ohfs68vbno607tr"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"rh-oidc.s3.us-east-1.amazonaws.com/23e3sd27sju1hoou6ohfs68vbno607tr:sub":"system:serviceaccount:<TENANT_ID>:<TENANT_SVC_ACCOUNT>"
}
}
}
]
}
· Hosted in AWS UK
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<YOUR_AWS_ACCOUNT_NUMBER>:oidc-provider/rh-oidc.s3.us-east-1.amazonaws.com/23ne21h005qjl3n33d8dui5dlrmv2tmg"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"rh-oidc.s3.us-east-1.amazonaws.com/23ne21h005qjl3n33d8dui5dlrmv2tmg:sub":"system:serviceaccount:<TENANT_ID>:<TENANT_SVC_ACCOUNT>"
}
}
}
]
}
· Hosted in AWS AP
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<YOUR_AWS_ACCOUNT_NUMBER>:oidc-provider/rh-oidc.s3.us-east-1.amazonaws.com/24jrf12m5dj7ljlfb4ta2frhrcoadm26"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"rh-oidc.s3.us-east-1.amazonaws.com/24jrf12m5dj7ljlfb4ta2frhrcoadm26:sub":"system:serviceaccount:<TENANT_ID>:<TENANT_SVC_ACCOUNT>"
}
}
}
]
}
g. Click Update policy
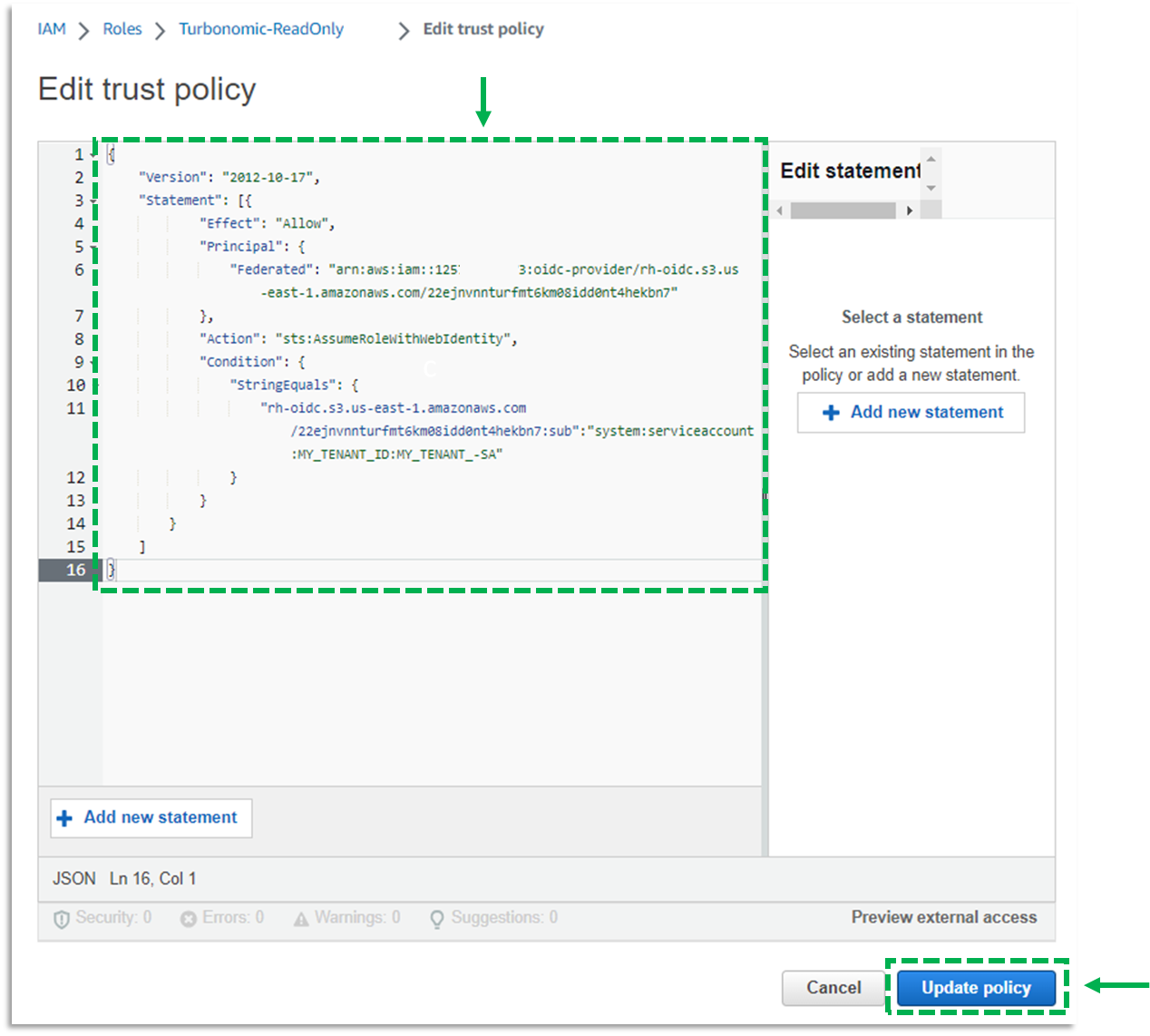
h. Record the ARN of the Role. This will be used to target the AWS account in Turbonomic.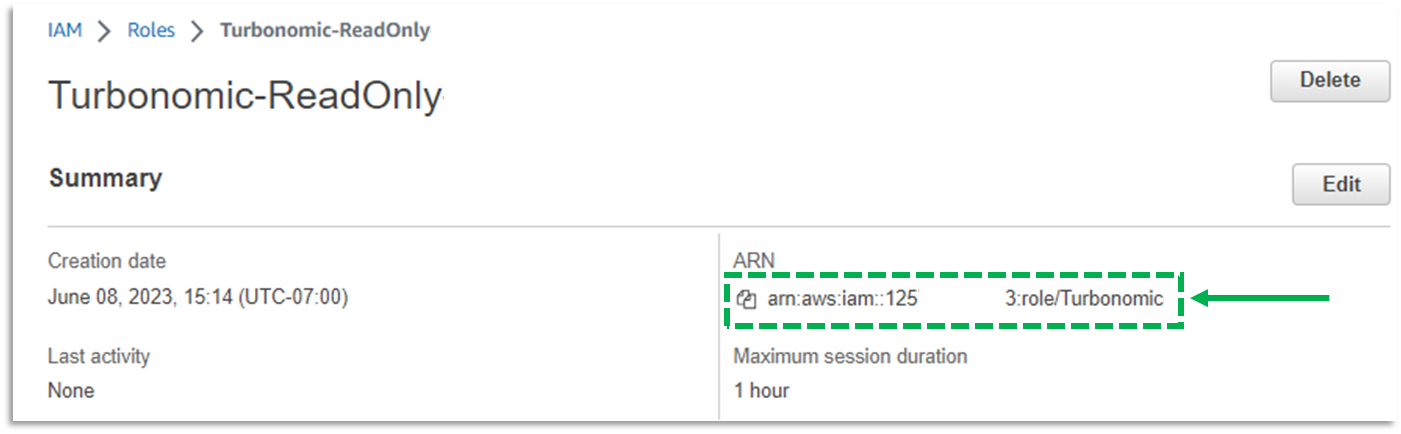
4. Target the AWS Account in Turbonomic
a. In Turbonomic, navigate to Settings > Target Configuration > New Target
b. Select Public Cloud > AWS
c. In Custom Target Name, provide a friendly name to identify this AWS account.
d. Toggle the IAM Role switch to “On/Green”
e. In the IAM Role ARN field, paste the ARN you recorded in step 3.
f. Click Add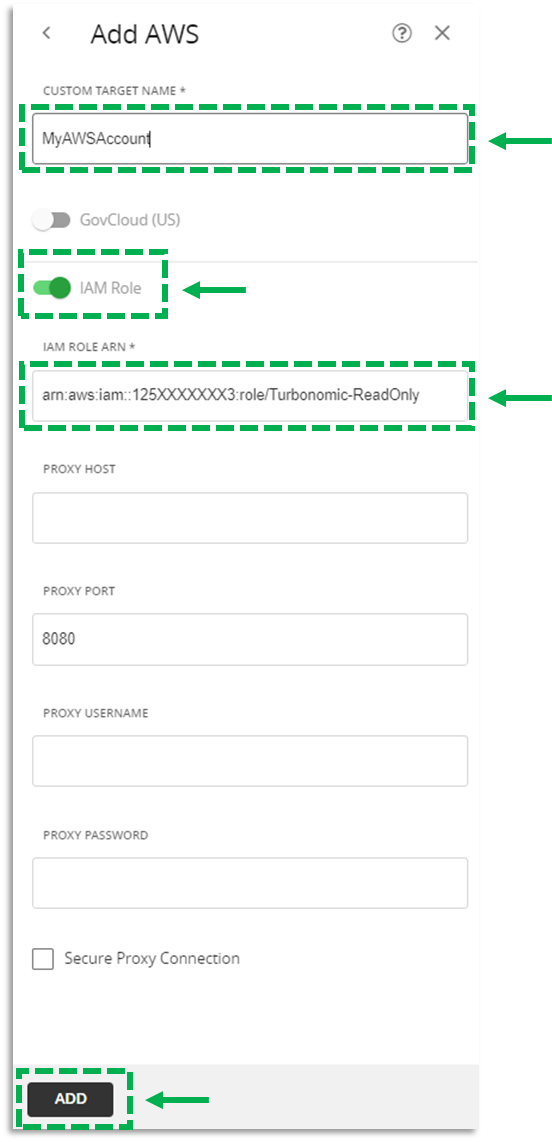
SaaS in GCP
For customers with URLs matching the following naming convention:
· GCP: xxxxxx.turbonomic.io
1. Create an IAM Role
a. Navigate to Identity and Access Management (IAM)
b. In Access Management select Roles
c. Click Create role
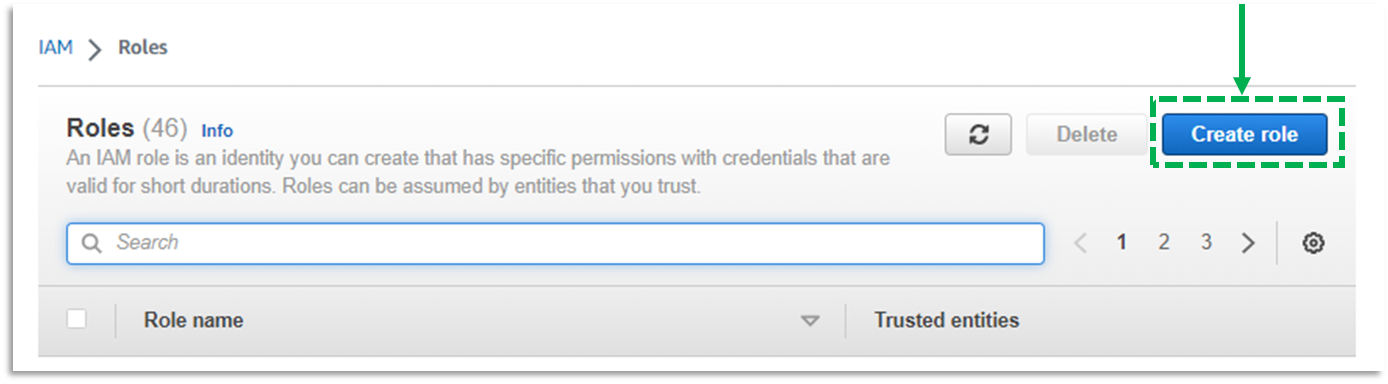
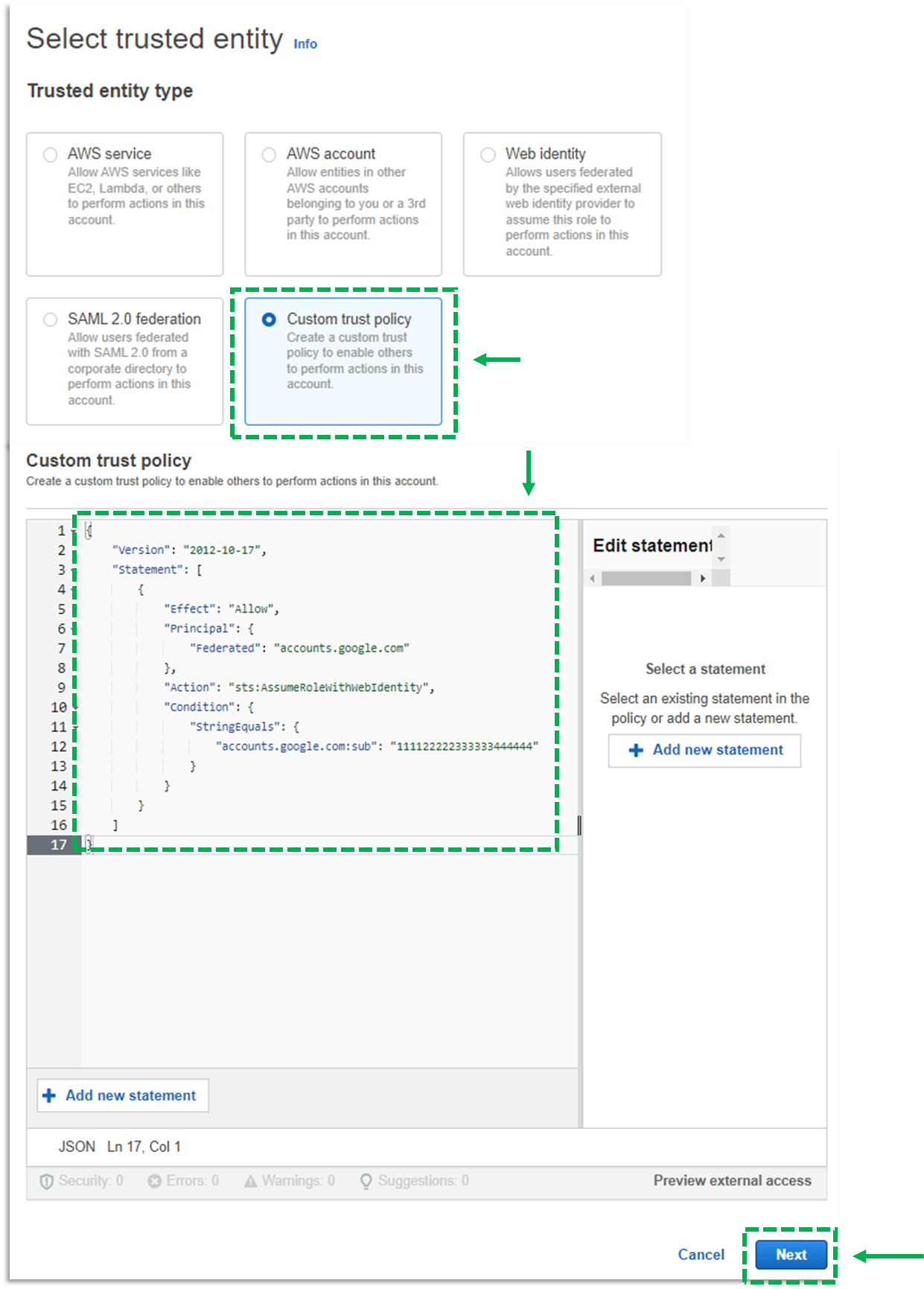
d. Select Custom trust policy
e. Overwrite the existing policy with the one below. Replace the following variables in the JSON:
<SERVICE_ACCOUNT_IDENTIFIER> Contact your Turbonomic account team if you do not have this information.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "accounts.google.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"accounts.google.com:sub": "<SERVICE_ACCOUNT_IDENTIFIER>"
}
}
}
]
}
f. Add permissions to the Role.
From the 4 options below, select the desired level of permissions you would like Turbonomic to have when managing AWS accounts. You can choose to leverage the existing “AWS Managed” policies or create your own “Customer Managed” policy for even more granular access. For more details on permissions, view Turbonomic Documentation: AWS Permissions.
i. AWS Managed Permissions: Read-Only
Leverages existing AWS Policies to define read-only access for Turbonomic.
· AmazonEC2ReadOnlyAcces
· AmazonS3ReadOnlyAccess
· AmazonRDSReadOnlyAccess
· AWSConfigRoleForOrganizations (only required for consolidated billing with the master account)
ii. AWS Managed Permissions: Action Execution
Leverages existing AWS Policies to allow Turbonomic users to execute actions.
· AmazonEC2FullAccess
· AmazonS3ReadOnlyAccess
· AmazonRDSFullAccess
· AWSConfigRoleForOrganizations (only required for consolidated billing with the master account)
iii. Customer Managed Permissions: Minimum Read-Only
Create a custom policy that defines the bare-minimum permissions required for Turbonomic read-only access.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeTags",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListTagsForResource",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeRegions",
"ec2:DescribeReservedInstances",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeTags",
"ec2:DescribeVolumes",
"ec2:DescribeVolumesModifications",
"ec2:DescribeVolumeStatus",
"elasticloadbalancing:DescribeInstanceHealth",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"iam:GetUser",
"organizations:DescribeOrganization",
"organizations:ListAccounts",
"pi:GetResourceMetrics",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameters",
"rds:DescribeOrderableDBInstanceOptions",
"rds:ListTagsForResource",
"rds:ListTagsForResource",
"servicecatalog:SearchProducts",
"savingsplans:DescribeSavingsPlans"
],
"Resource": "*"
}
]
}
iv. Customer Managed Permissions: Minimum Execution
Create a custom policy that defines the bare-minimum permissions required for Turbonomic users to execute actions.
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": [
"autoscaling:CreateLaunchConfiguration",
"autoscaling:DeleteLaunchConfiguration",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeTags",
"autoscaling:ResumeProcesses",
"autoscaling:SuspendProcesses",
"autoscaling:UpdateAutoScalingGroup",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListTagsForResource",
"ec2:DeleteVolume",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeInstanceStatus",
"ec2:DescribeRegions",
"ec2:DescribeReservedInstances",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeReservedInstancesOfferings",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeSpotPriceHistory",
"ec2:DescribeTags",
"ec2:DescribeVolumes",
"ec2:DescribeVolumesModifications",
"ec2:DescribeVolumeStatus",
"ec2:ModifyInstanceAttribute",
"ec2:ModifyVolume",
"ec2:StartInstances",
"ec2:StopInstances",
"elasticloadbalancing:DescribeInstanceHealth",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"iam:GetUser",
"KMS:CreateGrant",
"organizations:DescribeOrganization",
"organizations:ListAccounts",
"pi:GetResourceMetrics",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameters",
"rds:DescribeOrderableDBInstanceOptions",
"rds:ListTagsForResource",
"rds:ModifyDBInstance",
"servicecatalog:DescribeProduct",
"servicecatalog:DescribeRecord",
"servicecatalog:ListLaunchPaths",
"servicecatalog:ProvisionProduct",
"servicecatalog:SearchProducts",
"savingsplans:DescribeSavingsPlans"
],
"Resource": "*"
}
]
}
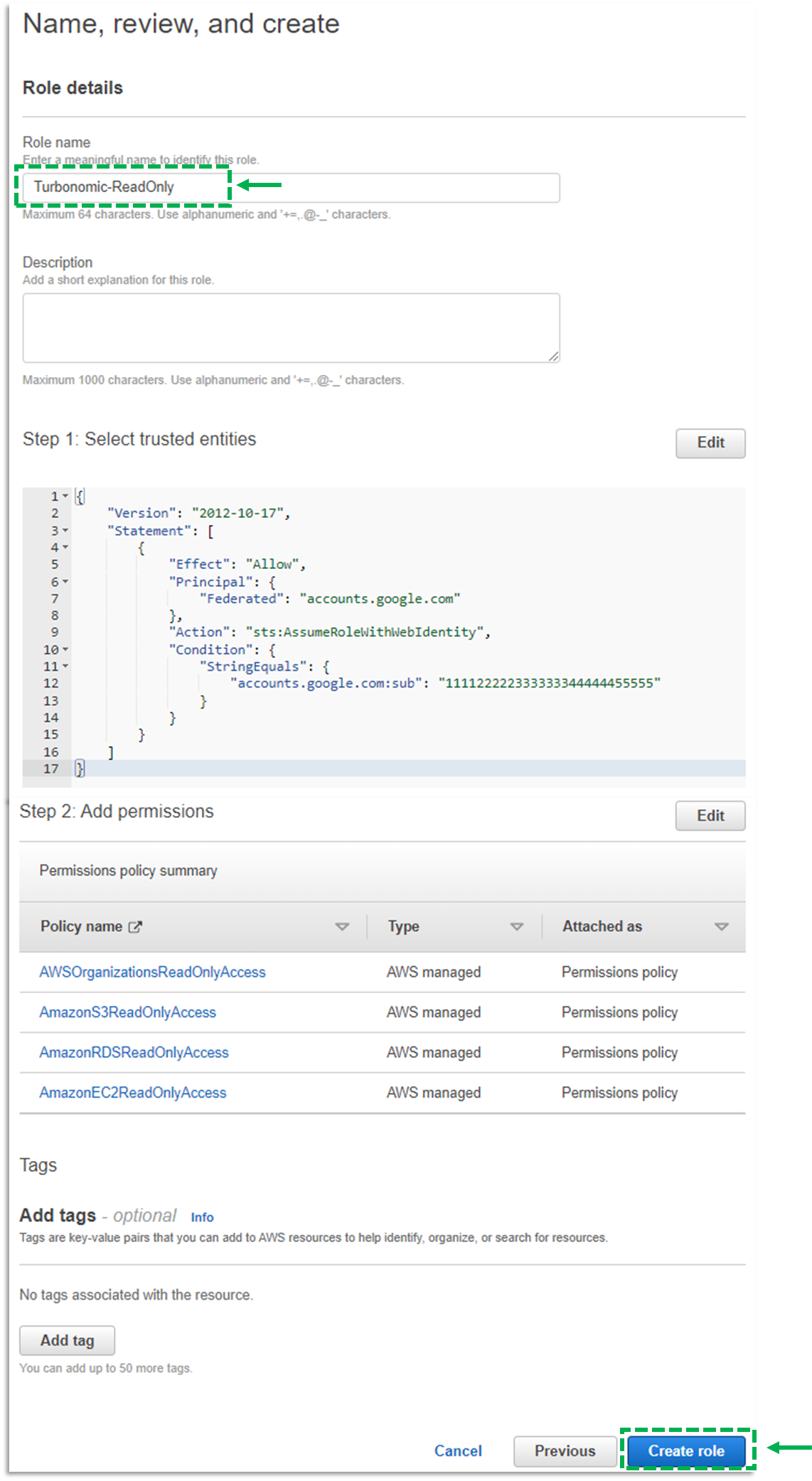
g. Once you’ve assigned your desired permissions, click Next
h. For Role name, provide a name for your role.
i. Click Create role
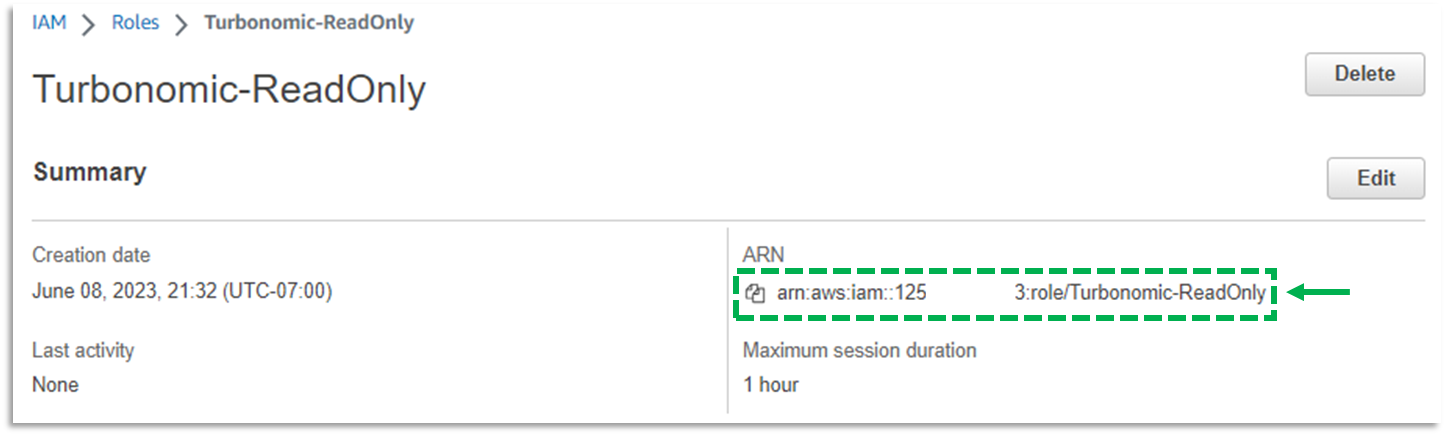
j. Locate and select the Role you just created. Record the ARN of the Role. This will be used to target the AWS account in Turbonomic.
2. Target the AWS Account in Turbonomic
a. In Turbonomic, navigate to Settings > Target Configuration > New Target
b. Select Public Cloud > AWS
c. In Custom Target Name, provide a friendly name to identify this AWS account.
d. Toggle the IAM Role switch to “On/Green”
e. In the IAM Role ARN field, paste the ARN you recorded in step 3.
f. Click Add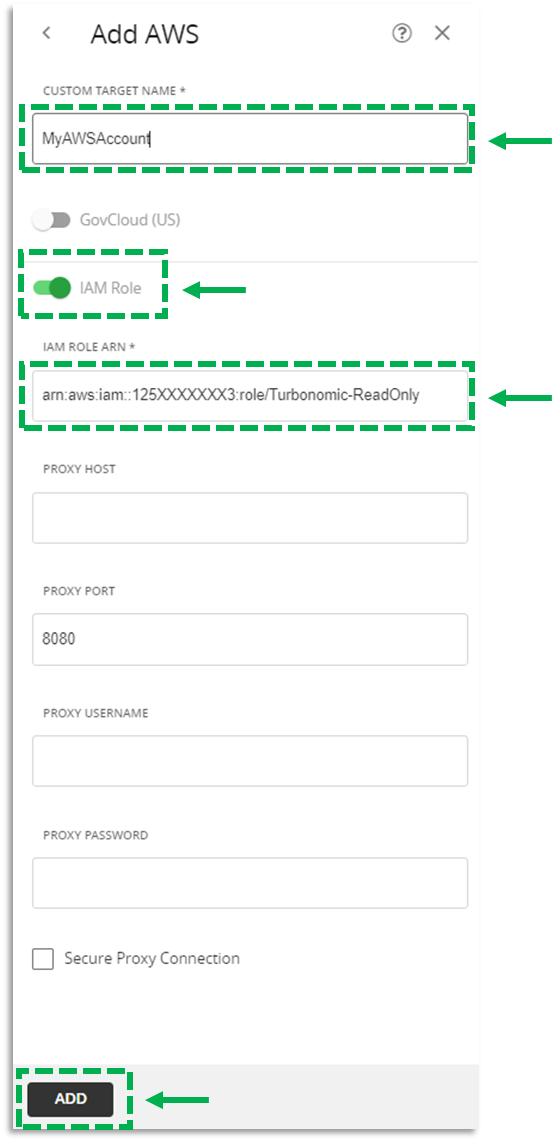
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
15 August 2023
UID
ibm16854437