Troubleshooting
Problem
SPNEGO SSO is not working correctly due to a recent Microsoft security patch.
Please see the following externally linked information on the November 2022 patch Microsoft has released.
Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability CVE-2022-37966
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37966
KB5021131: How to manage the Kerberos protocol changes related to CVE-2022-37966
https://support.microsoft.com/en-us/topic/kb5021131-how-to-manage-the-kerberos-protocol-changes-related-to-cve-2022-37966-fd837ac3-cdec-4e76-a6ec-86e67501407d
Symptom
Cause
Error "Illegal key size"
[JGSS_DBG_CTX] WebContainer : 1 Error authenticating request. Reporting to clientMajor code = 11, Minor code = 0org.ietf.jgss.GSSException, major code: 11, minor code: 0major string: General failure, unspecified at GSSAPI levelminor string: Kerberos error while decoding and verifying token: com.ibm.security.krb5.internal.crypto.KrbCryptoException, status code: 0message: java.security.InvalidKeyException: Illegal key size
[JGSS_DBG_CTX] WebContainer : 1 Error authenticating request. Reporting to clientMajor code = 11, Minor code = 45org.ietf.jgss.GSSException, major code: 11, minor code: 45major string: General failure, unspecified at GSSAPI levelminor string: Kerberos error while decoding and verifying token: com.ibm.security.krb5.KrbException, status code: 45message: No key of type: 23
Diagnosing The Problem
-
In the administrative console, navigate to Servers > [+] Server Types > WebSphere Application Servers > server_name.
-
Under Server Infrastructure, expand [+] Java and process management. Click Process Definition > Java Virtual Machine > Custom Properties.
-
Create two new Java ™ Virtual Machine (JVM) properties, assuming the properties don't already existName: com.ibm.security.jgss.debug
Value: allName: com.ibm.security.krb5.Krb5Debug
Value: all -
After creating the properties, save the changes.
- Expand TroubleShooting > Logs and Trace > server_name.
- Click Diagnostic Trace Service.
- Increase the Maximum Number of Historical Files from 1 to 10.
- Click Apply (you can save the changes, or wait until after the next steps)
- Next click Change Log Detail Levels.
- Clear the trace string in the text box. Replace it with the following:
*=info:SecurityDomain=all:com.ibm.ws.security.*=all:com.ibm.websphere.security.*=all:com.ibm.websphere.wim.*=all:com.ibm.wsspi.wim.*=all:com.ibm.ws.wim.*=all - Click OK (or Apply), and Save.
- Clear the trace string in the text box. Replace it with the following:
- Stop the server
- Delete or rename all the logs in the profile_home/logs directory.
By clearing the logs before restarting and then re-creating the issue, you will have a fresh and concise set of data to review, or otherwise provide to IBM Support - Next, restart the WebSphere Application Server instance
- Reproduce the problem
The resulting traces should contain one of the following errors if the issues are occurring
- java.security.InvalidKeyException: Illegal key size
- No key of type: 23
Resolving The Problem
https://www.ibm.com/support/pages/node/6431271
klist tickets
If you see, KerbTicket Encryption Type and Session Key Type are the same, a newly generated keytab file (with AES256-SHA1 only) is required.
Client: websphereadmin @ WASSEC-L2.LOCALServer: HTTP/waskdc1.wassec-l2.local/wassec-l2.local @ WASSEC-L2.LOCALKerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalizeStart Time: 11/30/2022 11:18:03 (local)End Time: 11/30/2022 21:18:03 (local)Renew Time: 12/7/2022 11:18:03 (local)Session Key Type: AES-256-CTS-HMAC-SHA1-96Cache Flags: 0Kdc Called: kdc1.wassec-l2.local
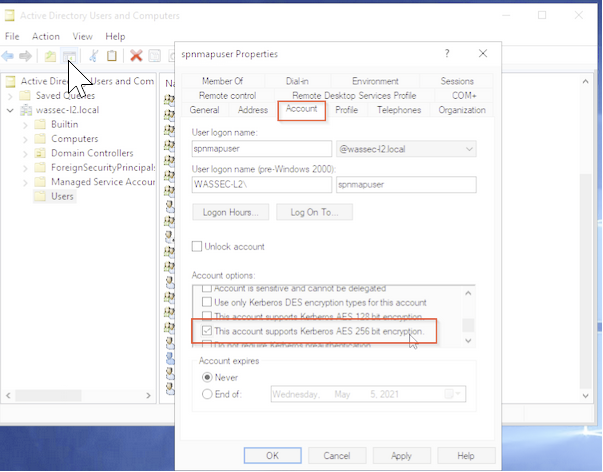
Please make sure the following configuration and AD side.
For the Mapped SPN account, please use higher encryption keys, check the option “This account support AES 256 encryptions” in user properties, and Reset the password.
For example, please see the following screenshot.
ktpass -princ HTTP/servera.ibm.com@WASSEC-L2.LOCAL -ptype KRB5_NT_PRINCIPAL -mapUser spnmapuser -mapOp set -pass password123 -out c:\was-keytab\WASServer.keytab -crypto AES256-SHA1 +DumpSalt -kvno 0
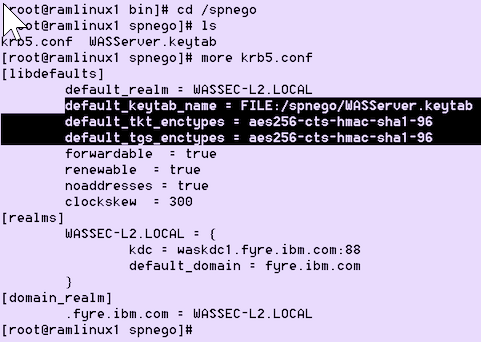
Ensure krb5.conf or krb4.ini Kerberos configuration file is configured with AES256 encryption type in WebSphere Application Server.
Issue 2, Different Encryption and Key Types:
If you see klist tickets as follows where KerbTicket Encryption Type as RC4-HMAC, and the Session Key Type as AES-256-CTS-HMAC-SHA1-96, you need to also generate a keytab, but with the argument -crypto All to workaround the issue.
Example entry seen in output from command klist tickets:
The command output shows in red that the encryption and key types differ.
Client: websphereadmin @ WASSEC-L2.LOCALServer: HTTP/waskdc1.wassec-l2.local/wassec-l2.local @ WASSEC-L2.LOCALKerbTicket Encryption Type: RSADSI RC4-HMAC(NT)Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalizeStart Time: 11/30/2022 11:18:03 (local)End Time: 11/30/2022 21:18:03 (local)Renew Time: 12/7/2022 11:18:03 (local)Session Key Type: AES-256-CTS-HMAC-SHA1-96Cache Flags: 0Kdc Called: kdc1.wassec-l2.local
Note: If you have further questions about ticket behavior, you need to work with your Microsoft Admin or Support for specifics as to why the tickets' KerbTicket Encryption Type and the Session Key Type differ in values
Please make sure the following configuration and AD side.
For the Mapped SPN account, please use higher encryption keys, check the option “This account support AES 256 encryptions” in user properties, and Reset the password.
For example, please see the following screenshot.

Example Command for ktpass
ktpass -princ HTTP/servera.ibm.com@WASSEC-L2.LOCAL -ptype KRB5_NT_PRINCIPAL -mapUser spnmapuser -mapOp set -pass Passw0rd@$# -out c:\was-keytab\WASServer.keytab -crypto All +DumpSalt -kvno 0
Ensure krb5.conf or krb4.ini Kerberos configuration file is configured with AES256 encryption type in WebSphere Application Server.

Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
21 February 2023
UID
ibm16845566