Release Notes
Abstract
MaaS360 adds usability improvements and significant security enhancements in the Security Dashboard. The widgets in the Security Dashboard are consolidated and arranged in a single layout so that the important information is immediately accessible at a glance. The detailed information about the affected devices in the Top risk incidents widget is displayed on new pages instead of a modal window.
MaaS360 adds the new Security Events widget in the Security Dashboard. This widget displays an aggregate view of all security events that were detected in the past 60 days. The security events are categorized based on whether a risk rule is configured for those events. MaaS360 uses separate color codes to clearly differentiate the events that have risk rules configured from the events that do not have risk rules configured in the MaaS360 Portal. Administrators can drill down to the Security Events page from this widget, where they can view the detailed summary of exposed devices, track the event types without risk rules, and enhance security by modifying the risk rules or configuring new risk rules. Administrators can also track the top 5 event types without risk rules that contributed to the most security events in their organization.
These enhancements allow administrators to identify security vulnerabilities in their organization and help them make informed decisions such as configuring risk rules and updating policy settings.
Content
Understanding the terminology
- Security events - Raw incidents that are detected by MaaS360.
- Risk incidents - The security events that violate risk rules configured in MaaS360.
Usability improvements
MaaS360 consolidates the following widgets:
- The Top Users with Risk Incidents widget displays both Users with risk incidents and Top risky users under two separate tabs.
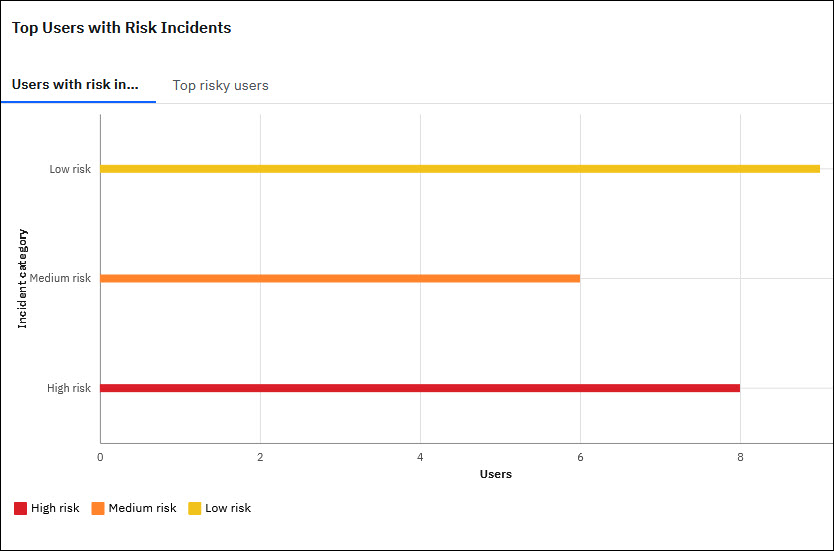
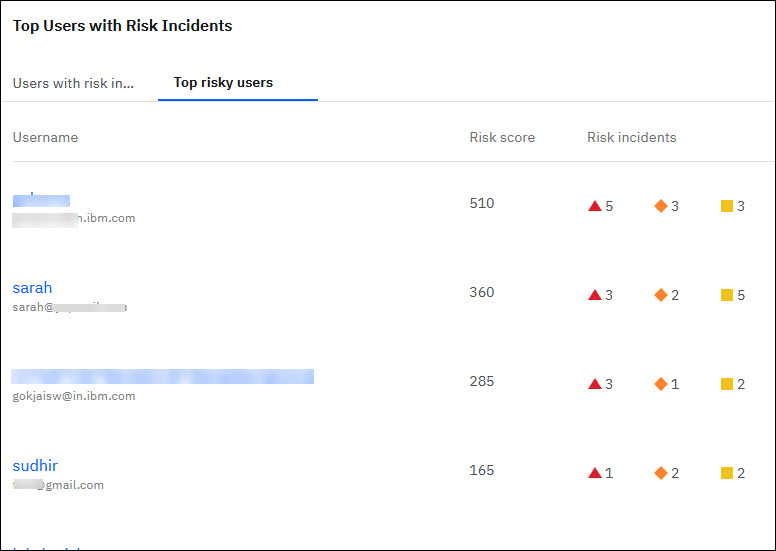
- The Risk incidents widget displays both Risk incidents and Top risk incidents under two separate tabs.
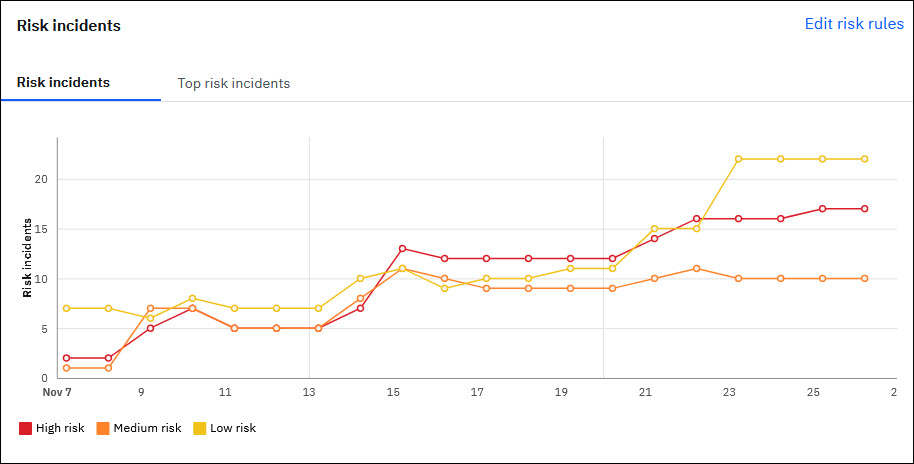
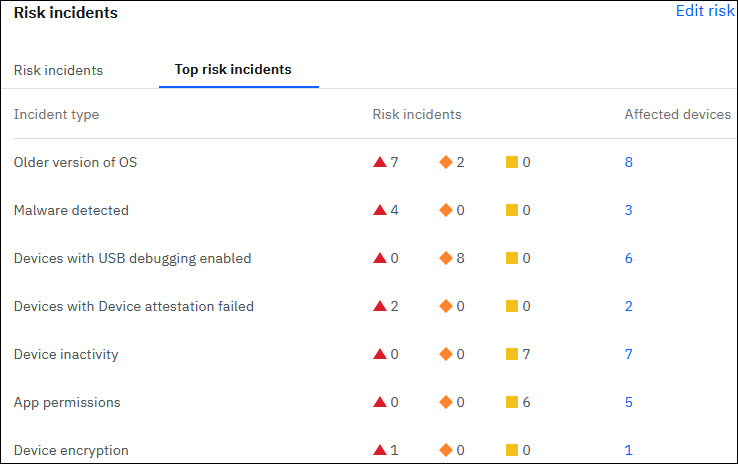
Dedicated pages to show devices exposed to risk incidents
MaaS360 now displays a detailed summary of devices affected by each risk incident on a separate page. For example, administrators can view detailed information about the devices that are exposed to the Malware risk on a separate page. When administrators click affected devices in the Top risk incidents widget, MaaS360 displays an overview of devices affected by the risk incident on the corresponding risk incident page.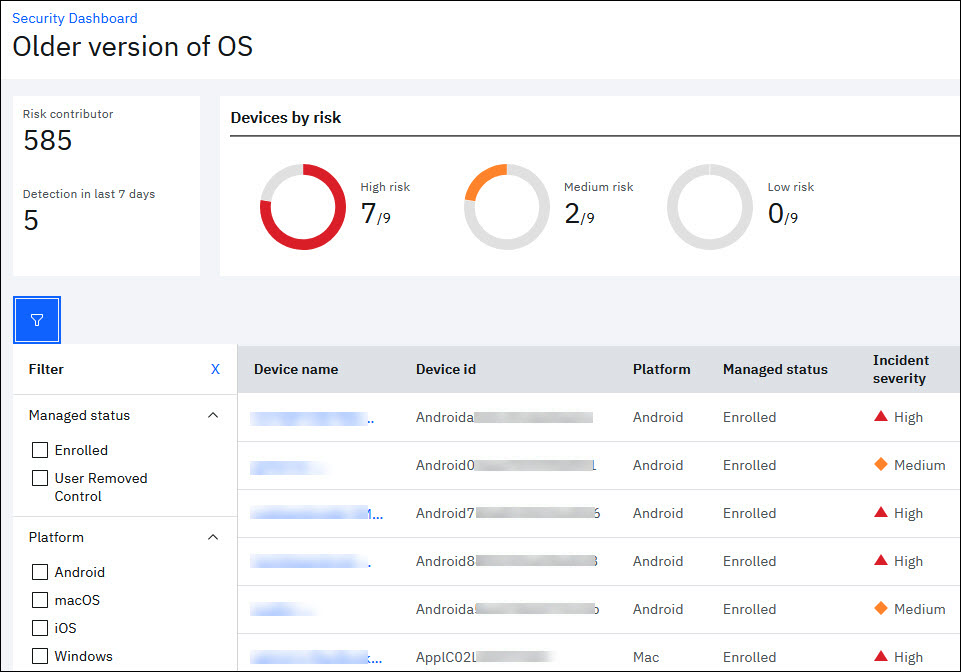
Administrators can use this page to:
- Track the overall risk contribution score and the number of threats detected for the selected event type over the past 7 days.
- View the detailed breakdown of devices by their risk severity levels and also identify the number of devices that contribute to each risk level: High, Medium, and Low. For example, 7 out of 9 devices contribute to High risk.
- Filter affected devices based on the managed status of the device, platform, severity level, and date range.
- View detailed summary information about each affected device, such as Device Name, ID, Platform, Incident Severity, and Username.
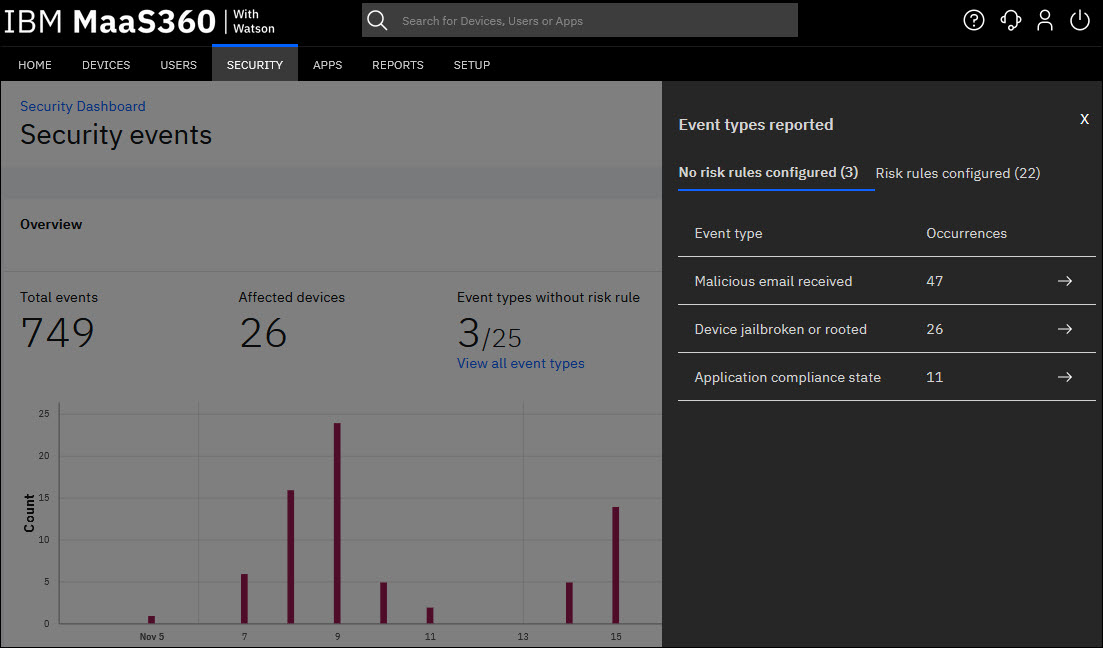
New Security Events widget
This widget displays an aggregate view of all security events detected in the past 60 days. The security events are categorized based on whether a risk rule is configured for those events. Administrators can hover over the Security Events bar in this widget to view the total number of security events in each category. MaaS360 uses separate color codes to clearly differentiate the events that have risk rules configured from the events that do not have risk rules configured in the MaaS360 Portal.
In the Top event types without risk rules section, MaaS360 displays the top 5 event types without risk rules that contributed to the most security events. The order of event types displayed in this list is based on the number of devices impacted by security events.
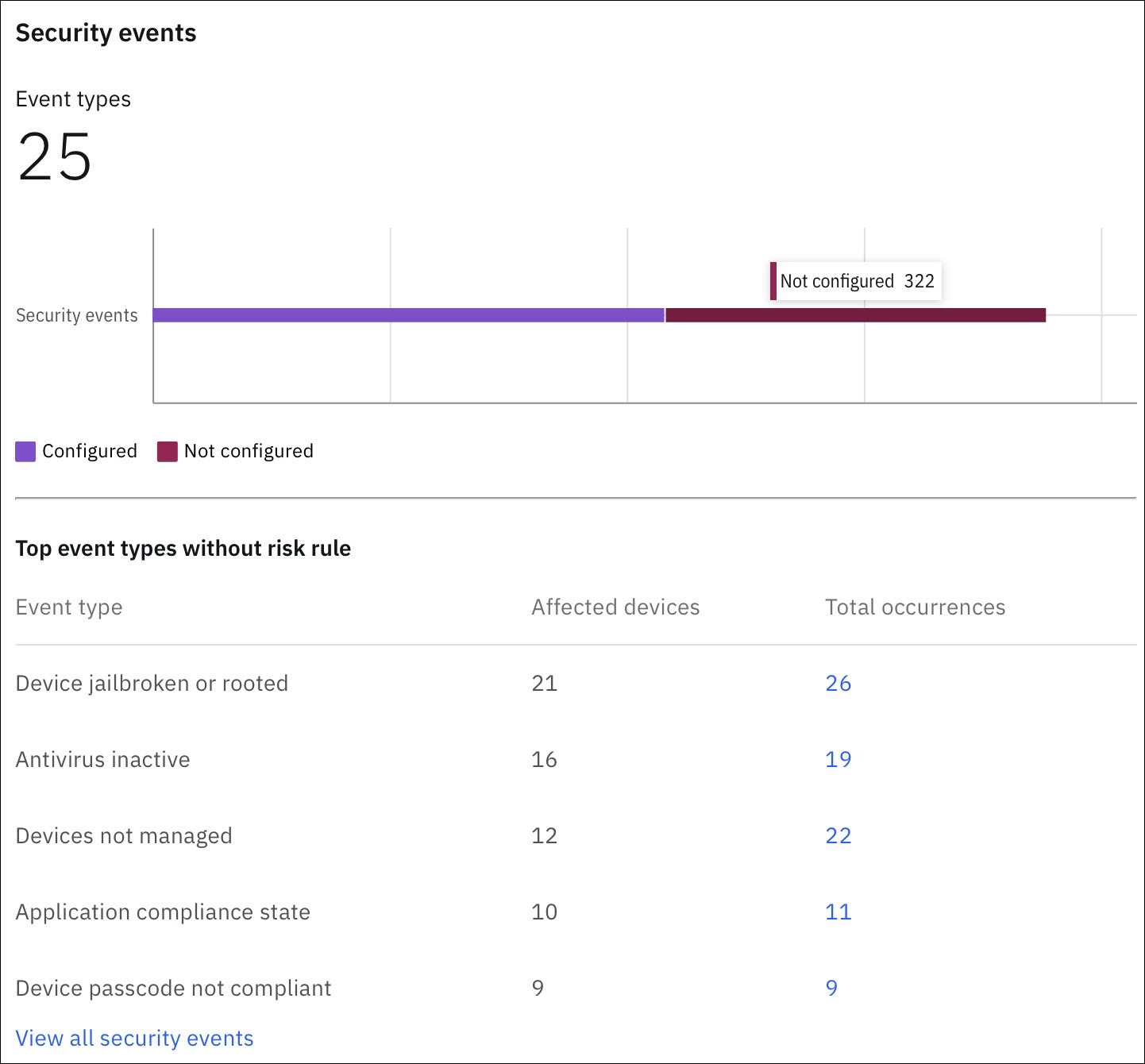
Viewing all the security events
MaaS360 displays an overall view of all the security events detected in your organization on the Security events page.
Note: Data for inactive devices in the MaaS360 Portal is not displayed on the Security events page.
Administrators can use the Security events page to:
- View information about all the security events in a centralized location.
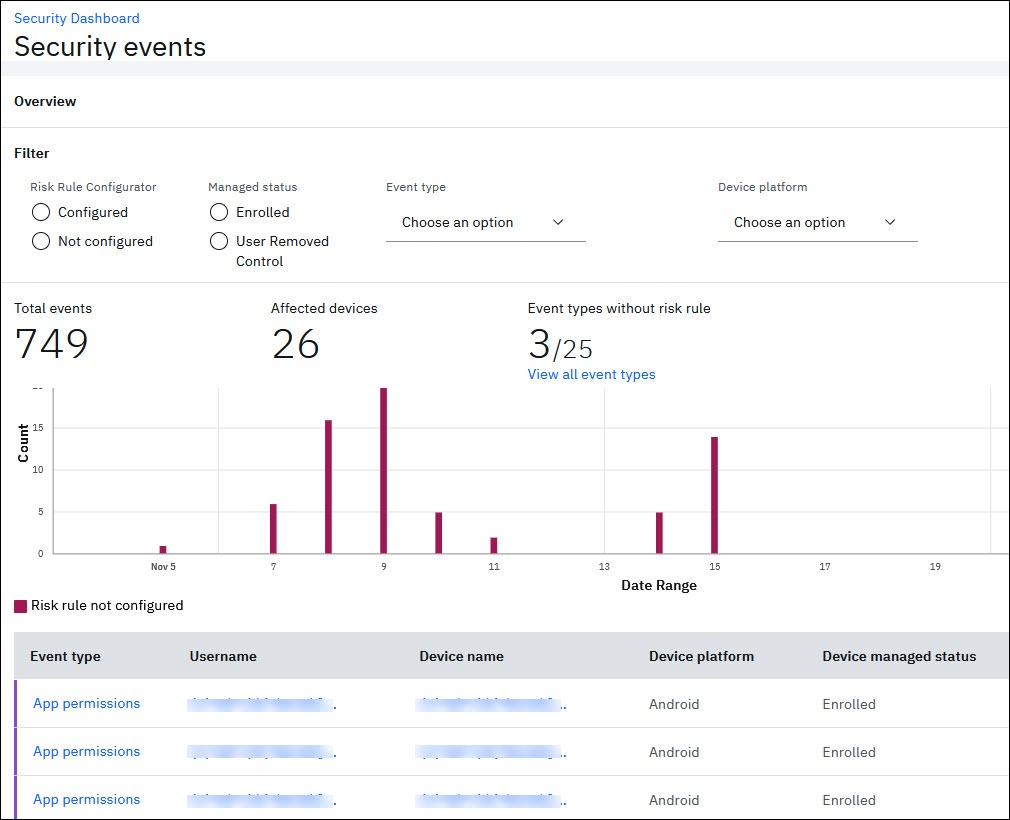
- Identify the security events that do not have a risk rule configured based on the color codes.
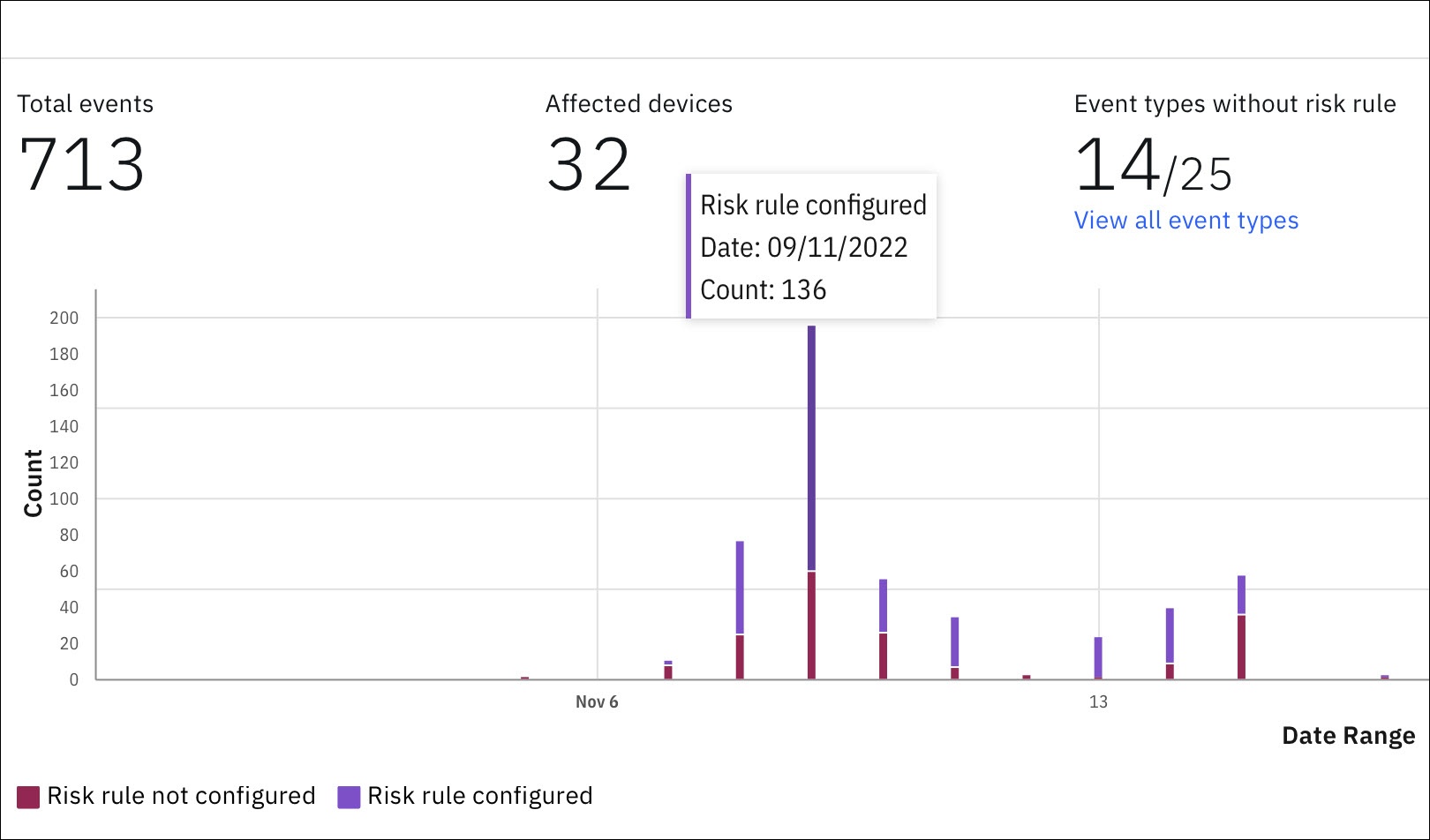
- View the detailed summary of exposed devices including event type, username, device name, platform, device managed status, and the time of detection.
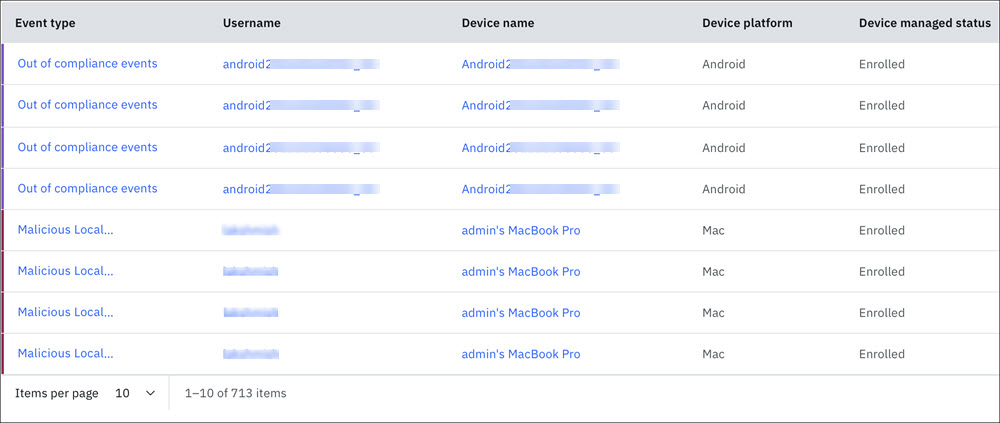
- Filter security events to narrow down the exposed devices list based on risk rule configuration, managed device status, event type, platform, and date range.
- Use the event type, username, and device name hyperlinks to easily navigate to the corresponding detail view page.
-
Track all event types in one place. The event types are categorized into two separate sections: No risk rules configured and Risk rules configured. In each section, MaaS360 displays the number of security event occurrences detected against each event type.
-
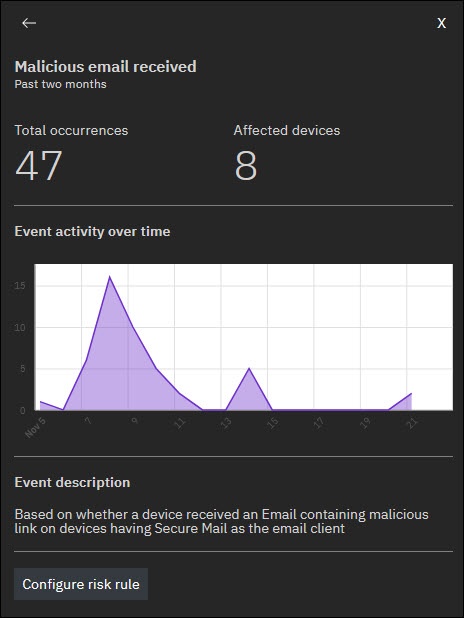
Administrators can click the arrow mark next to each event type to view detailed information about that event type. In the detailed view page, MaaS360 displays the number of exposed devices and occurrences.
For event types without a risk rule, MaaS360 displays the Configure risk rule. Clicking on this button redirects administrators to the Risk Rule Configurator page, where they can configure the risk rule for the corresponding event type.
Note: The new risk rules affect future events only.
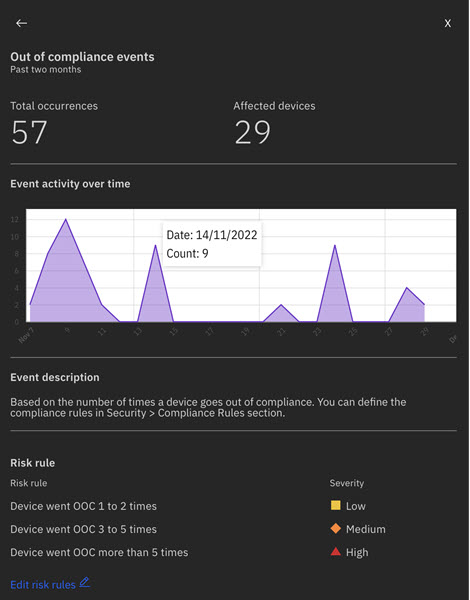
For event types with a risk rule, MaaS360 displays the existing risk rule and its severity. Clicking on this button redirects administrators to the Risk Rule Configurator page, where they can edit the risk rule severity and threshold for the corresponding event type.
Why should you configure risk rules?
If risk rules are configured, a risk incident is created in the MaaS360 Portal when a violation is detected. MaaS360 validates all risk incidents against your risk rules to calculate the severity and risk score for devices and users. As a security analyst, you can view the overall risk score, average risk score trend, and the list of applications, users, and devices that pose a risk to your organization.
Was this topic helpful?
Document Information
Modified date:
01 December 2022
UID
ibm16843119