Troubleshooting
Problem
If you change the encryption keys of the database at the same time when you upgrade Manage, you may encounter error reported by the Manage operator:
"Invalid keys: Encryption keys do not match what database uses."
Symptom
"Invalid keys: Encryption keys do not match what database uses." occurs on the ManageWorkspace custom resource status screen on Red Hat OpenShift.
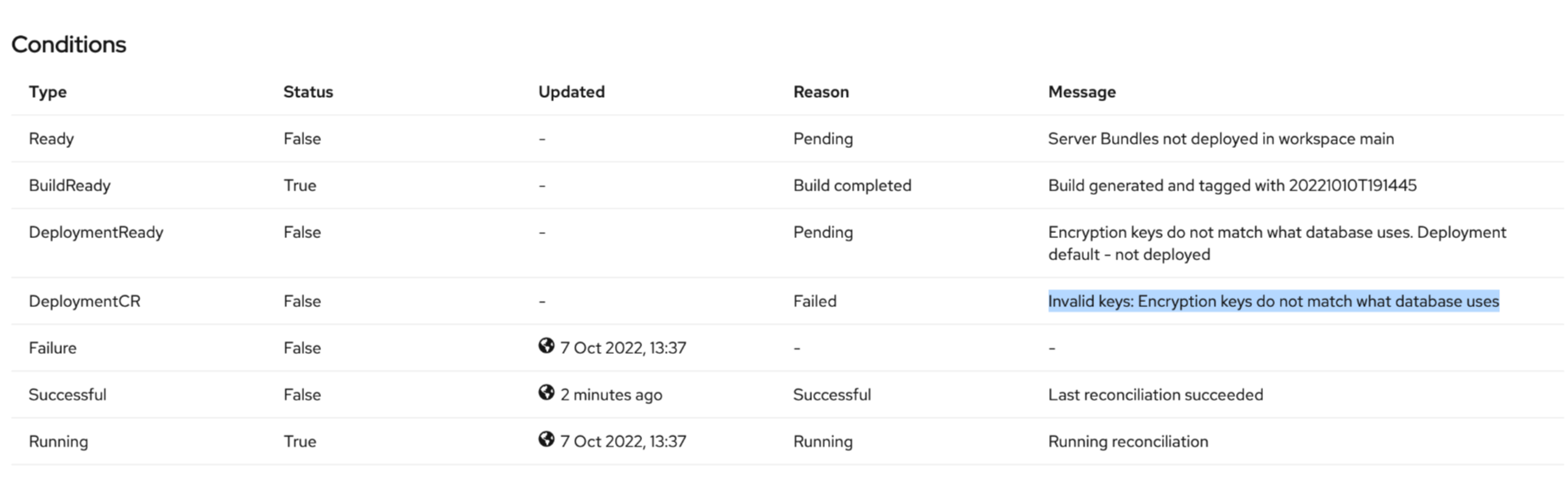
The same error message is displayed on Maximo Application Suite's Manage deployment screen.
However, the re-encryption is shown to be done successfully. The Manage admin server (maxinst) pod log displays:
The operator does not recover from this error and the operator attempts reconciling repeatedly.
Cause
The problem happens when the re-encryption of the database is followed by an update DB process in the same reconcile cycle of the Manage operator. The re-encryption finishes correctly, however, the admin server (maxinst) pod isn't restarted to reflect the new encryption keys. As the result, the validation routine before the database upgrade throws the error.
Diagnosing The Problem
Restart the admin server by locating the maxinst pod in Red Hat OpenShift and delete the pod. The maxinst pod will be re-created and the encryption value will reflect what is used after the successful re-encryption. If the encryption keys actually match the DB's, the problem is resolved and the operator continues with the database update.
If the problem persists, that means the old encryption keys specified in the encryption secret do not match to the database and the re-encryption has failed.
Resolving The Problem
When this problem happens, if you have direct access to the Red Hat OpenShift environment, locate the maxinst pod and delete the pod. The pod will be restarted reflecting the correct encryption keys. The operator continues to reconcile and is able to pass the validation check and continue the DB update process.
To avoid this problem from happening, simply do not mix encryption key change with other changes such as upgrading the database. Only make changes to encryption secret in order to re-encrypt the database after other changes have taken effect and the operator are reporting "ready" status.
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB59","label":"Sustainability Software"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSRHPA","label":"IBM Maximo Application Suite"},"ARM Category":[{"code":"a8m3p000000hAeaAAE","label":"Maximo Application Suite-\u003EMAS Applications-\u003EManage"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"8.5.0"}]
Was this topic helpful?
Document Information
Modified date:
22 November 2022
UID
ibm16840593