News
Abstract
QRadar Support and Development teams are announcing an upcoming end of life for WMI-based Microsoft Security Event Log protocols on 31 October 2022. This announcement is specific to older QRadar protocol implementations that user WMI to collect events from Windows hosts. Administrators need to review and confirm whether you use the end of life protocols and migrate to either WinCollect or Microsoft Windows Security Event Log over MSRPC.
Content
Updates
- 22 September 2022: Initial release of this article to notify users of the upcoming change to mark WMI-based event collection protocols for Microsoft Windows as end of life.
- 31 October 2022: The Windows Event Log protocol is considered end of life by IBM development. The final versions are posted to IBM Fix Central to display WMI-based Windows protocols as end of life in the QRadar Log Source Management app. An auto update is pending to install the following final release versions:
- PROTOCOL-WindowsEventLog-7.4-20220516182420.noarch.rpm
- PROTOCOL-WindowsEventLog-7.5-20220516182406.noarch.rpm
Notice: The Windows Event Log (WMI) protocol is officially end of life. Users who experience issues with WMI-based log sources need to convert their log sources over to WinCollect or Microsoft Security Event Log over MSRPC. No further code changes or updates are expected for the Windows Event Log (WMI) protocol.
Important: QRadar® development is deprecating two WMI-based protocols for the Microsoft Windows Security Event Log protocol. A QRadar auto update is pending to alert users to this change by marking two protocols as end of life in the user interface. Users who have log sources with affected protocol types must convert the log sources to use a supported protocol option, such as WinCollect or Microsoft Security Event Log over MSRPC.
- Microsoft Windows Security Event Log - End of life 31 October 2022
- Microsoft Windows Security Event Log Custom - End of life 31 October 2022
Example
Figure 1: Example of Microsoft WMI protocol types announced as end of life.
End of life and support
Administrators with enabled end of life protocol after 31 October 2022 can expect the following:
- QRadar Support can take cases on end of life protocols, but limited troubleshooting is available. Administrators who experience issues might be required to convert their log source from the WMI-based protocol to a supported protocol type, such as WinCollect (Syslog) or Microsoft Security Event Log over MSRPC.
- No further code releases or fixes from development teams for deprecated protocols.
- No APARs or known issues are created for deprecated protocols.
Administrators can verify whether you have log sources configured that use deprecated protocols in the Log Source Management app. After 31 October 2022, QRadar auto updates and legacy protocols are marked (End of life) in the user interface.
- Log in to the QRadar Console as an administrator.
- Click the Admin tab.
- Click the Log Sources icon.
- Review the Protocol Type list to determine you have end of life protocols enabled for your log sources.
- Protocol type list before 31 October 2022

Figure 2: The screen capture highlights two protocols that are planned for End of life after 31 October 2022. - Protocol type list after 31 October 2022

Figure 3: In this example, the Console has two affected protocols in use collecting events marked End of life in the user interface.
- Protocol type list before 31 October 2022
- Enabled Microsoft Security Event Log or Microsoft Security Event Log Custom log sources must be converted to a supported protocol, such as WinCollect (Syslog) or Microsoft Windows Security Event Log over MSRPC.
Results
Log sources that poll for important security events can be disabled. If you need to search for these events or possibly audit the Windows hosts in the future, do not delete the log sources. Deleting log sources removes pointers to the log source names or types, which can make the event data harder to search. A good practice for administrators is to create your new WinCollect (Syslog) or Microsoft Windows Security Event Log over MSRPC log source, confirm they collect events successfully, then disable the WMI-based log sources and move them in to a Decommissioned log source group.
Migrating your log sources
Select one of the following options to create a WinCollect Syslog or Microsoft Windows Security Event Log over MSRPC log source:
Option A: Configuring a WinCollect log source
Administrators who want to collect events from Security, Application, System, DNS, File Replication, and other files within the Microsoft Event Viewer can install a stand-alone WinCollect 10 agent on your Windows host.
Procedure
- Download WinCollect 10 from IBM Fix Central: https://ibm.biz/getwincollect10
- Double-click the installer to begin the installation.
- In the Welcome to the IBM 64-bit Setup Wizard window, click Next.
- Accept the EULA and click Next.
- In the Installer Options window, select Quick.
The Quick installation option configures the agent to collect Security, System, and Application events.
- In the Destination Input window, type the Hostname of the QRadar appliance you want to send your WinCollect events to, and click Install.
- Wait for the installation to complete.
- Click Finish to close the installer.
Results
You can verify a new log source is auto discovered from your WinCollect agent that sends Syslog events to QRadar. WinCollect log sources that auto discover in QRadar are listed with a name WindowsAuthServer @ {hostname}. You can click the menu for the log source to search and review incoming events. For example,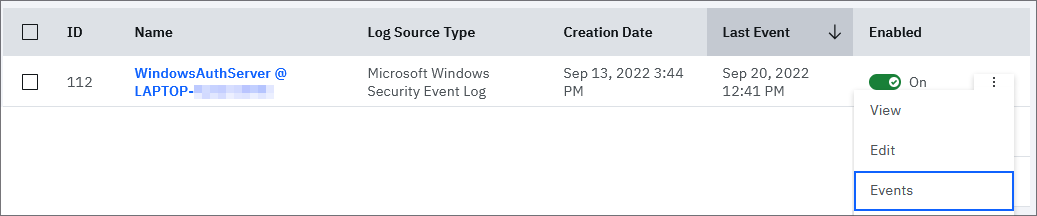
Figure 4: Use the Events drop-down to quickly display events from the last 5 minutes for your log source.
The Log Activity tab is filtered to display the latest.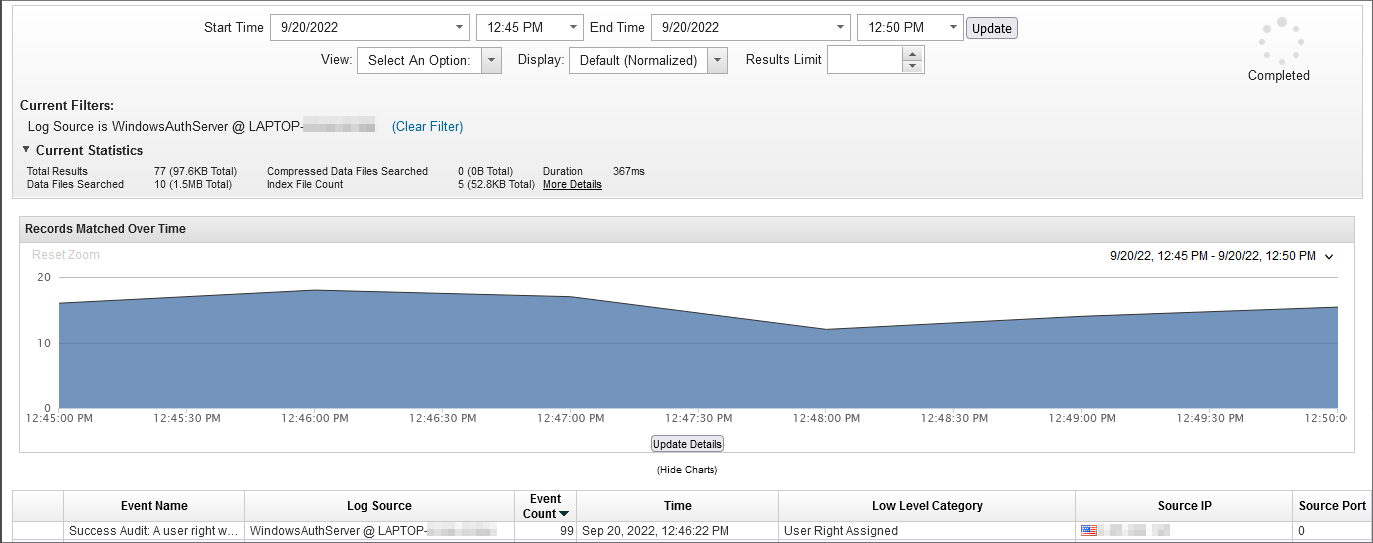
Figure 5: Example search that displays the last 5 minutes of events on the Log Activity tab.
Option B: Configuring an MSRPC log source
MSRPC protocol log sources for the Microsoft Windows Security Event Log allows users to remotely poll for events over MSRPC. The protocol leverages Microsoft's implementation of DCE/RPC, which is commonly referred to as MSRPC. The MSRPC protocol offers agentless, encrypted event collecting that provides higher event rates than the default 'Microsoft Windows Security Event Log' end of life protocol, which uses WMI/DCOM for event collection.
Before you begin
The following services and ports must be enabled to remotely poll for event data from Windows hosts over MSRPC.
|
Windows port requirements
|
You must ensure that external firewalls between the Windows host and the QRadar appliance are configured to allow incoming and outgoing TCP connections on the following ports:
|
|
Windows service requirements
|
The following services must be configured to start automatically:
|
|
Log source permissions
|
The log source user must be a member of the Event Log Readers group. If this group is not configured, then domain admin privileges are required in most cases to poll a Windows event log across a domain. In some cases, the Backup operators group can also be used depending on how Microsoft Group Policy Objects are configured.
The log source user must have access to following components:
|
Procedure
- Log in to the QRadar user interface as an administrator.
- Click the Admin tab.
- Click the Log Sources icon.
- Create a new log source.
- Select a Log Source type, Microsoft Windows Security Event Log.
- Select the protocol type, Microsoft Windows Security Event Log over MSRPC.
- Provide a name for the log source.
- Configure the protocol parameters, such as Log Source Identifier, domain, credentials, and event log types. For more information, see MSRPC log source configuration parameters.
- Click Next to test your MSRPC log source.
Results
Review the output of your MSRPC log source test. If you fail a test, you can enable debug to get detailed information on why the log source test did not retrieve events as expected. If a log source test did not pass, you can update parameters for your log source without needing to save a change. This allows users to update field, run tests, then save the log source changes. You only need to save your changes after the protocol passes all configuration tests.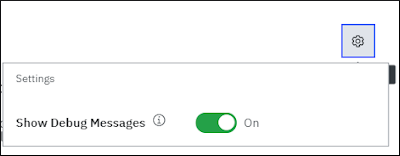
Figure 6: Enabling debug can provide detailed error messages for log sources that fail to collect events.
Was this topic helpful?
Document Information
Modified date:
09 February 2023
UID
ibm16616223