Troubleshooting
Problem
This document describes how to configure the TLS FTP client.
Resolving The Problem
This document describes how to configure the TLS FTP client.
TLS FTP uses digital certificates to encrypt data end to end. Passwords, FTP subcommands, and the data transferred are all encrypted by this means. For the connection to be established the IBM i needs to trust the Certificate Authority (CA) certificates that have signed the remote server certificate. To establish this trust, we will need to import the CA certificate signature chain into the *SYSTEM store. This import can be done using two different methods:
TLS FTP uses digital certificates to encrypt data end to end. Passwords, FTP subcommands, and the data transferred are all encrypted by this means. For the connection to be established the IBM i needs to trust the Certificate Authority (CA) certificates that have signed the remote server certificate. To establish this trust, we will need to import the CA certificate signature chain into the *SYSTEM store. This import can be done using two different methods:
STEP 1: Importing the CA Using Digital Certificate Manager for i
The CA will be imported using Digital Certificate Manager for i (which is part of the HTTP ADMIN server). Do the following:
Automatic Retrieval (Recommended)
Our QMGTOOLS/GETSSL utility has the ability to connect to the remote server and extract the certificates from the connection. See the following for more details:
NOTE: The optional option in Step 3 can be used to automatically import the extracted CAs into the *SYSTEM store:
Port number = FTP port (often either 21 or 990)
Start TLS = Y
Protocol for start TLS = FTP
Auto import CA = Y
*SYSTEM store password = enter the *DCM *SYSTEM store password
If QMGTOOLS/GETSSL is not able to connect to retrieve the certificates, please use the Manual Import instructions.Manual Import
Request that the remote server side send you the Root CA/Intermediate CA certificates that have signed their server certificate (in BASE64 encoded format). These files typically will have a .cer or .crt file extension. These can be opened on the PC to view the certificate information.
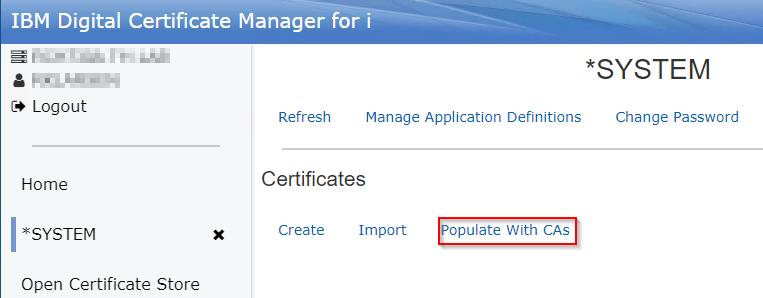
NOTE: Many of the well-known CA certificates used by remote servers are already provided on the system to import into the *SYSTEM store through the 'Populate with CAs' option:
The certificates shown in the 'Populate with CAs' list can be viewed by clicking the + on the right side of the tile. If it is a match to what the server side is using, check the box next to it and click 'Populate'. This will import the certificate into the store.
a. Open a Web browser, and type:
Non-Secure:
http://<system_name>:2006/dcm
TLS enabled:
https://<system_name>:2007/dcm
b. Sign on with a user ID that has *IOSYSCFG and *ALLOBJ authority.
c. Click 'Open Certificate Store:
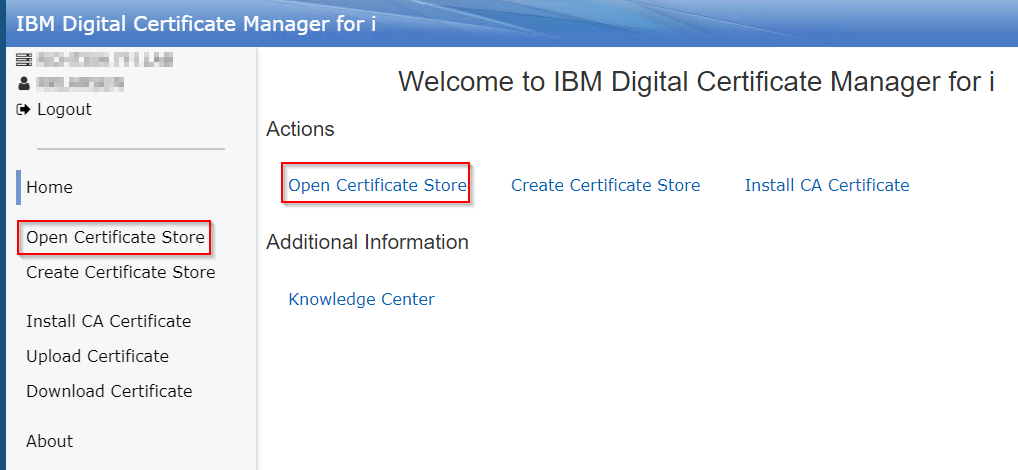
d. Click '*SYSTEM':
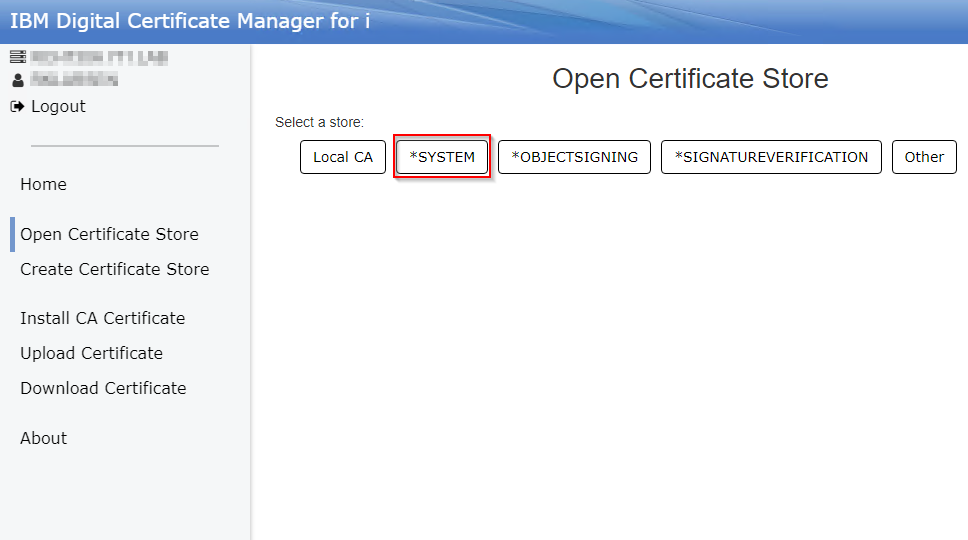
e. Type the password for the certificate store:
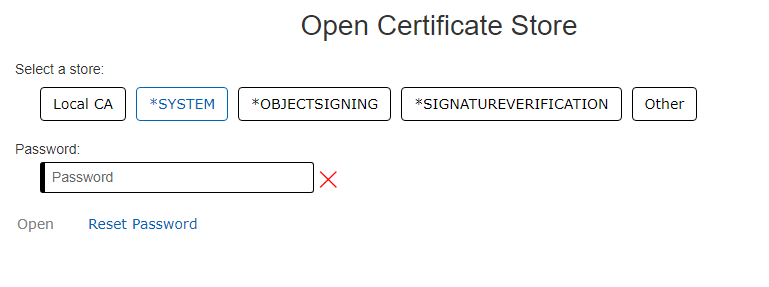
f. If the password is correct, you are now signed on and can import the CA using the following instructions:
NOTE: We will need to import the Root CA first, followed by the Intermediate CA. If you open the CA certificate on the PC the Root CA will have the same name for the 'Issued to' and 'Issued by'.
STEP 2: Configuring the FTP client application ID to trust the newly imported CAs.
a. In DCM click 'Manage Application Definitions' near the top of the screen:
a. In DCM click 'Manage Application Definitions' near the top of the screen:
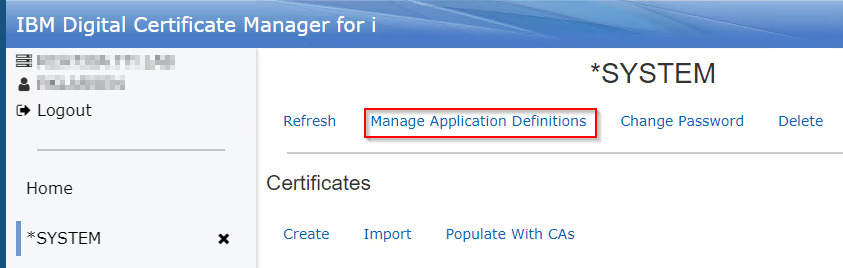
b. In the search box on the right type 'FTP':
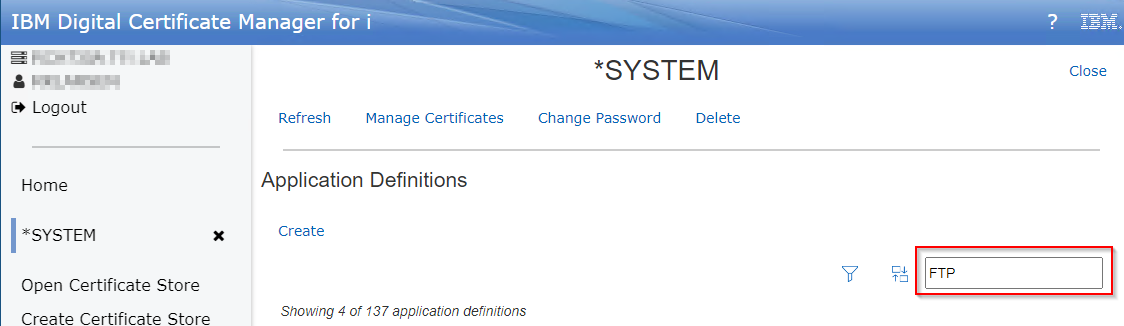
This will dynamically show just the application IDs related to FTP.
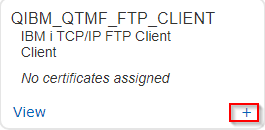
c. Locate the 'QIBM_QTMF_FTP_CLIENT' application ID and click the + in the lower right corner:
d. Click the 'Update' option:
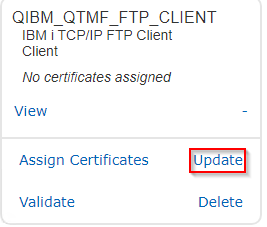
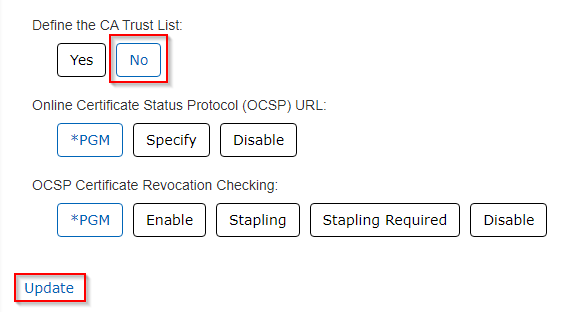
e. Scroll down to the bottom and set 'Define the CA Trust List' to 'No' (this will allow the application to trust all CAs in the *SYSTEM store), then click 'Update' at the bottom:
Only new jobs will be able to use this new configuration. This means that interactive sessions running batch jobs or persistent applications must be ended and started again to be able to use the changes made to the TLS FTP client.
[{"Type":"MASTER","Line of Business":{"code":"LOB68","label":"Power HW"},"Business Unit":{"code":"BU070","label":"IBM Infrastructure"},"Product":{"code":"SWG60","label":"IBM i"},"ARM Category":[{"code":"a8m0z0000000CLbAAM","label":"Communications-\u003EFTP"},{"code":"a8m0z0000000CISAA2","label":"Digital Certificate Manager"}],"ARM Case Number":"","Platform":[{"code":"PF012","label":"IBM i"}],"Version":"7.3.0;7.4.0;7.5.0"}]
Historical Number
425060441
Was this topic helpful?
Document Information
Modified date:
03 June 2024
UID
ibm16613797