Troubleshooting
Problem
CWWKS5041E: The expected RelayState parameter was not included in the SAML response message from the IdP
Symptom
When a user attempts to access the application that uses IdP initiated SAML-based SSO, a 403 forbidden error is returned from the following URL: https://hostname/ibm/saml20/errorMsg.jsp
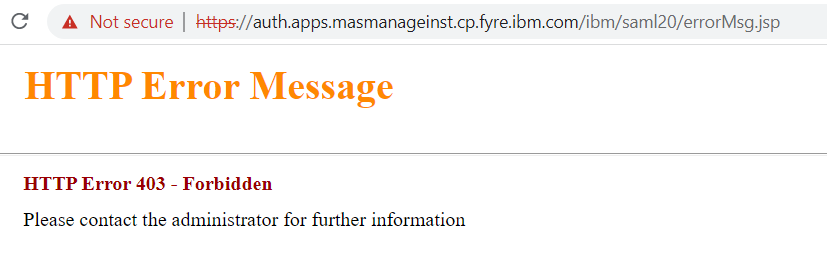
Cause
This is caused either due to the Default Relay State value in the identity provider SAML settings being incorrect or blank. This issue is only for MAS 8.7.2 and below versions. This is fixed in MAS 8.7.3 where if the user even keeps Default Relay State value blank, it is still valid and user will not get any error, considering all SAML configuration and setup in Identity Provider as well as in MAS admin SAML configuration is correct.
Diagnosing The Problem
This can be diagnosed by checking the coreidp pod's log (coreidp-xxxxxxxxx-xxxxx-coreidp.log) under the Manage instance and looking for
CWWKS5041E: The expected RelayState parameter was not included in the SAML response message from the IdP
Resolving The Problem
To resolve this, one needs to log in to their Identity Provider account, then go to the Application that is created and find its SAML settings. There, look for Default Relay State and set its required value, for example:
https://masinst.home.apps.masmanageinst.cp.fyre.ibm.com
You need to set your wanted URL here that you want to be get navigated to.
Then, save the configurations and launch the application from your Identity Provider account. It should navigate to the expected screen.
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB59","label":"Sustainability Software"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSRHPA","label":"IBM Maximo Application Suite"},"ARM Category":[{"code":"a8m3p000000hAeaAAE","label":"Maximo Application Suite->MAS Applications->Manage"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"8.7.0"}]
Was this topic helpful?
Document Information
Modified date:
11 July 2022
UID
ibm16602323