Security Bulletin
Summary
Watson Query is vulnerable to an internal attacker who can use an exposed administrator APIKEY to potentially alter system configuration or view customer data. The APIKEY is used to automatically create connections and assets to help reduce workload for the user. However, in some circumstances, due to CVE-2022-22410, the APIKEY is exposed to an internal user which can allow the attacker to alter system configuration or view customer data.
Vulnerability Details
DESCRIPTION: IBM Watson Query could allow an authenticated user to obtain sensitive information that would allow them to examine or alter system configurations or data sources connected to the service.
CVSS Base score: 3.9
CVSS Temporal Score: See: https://exchange.xforce.ibmcloud.com/vulnerabilities/222763 for the current score.
CVSS Vector: (CVSS:3.0/AV:N/AC:H/PR:H/UI:R/S:U/C:L/I:L/A:L)
Affected Products and Versions
Affected Products/Versions guidance:
| Affected Product(s) | Version(s) |
| IBM Watson Query with Cloud Pak for Data as a Service | All instances on or after December 1, 2021 |
About Vulnerability:
In Watson Query release made generally available on December 1, 2021, a feature was introduced to automatically create Platform connections. This feature reduces workload for the users and automates otherwise routine work.
This feature requires that the Watson Query service create a Service ID and associated APIKey when a user first logs on to the UI. To accomplish this, a new end point GET APIKEY was introduced. Due to CVE-2022-22410, this GET APIKEY endpoint inadvertently exposes administrator's key. An attacker can use this APIKEY to modify Watson Query catalog configuration or enable access customer data in certain configurations.
Watson Query Service has already remediated the exposure, however, to further secure the environment and customer's asset customers should take steps recommended in this document.
Remediation/Fixes
Since the API key was potentially exposed, you must delete the current API key and associated service ID, create a new service ID and associated API key, and replace both in the Watson Query service. A new service ID and API key are created automatically when you delete the current service ID and API key and then re-launch the Watson Query UI using the provisioning account or another account with the Platform Connections Admin role and Watson Query Manager role. The user is not required to re-create the new service ID and API key manually.
Additionally, there are two Catalogs that might be affected depending on your service configuration. You must make updates to the Platform assets catalog. See Step 2. You might also need to determine whether a primary catalog is enabled. See Step 1. And if a primary catalog is enabled, you must reselect it. See Step 3.
When the old service ID and associated API key are removed and replaced, the connections that were created with the old service ID and API key appear with the name “Not Available” and you will not be able to edit these connections. In Step 1, you will be asked to note these connections parameters so that you can remove them and recreate the connections using the new service ID in Step 4.
Should you run into difficulties or require assistance, please contact IBM Support Team for further assistance.
Step 1: Check primary catalog and connections:
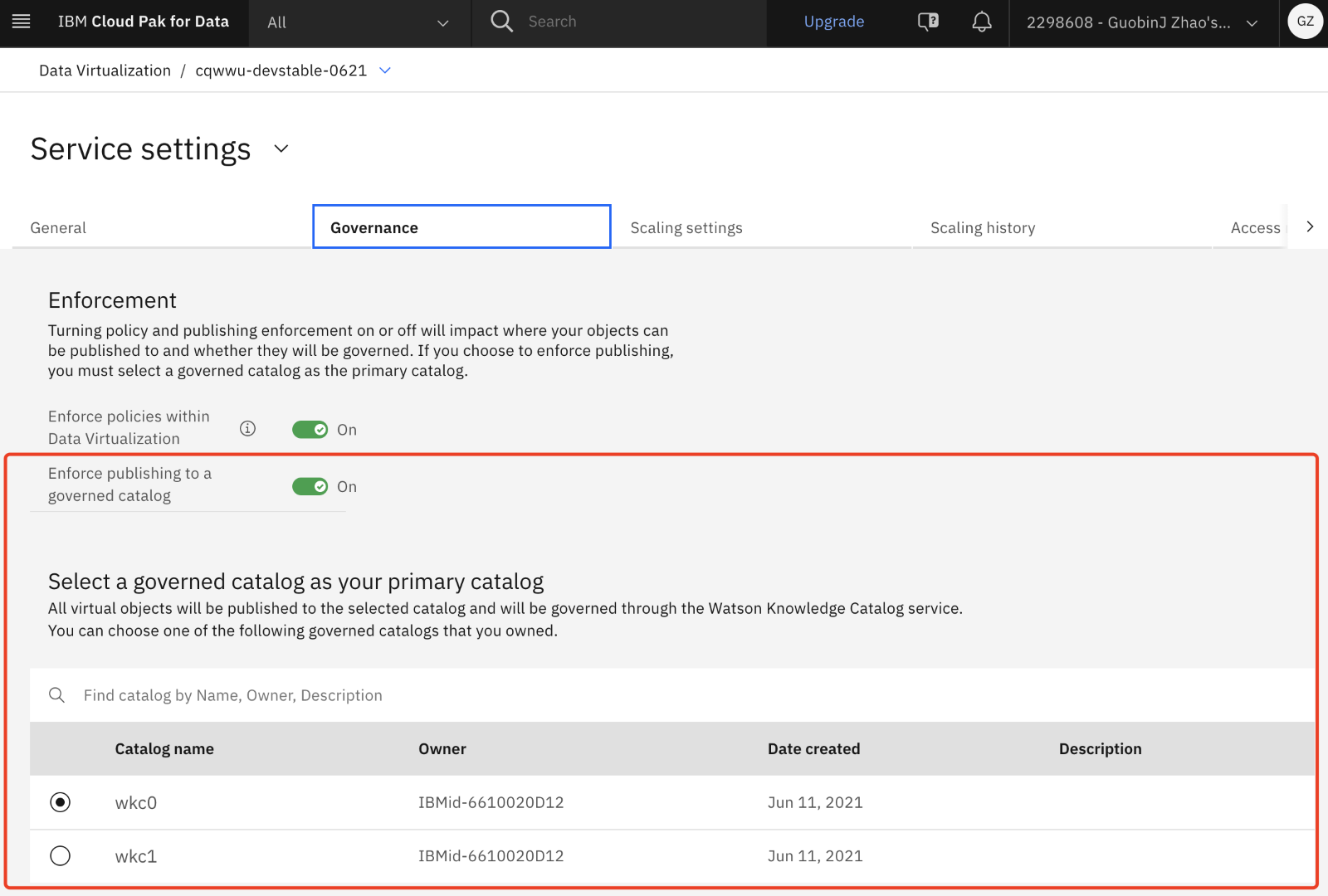
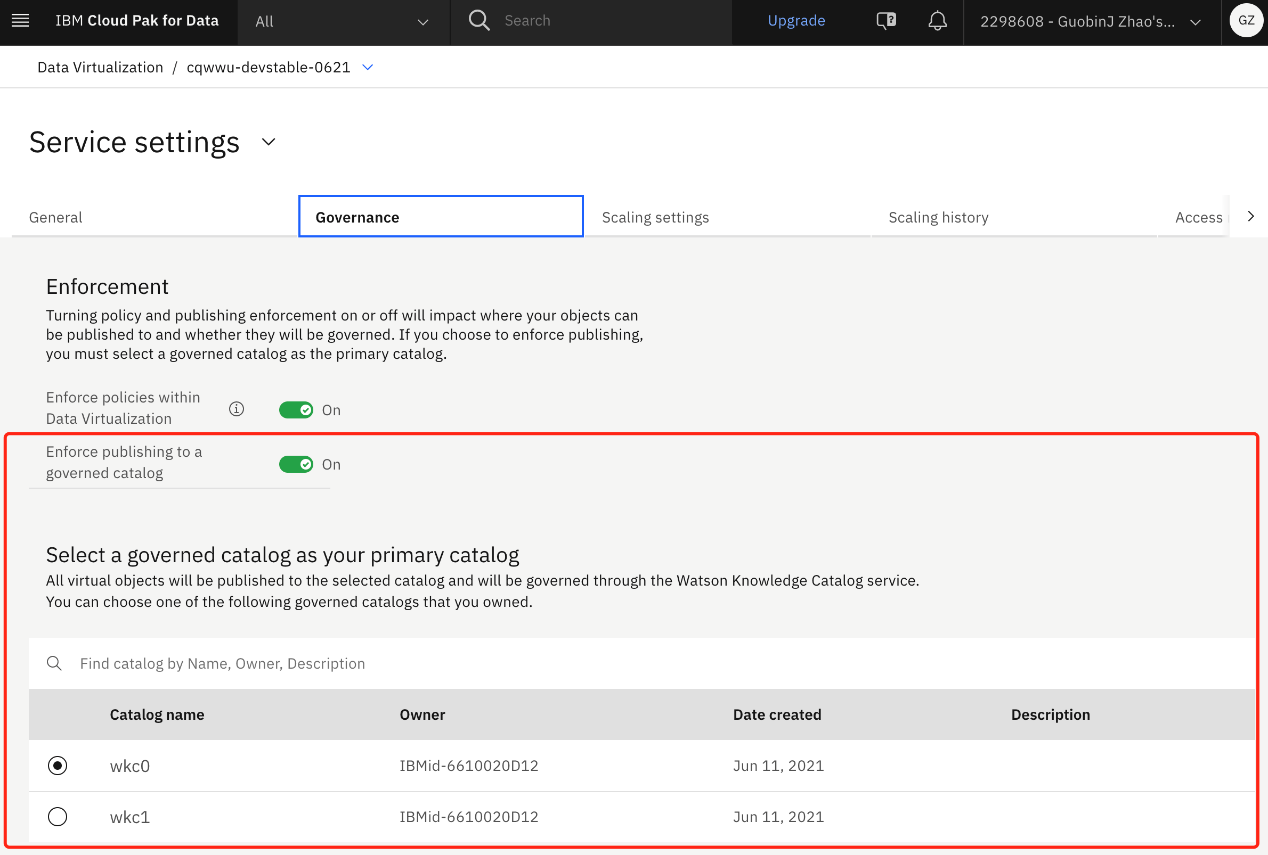
1. Check whether the primary catalog is enabled. If it is enabled, remember the primary catalog name, which will be used in Step 3. If it is not enabled, you don't need to do Step 3. Go to Data > Data virtualization > Service settings > Governance. If Enforce publishing to a governed catalog is checked, note the primary catalog name. For example, wkc0 in the following screenshot.
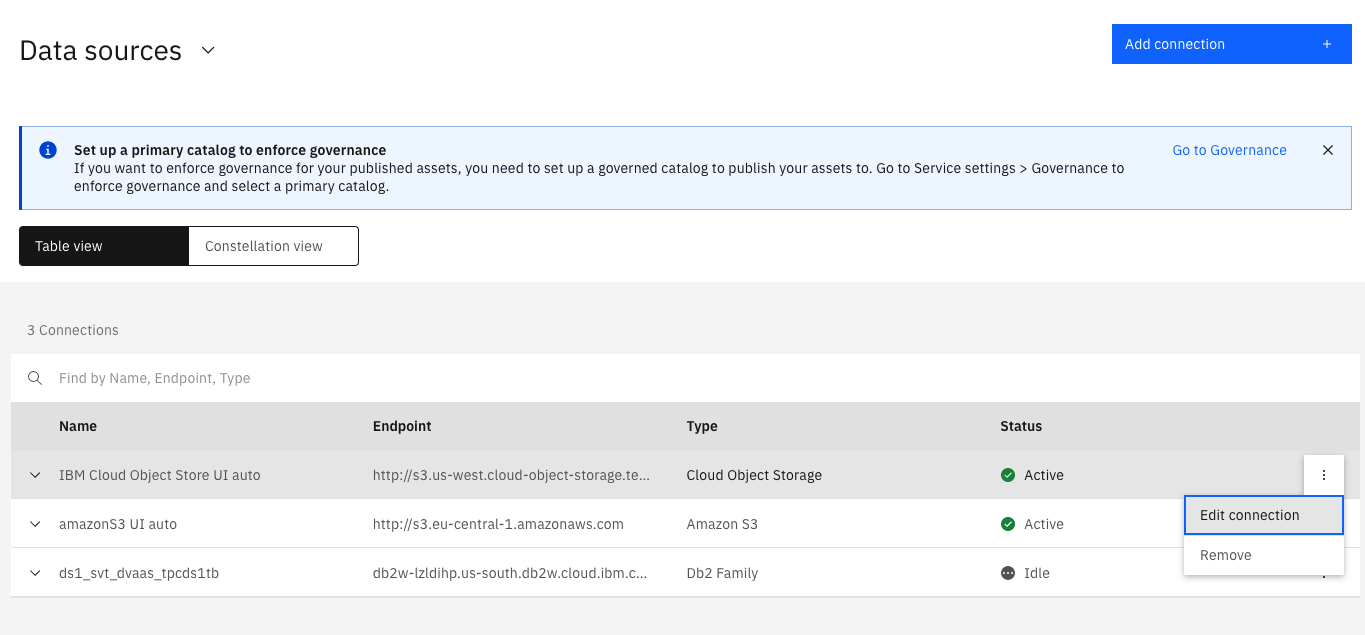
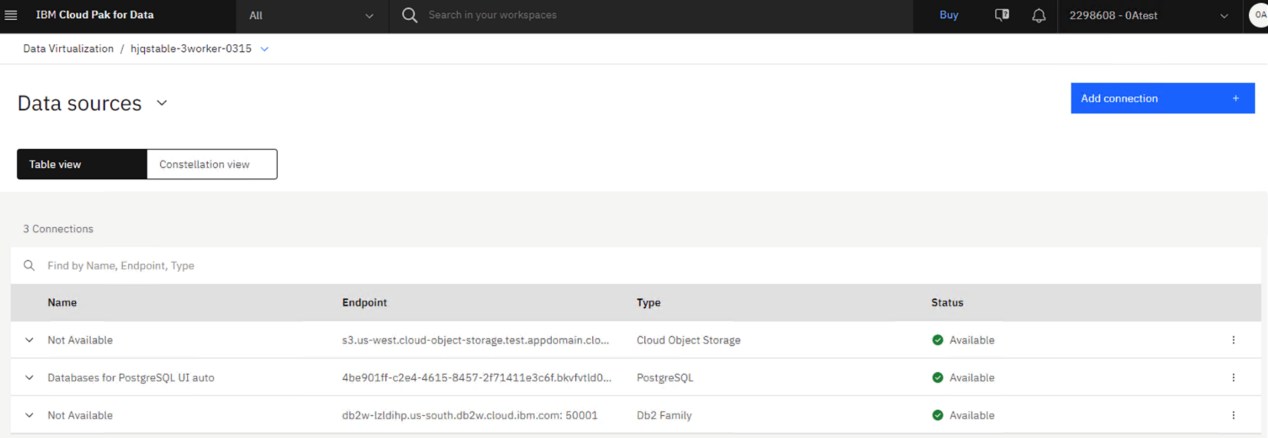
2. Go to Data > Data virtualization > Data sources. For each connection, click Edit connection in the overflow menu and note the connection parameters.
Step 2: For the Platform assets catalog:
1. In IBM Cloud > Manage > Access (IAM) > Service IDs, remove all Service IDs that are named Data Virtualization service ID for publish to Watson Knowledge Catalog.
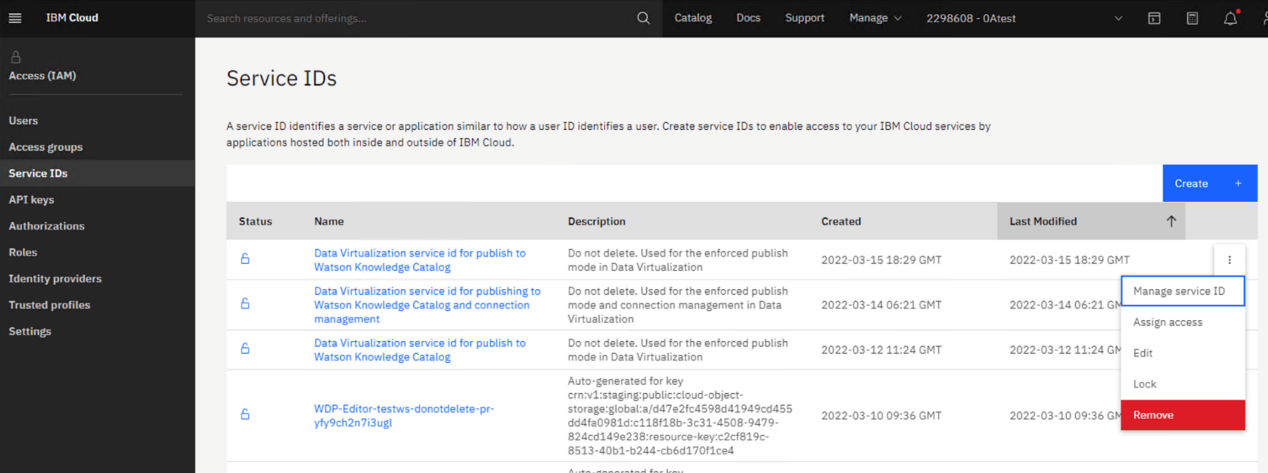
2. Review and validate all other Service IDs in this list that were created after December 1, 2021. Verify that the Service IDs are still valid.
3. Re-launch the Watson Query UI using the provisioning account or another account with Platform Connections Admin role and Watson Query Manager role. This step generates a new service ID, and the new service ID is added as a Platform connection collaborator.
4. Return to IAM and notice the new service ID named Data Virtualization service ID for publish to Watson Knowledge Catalog and connection management.
5. Go to Data > Platform connections > Access control and see that the Service ID (named Unavailable) is in the list of collaborators with the date added as when you re-launched the Watson Query UI.
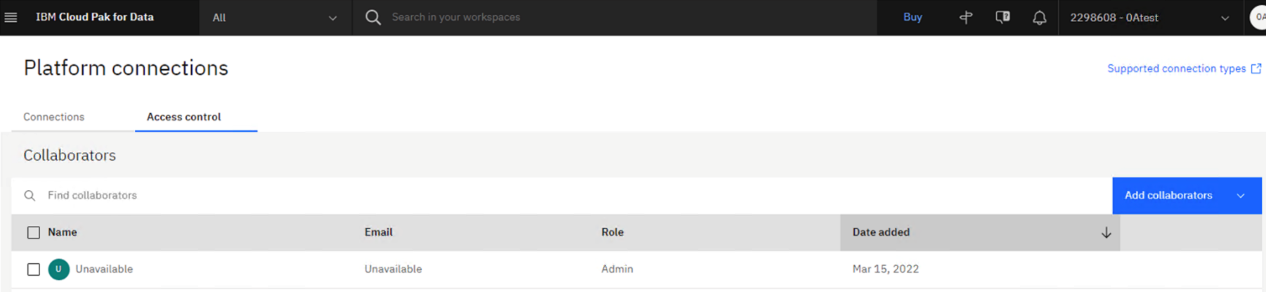
6. Review and validate all other Collaborators in this list that were created after December 1, 2021. Verify that the collaborators are still valid.
Step 3: For Watson Knowledge Catalog:
1. Go to Data > Data virtualization > Service settings > Governance and select the primary catalog name that was noted in Step 1. For example, in the screenshot below, you must select wkc0 catalog as the primary catalog.
2. Navigate to Catalogs > View all catalogs and find the primary catalog, for example, wkc0.
3. Click Access control and see that the Service ID (named Unavailable) is in the list of collaborators with the date added as when you re-selected the primary catalog.
4. Review and validate all other Collaborators in this list that were created after December 1, 2021. Verify that the collaborators are still valid.
5. Review all data source connection assets in your Platform Assets Catalog and Primary Catalog that use shared credentials. Change the password of those shared credentials.
6. After each password has been changed, review and validate all access this shared credential has to the data source.
Step 4: For connections (Optional):
This step is optional. You can complete most Watson Query tasks without connection names. If you want to edit connections, do the following step:
1. If connection names appear as “Not available” on the Data sources page, remove and recreate these connections using the connection parameters that were noted in Step 1.
Workarounds and Mitigations
None
Get Notified about Future Security Bulletins
References
Reference guidance:
Customers must follow these steps to remediate the vulnerability.
Change History
30 Mar 2022: Initial Publication
*The CVSS Environment Score is customer environment specific and will ultimately impact the Overall CVSS Score. Customers can evaluate the impact of this vulnerability in their environments by accessing the links in the Reference section of this Security Bulletin.
Disclaimer
Review the IBM security bulletin disclaimer and definitions regarding your responsibilities for assessing potential impact of security vulnerabilities to your environment.
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
25 July 2023
UID
ibm16569235