How To
Summary
This article is intended to put together information related to how WinCollect agents work with QRoC (QRadar on Cloud).
Steps
What’s different
The first thing that you need to keep in mind is that managed WinCollect agents are not supported by QRoC that means that you need to use only stand-alone agents:
“Managed deployment is not supported in QRadar on Cloud environments. Customers who use IBM QRadar on Cloud must use stand-alone WinCollect agents. “
Second, you can send only the events to a Data Gateway, an Event Processor (EP), or Event Flow Processor (EPFP) that is a part of the deployment. If you want to send them directly to the QRoC Console, you can do it only by using TLS Syslog.
Note: Sending events directly to the Console might result in events not being queued. A Data Gateway, EP, or EPFP has the ability to queue events better.
How to send the events directly to the QRoC console
If you want to send events directly to the QRoC Console, you can do it by using only TLS Syslog, follow the next steps to successfully do it:
1. Add to the allowlist the WinCollect agent IP address:
Log in to your QRoC environment and open the Self-Service Management app, go to the Allow section, and enter the IP address (and mask) to allow the connection.
2. Create the log source:
a. Go to the Log Source Management app and create the Log Source, you need to use the next configuration options:
- Log Source Type: Universal DSM
- Protocol Type: TLS Syslog
- TLS Listening port: 6514
- Authentication mode: TLS
- Certificate Type: Generated Certificate
b. Save and deploy the changes.
Notes:
During the configuration, you see a Test tab, this fails if you do not save and deploy the changes first.
This process opens port 6514 on QRoC.
3. Get the cert from IBM Support:
Open a case with IBM Support and request the next file /opt/qradar/conf/trusted_certificates/syslog-tls.cert from the QRoC console, this has to include -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----
This certificate looks like this:
-----BEGIN CERTIFICATE-----
MIIDITCCAgmgAwIBAgIJAPJsnrBOTkIzMA0GCSqGSIb3DQEBDQUAMCcxCjAIBgNV
<here you will see a long string>
2trDsZvwqpWSDjQAiHg+xO+eME0dyE3PILu6Z9WoAAEWcnWIXA==
-----END CERTIFICATE-----
This certificate works if you want to send any logs by using TLS Syslog to the QRoC console.
4. Create the Destination in the stand-alone WinCollect agent:
If you have doubts on how to install the WinCollect stand-alone agent, check the “How to install a stand-alone WinCollect agent” section on this article.
a. Open the Destination section on the WinCollect Configuration Console, and right-click Add New Destination: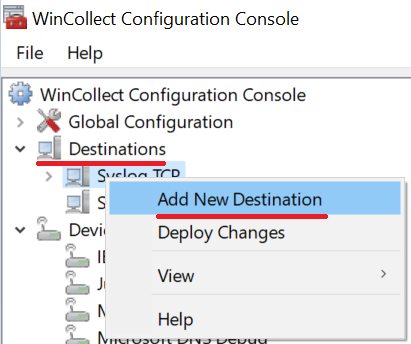
b. Add a name for this new Destination: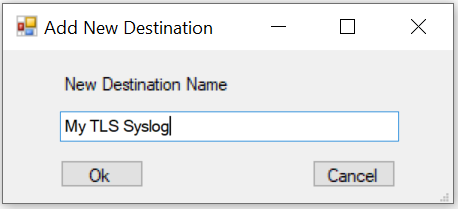
c. Click the new Destination: Destination > Syslog TCP > New Destination: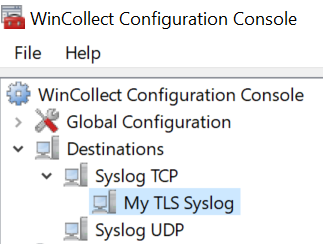
This opens the configuration for the destination:
-Hostname / IP: the Console QRoC IP address.
-Port: 6514
-Certificate (turns on TLS): Here you need to paste the cert you got from IBM support, make sure you do not leave spaces before or after.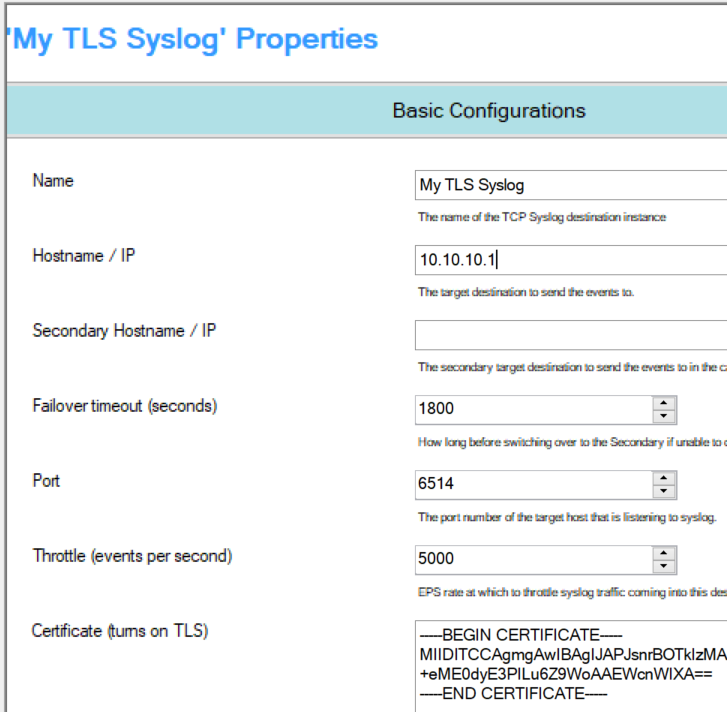
5. Create the Log Source in the WinCollect agent:
The entries to configure the log collection in the stand-alone WinCollect agent are named Devices: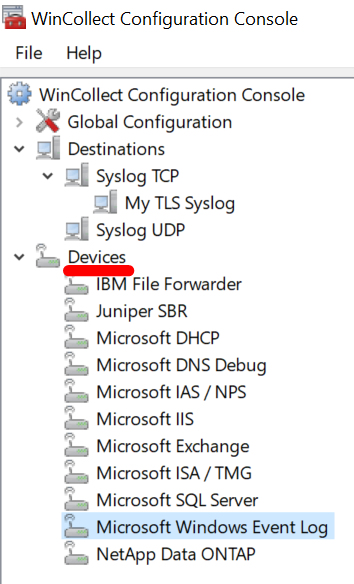
a. Right-click the Windows event type you want to monitor and add the configuration as you would do it in the Log Source Management app. Make sure you pick the Destination with the cert that you created in the previous step.
b. Once you are done, you need to deploy to apply the changes, you find the Deploy Changes option on the right upper part of the WinCollect Configuration Console: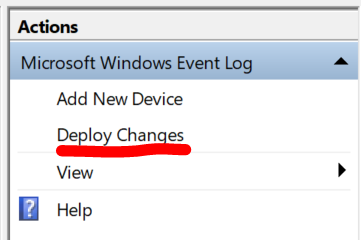
You are now able to see the events in QRoC.
How to get the events parsed when using TLS Syslog
TLS Syslog protocol is used to collect multiple event types and it does not parse your events. To get your Windows events parsed, you need to use the “Use As A Gateway Log Source” options after enabled it displays a new field named “Log Source Identifier Pattern”: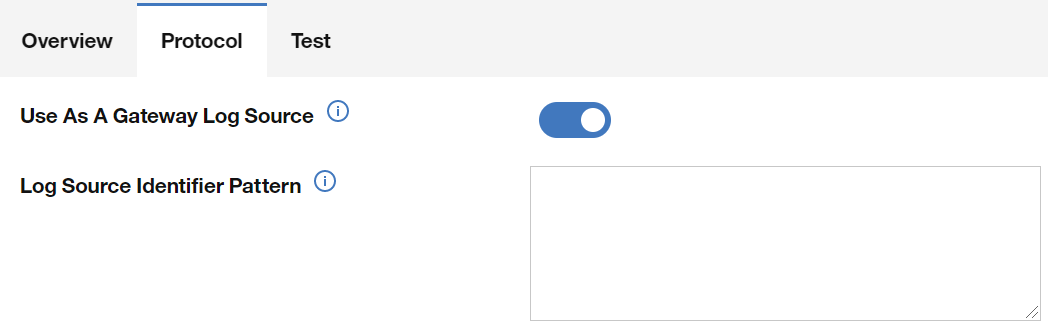
The “Log Source Identifier Pattern” provides you with the option to use a regex to find a pattern on your events and assign this pattern as the new Log Source Identifier. They are then put in the pipeline to be auto discovered by QRadar.
This file works with a key-value format where key is the new log source identifier and value the regex pattern, for example, let’s say that this is the beginning of your event.
<13>Apr 08 09:26:42 myserver01 AgentDevice=WindowsLog AgentLogFile=Security...
$1=\d{2}:\d{2}:\d{2}\s(.*?)\sAgent
This searches within events for the time format nn:nn:nn (n is a number) then follow by a space, and whatever is after that is considered group number one ($1) until a space is found again. The group number one is used as the new log source identifier.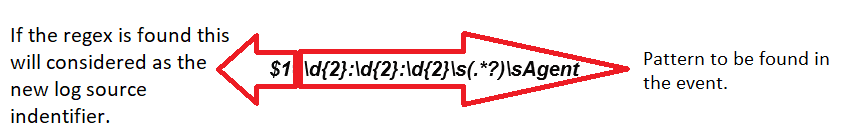
How to install a stand-alone WinCollect agent
1. Confirm the prerequisites on your server:
- Install .net framework version 3.5
- Install Microsoft Management Console (MMC) 3.0 and later.
2. Install the WinCollect agent software:
a. Download the .exe for the agent from FixCentral (7.4.0-QRADAR-AGENT-wincollect-<version>.x64.exe).
b. Start the installation wizard and pick Stand-alone mode. You can create or not during installation of the log source.
3. Install the stand-alone patch:
This provides the console with the graphical interface that allows interaction with the agent configuration.
a. Download the .exe for the console from FixCentral (7.4.0-QRADAR-wincollect-standalone-patch-installer-<version>.exe).
b. Follow the installation wizard.
4. Open the WinCollect Configuration Console:
Search for it on the Windows search bar:
5. You can now add a log source at Devices and where to send this information in the Destinations section:
Additional Information
Related Information
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
10 March 2023
UID
ibm16445471