Troubleshooting
Problem
After you create a self-signed certificate for your Engineering Lifecycle Management (ELM) environment, you might encounter a certificate error in the browser. The error does not prevent you from accessing ELM, but displays an error and forces you to proceed through messages indicating that the website is not safe.
If you are using IHS for a reverse proxy, then you might see errors in the error.log.
[Tue May 11 11:22:48.877661 2021] [ibm_ssl:error] [pid 15183:tid 140561172965120] [client 10.172.13.28:62703]
SSL0284E: The browser/client has rejected this servers certificate for an unspecified reason and has likely presented
the user a warning. Possible causes include a missing Subject Alternative Name (SAN) certificate extension or a
mismatch between the requested hostname and SAN certificate extensions. The requested TLS server_name is:
'ABC.123.com', and the SAN extensions in the server certificate are: '<not present>'.
Symptom
After you apply your self-signed certificate, when you log in to the server administration page, you might notice that your certificate is still not trusted when you view in Google Chrome, Microsoft Edge, and other Chromium browsers.
Cause
The Chromium browser requires you to include the domain name of your public URI in the Subject Alternative Names (SAN) section of the self-signed certificate. It is not enough to create a self-signed certificate that matches the public URI of your Engineering Lifecycle Management (ELM) installation.
Environment
ELM environments with Chromium browser clients at version 58 or newer, which was released April 2017. Chromium versions are the same as Google Chrome, so Google Chrome 58 and newer are affected. All modern versions of Microsoft Edge are affected, which adopted the Chromium engine in 2019.
Resolving The Problem
Create a new personal certificate in your existing keystore by using the IBM Key Management Java utility. Note: If you are using IHS, you must also update its certificate. The following describes the steps to perform in Windows operating system. Make adjustments to your environment and operating system.
1. Run the IBM Key Management utility in your IHS or application server JRE.
Example: C:\Program Files\IBM\JazzTeamServer\server\jre\bin\ikeyman
In IHS the IBM Key Management utility can be found in the <HTTPServer_Install_Dir>/bin
2. Open the default IBM keystore. Password is "ibm-team". In WebSphere Liberty it can be found in the following directory:
Example: C:\Program Files\IBM\JazzTeamServer\server\liberty\servers\clm\resources\security\ibm-team-ssl.keystore
3. Select "Personal Certificates" from the list box and display "default". This certificate is associated to the default "localhost" certificate.
4. Select "New Self-Signed" button and create a new self-signed certificate.
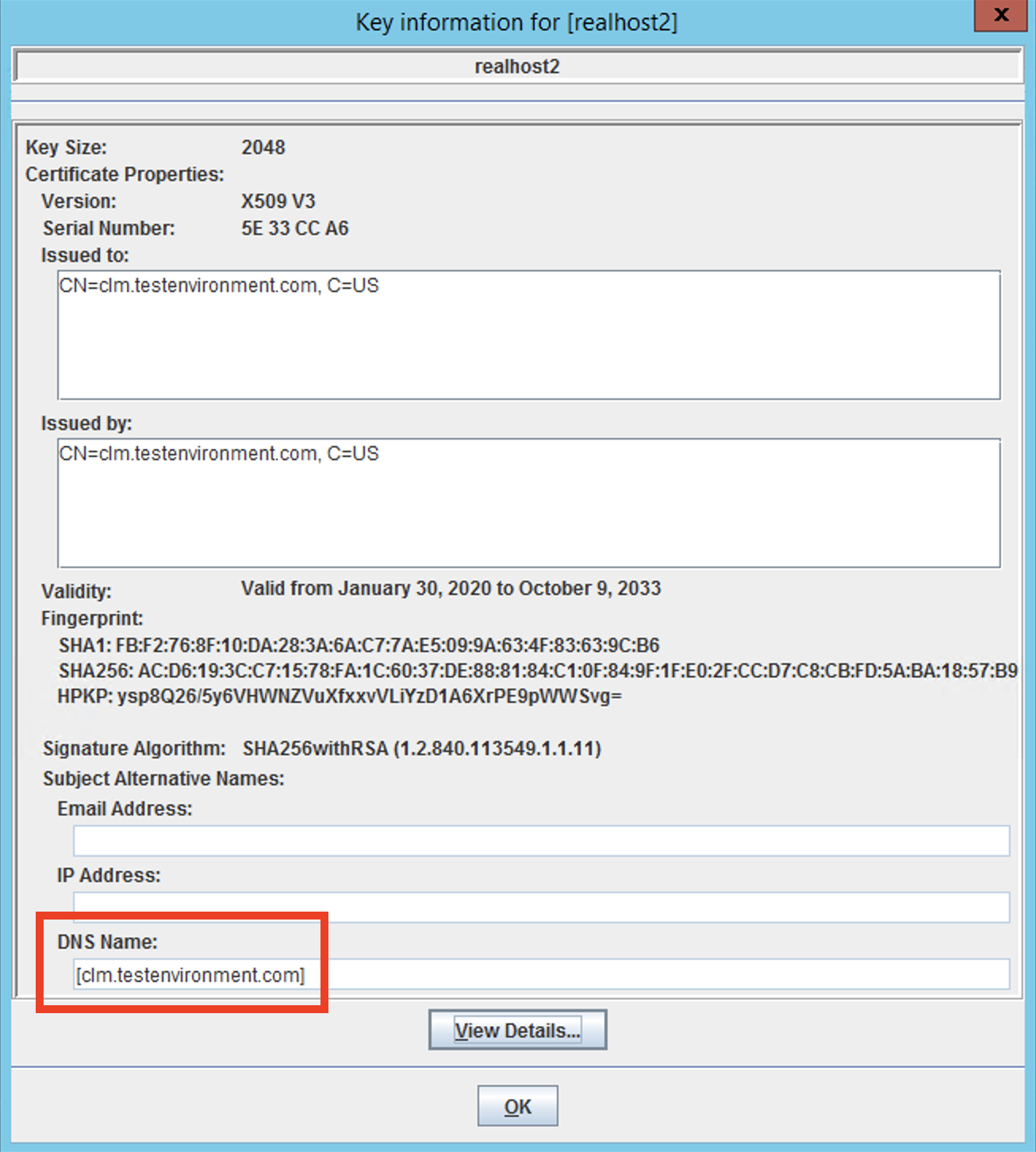
Key Label: Your public URI host name.
Version: X509 V3 (Default)
Key Size: 2048 bit.
Signature Algorithm: SHA256withRSA
Common Name: Your public URI host name. [Important] By default, the actual host name displays so change as necessary.
Validity Period: 5000 Days (this period is about 13 years)
Subject Alternative Names: Specify the domain name of your public URI under "DNS Name". [Important]
No other values need to be changed.
5. Select "Export/Import" to export the new self-signed certificate.
Key File Type: PKCS12 [Important]
Location: A path outside the ELM installation directory.
6. Select Delete to delete the "default" self-signed certificate and close IBM Key Management.
7. Open Internet Explorer on the server host machine, if it is available. Add your public URI host name to [Internet Options] > [Security] > [Trusted sites] > [Sites]. If your version of Windows comes with Microsoft Edge browser rather than Internet Explorer, you can find this setting under [Control Panel]. If you are using Google Chrome, you can find the setting under [Security] > [Trusted Sites] section.
8. Check for existing self-signed certificates under [Internet Options] > [Content] > [Certificates] > [Trusted Root Certification Authorities]. If there is one with "Issued By" as "localhost", select Remove to delete it. You can find the same setting on Google Chrome browser under [Privacy and security] > [More] > [Manage certificates] > [Trusted Root Certification Authorities] tab.
9. Select Import to Import your new self-signed certificate, which you exported previously.
10. Go to the Content tab and select "Clear SSL state" to clear the SSL cache.
11. Log out of ELM and close all browser windows. Restart your ELM application server.
12. Open your browser to a URL such as https://myhost.com:9443 to check that a padlock appears instead of warnings. Google Chrome and Microsoft Edge use the same settings as Internet Explorer, so you do not have to repeat steps.
13. Distribute the exported PKCS12 file to users so that they can import it into their browser in a similar way.
Microsoft, Windows, Windows NT, and the Windows logo are trademarks of Microsoft Corporation in the United States, other countries, or both.Java and all Java-based trademarks and logos are trademarks or registered trademarks of Oracle and/or its affiliates.Related Information
Document Location
Worldwide
[{"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSPRJQ","label":"IBM Engineering Lifecycle Management Base"},"Component":"Foundation","Platform":[{"code":"PF016","label":"Linux"},{"code":"PF033","label":"Windows"}],"Version":"6.0.x and above","Edition":"","Line of Business":{"code":"LOB59","label":"Sustainability Software"}}]
Product Synonym
Rational Collaborative Lifecycle Management Solution
Was this topic helpful?
Document Information
Modified date:
24 October 2022
UID
ibm11289289