Question & Answer
Question
In IBM MQ you can performed such tasks through the IBM Key Management GUI (iKeyman) or through the command line using runmqckm and runmqakm commands.
This document provides examples for certificate management using the command line. There is a corresponding link to the IBM MQ documentation to perform the same task using iKeyman.
Cause
- How to check a certificate expiration?
- How to list the content of a MQ keystore?
- How to view the content of a certificate?
- How to (process) create a certificate signing request (CSR) and to receive a CA signed personal certificate?
- How to renew an existing certificate before it expires?
- How to rename a certificate?
- How to export and import a personal certificate?
- How to check/verify that you have a personal certificate for your queue manager or client?
- How to tell if the certificate has OCSP/CRL validation?
- How to combine public certifcate and private key into PKCS12 file
Answer
- runmqakm -cert -list -db <keyfile.kdb> -pw <password> -expiry xx
runmqakm -cert -list -db key.kdb -pw password -expiry 90
- runmqakm -cert -list -db <keyfile.kdb> -pw <password>
- runmqakm -cert -details -label <cert_label> -db <keyfile.kdb> -pw <password>
How to (process) create a certificate signing request (CSR) and to receive a CA signed personal certificate?
- Create the queue manager keystore if none exists.
- Create the CSR, and and send it to the CA.
- Receive the CA signed personal certificate requested sent by the CA into the keystore
- Add CA Singer Certificates (Intermediates and Root) into the keystore. Note: This a mandatory step for certificate validation. For more details see the following technote:
How certificate chains work
- runmqakm -keydb -create -db <keyfile.kdb> -type cms -pw <password> -stash
b) Create a Certificate Signing request (CSR) for the queue manager
- runmqakm -certreq -create -db <keyfile.kdb> -pw <password> -label <cert_Label> -dn <distinguished_name> -size <key_size> -file <filename> -sig_alg <algorithm>
c) Verify that the certificate requests was created by listing it:
- runmqakm -certreq -list -db <keyfile.kdb> -stashed
d) Send the CSR to your CA to be signed.
- runmqakm -cert -add -db <keyfile.kdb> -stashed -label <cert_label> -file <ca_filename>
Be careful NOT to add the actual signed certificate file to the keystore, as runmqakm -cert -add
g) Receive the CA signed certificate with the following command:
- runmqakm -cert -receive -file <filename> -db <keyfile.kdb> -stashed
h) List the content of the keystore to make sure the certificates, personal and signers, where added to the keystore:
- runmqakm -cert -list -db <filename> -stashed
If you want to renew an existing certificate that is about to expire, you can do the following:
- runmqakm -certreq -recreate -db <keyfile.kdb> -pw <password> -label <label> -target <filename>
b) Send the certificate renewal request to the CA
- runmqakm -cert -add -db <keyfile.kdb> -stashed -label <cert_label> -file <ca_filename>
- runmqakm -cert -receive -file <filename> -db <keyfile.kdb> -pw <password>
- runmqsc QMGR_NAME
- REFRESH SECURITY TYPE(SSL)
https://www.ibm.com/support/knowledgecenter/SSFKSJ_9.2.0/com.ibm.mq.sec.doc/q012790_.htm
KC: Renewing an existing personal certificate on UNIX, Linux, and Windows
https://www.ibm.com/mysupport/s/question/0D50z00005phsz1CAA/how-to-renew-websphere-mq-ssl-certificates?language=en_US
How to renew WebSphere MQ SSL Certificates
One way to renew the certificate would be using the following command:
- runmqakm -cert -rename -db <keyfile.kdb> -pw <password> -label <label> -new_label <newLabel>
Also see the following article:
In MQ, how do you rename the certificate label if the label name is incorrect?
To Export a personal certificate use the following command:
- runmqakm -cert -export -db <keyfile.kdb> -pw <password> -label <label> -type <cms> -target <filename> -target_pw <password> -target_type <kdb>
target_pw - is the password for file where the certificate is saved. This is used when importing the certificate.
target_type - is the type of certificate
To import a personal certificate, use the following command:
- runmqakm -cert -import -file <filename> -pw <password> -type <kdb> -target <filename> -target_pw <password> -target_type <cms> -label <labelName>
target - is the name of the keystore file where the certificate will be import to.
target_pw - is the password of the keystore
- runmqakm -cert -list -db <filename> -stashed
- runmqakm -cert -list -db <keyfile.kdb> -pw <password>
runmqakm -cert -list -db key.kdb -stashed
Certificates found
* default, - personal, ! trusted, # secret key
! ibmwebspheremqperez
- ibmwebspheremqssl1
b) Using the runmqckm command:
- runmqckm -cert- list personal -db <file.kdb> -pw <password>
C) From the Key Management GUI (iKeyman)
- Open keystore file -> From the drop down menu select "Personal Certificates"
Most CA certificates have this extension.
- runmqakm -cert -details -label <cert_label> -db <filename> -stashed
https://www.ibm.com/support/knowledgecenter/SSFKSJ_9.2.0/com.ibm.mq.sec.doc/q135040_.htm
How to combine public certificate and private key into PKCS12 file
Sometimes you may have your public certificate and private key sent in one combined file or in two separate files. To import them into MQ they will need to be in one pkcs12 file. If your certificate and key come in separate files you can skip the Split Certificate/Key in Text Editor step.
Split Certificate/Key in Text Editor:
If your certificate and key are in separate files you can split them in a text editor into two files.
The certificate will have delimiters at the start and end of the certificate. Include these in your new certificate file.
Certificate Delimiter Example: -----BEGIN CERTIFICATE----- <CERTIFICATE> -----END CERTIFICATE-----
Name the cert exampleCert.crt for clarity.
The private key will also have delimiters surrounding the key. Include these in the new private key file.
Private Key Delimiter Example: -----BEGIN PRIVATE KEY-----<PRIVATE KEY> -----END PRIVATE KEY-----
Name the cert exampleCert.key for clarity.
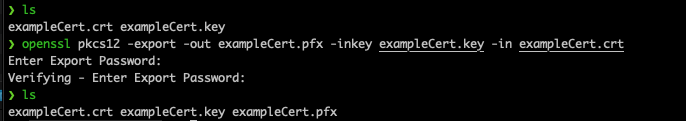
OpenSSL On Linux/AIX:
Using the "OpenSSL pkcs12 -export" command you can combine the certificate and the private key. The usage is:
openssl pkcs12 -export -out [OutputCertificate] -inkey [InputPrivateKey]-in [InputCertificate]
certutil on Windows:
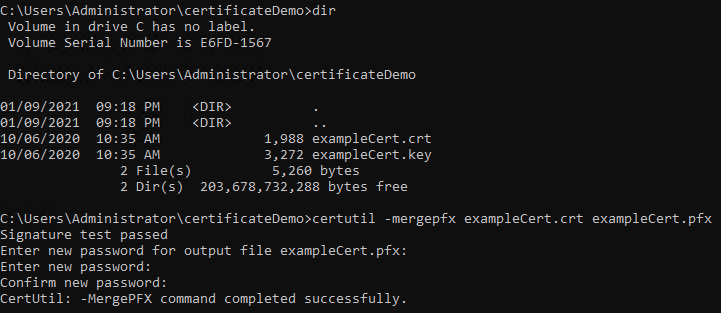
certutil is a built in utility in Windows. It requires your certificate and private key have the same file names with different extensions. The command usage is:
certutil -mergepfx [InputCertificate] [OutputCertificate]
The private key's file name is inferred by the command. In our example pictured because our certificate is exampleCert.crt certutil will look for an exampleCert.key to merge.
tags: "MQ SSL"; "MQ TLS"; MQSSL; MQTLS
Was this topic helpful?
Document Information
Modified date:
26 October 2023
UID
ibm16382940