Question & Answer
Question
When enables LOG FULL DETAILS action by default settings, InfoSphere Guardium may collect too many activities from the target database servers. Some of the users may want to ignore capturing activities of DB2 administration processes such as DB2HMON or DB2DASSTM.EXE. How can we reduce or omit the unnecessary DB2 process activities from capturing by S-TAP?
Cause
When you install a policy rule to enable LOG FULL DETAILS action to any application, the S-TAP might collect too many activities, and it may consume unnecessary disk resource.
Answer
You can ignore capturing the activity of some specific processes by defining INGNORE S-TAP SESSION policy. Here is the overview scenario.
Overview:
- 1. Create a group for trusted applications
Create a group named My Trusted Applications, and add DB2HMON and DB2DASSTM.EXE to this group.
2. Create a policy for the group
Create a policy named Ingore My Trusted Application, and apply My Trusted Application group to Ingnore S-TAP Session action.
3. Install the policy
Install the Ignore My Trusted Application policy.
[NOTE] The group name My Trusted Application and the policy name Ignore My Trusted Application can be changed as you like.
- The detail instruction is here:
- 1. Create a group for trusted applications
- Create a group named My Trusted Applications, and add DB2HMON and DB2DASSTM.EXE to this group.
1.1. Login to the Guardium web console by admin role.
1.2 Click Monitor/Audit > Build Reports tabs, and click on Group Builder icon.



2. Create a policy for the group
- 2.1 Click Monitor/Audit > Build Audit Policies tabs, and click New... button in Policy Finder.


2.3 Click Edit Rules... to open a Policy Rules pane.
2.4 From the Policy Rules pane, click Add Access Rule... button.

2.5 From the Access Rule Definition pane, type Rule for Ignoring My Trusted Application at Description field, select (public) My Trusted Application at the and/or Group pull down list at Src App. field, and then click Add Action button.

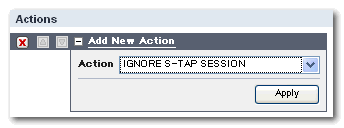
2.7 Click Save button.

Now, a new policy rule is defined. See if the action is correctly defined.

3. Install the policy
- Install the Ingore My Trusted Application policy.
3.1 Click Protect > Security Policies tabs, and click on Install Policy icon.

3.2 From the Policy Installer pane, select Ignore Trusted Application policy, which was defined in the previous step, and then select Install from the pull down list.
[NOTE] If you have any policy installed, all the installed policies are listed sequentially. Select the appropriate position which this policy should be applied. The following figure shows an example to choose Ignore Trusted Application policy before Policy_1 and v8.

Now, the policy has been installed.
Verification
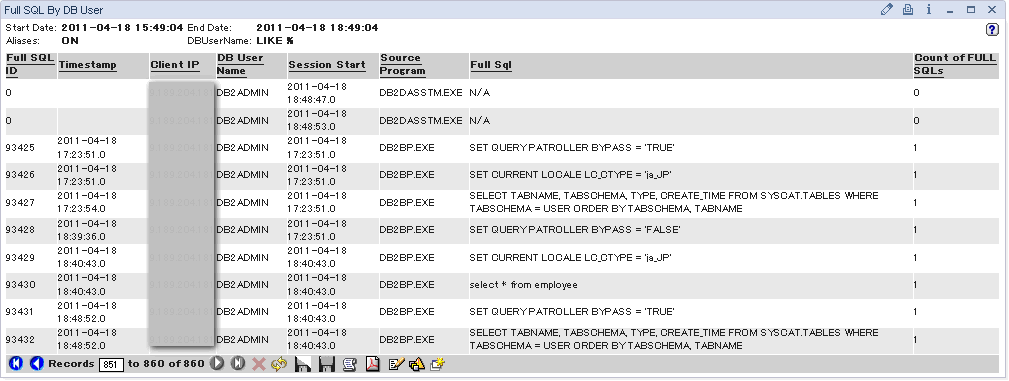
The following report was captured after the Ignore Trusted Application rule has been installed and the DB2DASSTM.EXE process has been restarted at 18:45. You can see that DB2DASSTM.EXE is no longer reported in Full SQL By DB User report even though the process is running.
| C:\>tasklist | findstr /I DB2DASSTM.EXE db2dasstm.exe 452 Console 0 35,400 K C:\> |
Was this topic helpful?
Document Information
Modified date:
16 June 2018
UID
swg21497163