How To
Summary
How can I only configure the WebSphere Application Server SSL protocol to use TLSv1.2 or TLSv1.3?
Objective
The following steps demonstrate for ND environment where you have Deployment Manager, Node Agent, and Application Server instances, and using default WebSphere Application Server SSL configuration CellDefaultSSLsettings and NodeDefaultSSLsettings.
WebSphere Application Server Network Deployment (hereafter referred to as Network Deployment) cell has a cell-scoped (meaning visible to all processes in the cell) SSL configuration called CellDefaultSSLSettings. This configuration contains node-scoped (visible to all endpoints on that specific Node) SSL configurations called NodeDefaultSSLSettings for every Node in the cell. Also, NodeDefaultSSLSettings will apply to each application server that runs within that Node.
These SSLconfigurations (CellDefaultSSLSettings & NodeDefaultSSLSettings) contain many resources such as keystore, truststore, SSL handshake protocol, cipher suite group, and Client authentication.
The following picture shows the SSL configuration layout for dmgr (CellDefaultSSLSettings) and one node (NodeDefaultSSLSettings). For the stand-alone WebSphere Application Server, you will see only NodeDefaultSSLSettings.

Steps
High Level Steps
- Backup the WebSphere Application Server configuration
- Configure TLSv1.2 or TLSv1.3 for WebSphere Application Server SSL configuration (CellDefaultSSLsetting, NodeDefaultSSLsetting, and XDDefaultSSLsetting).
- Configure TLSv1.2 or TLSv1.3 for the DMGR & Node ssl.client.props.
- How to verify WebSphere Application Server using TLSv1.2 or TLSv1.3 protocol.
- Frequently asked questions (FAQ) or Questions and Answers (Q&A).
Backup the WebSphere Application Server configuration
Please make sure to backup the WebSphere Application Server configuration before making any changes in the WebSphere Application Server SSL configuration.
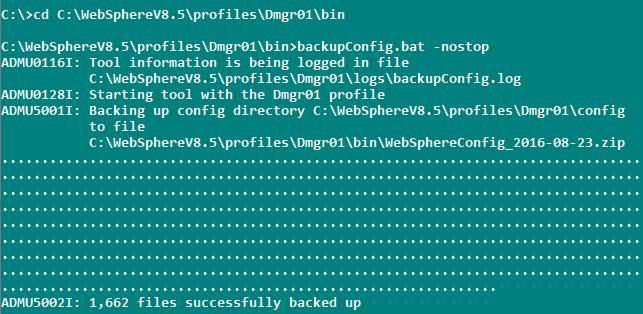
WebSphere Application Server has backupConfig command, which will backup the entire config directory
Tells the backupConfig command not to stop the servers before backing up the configuration
Example command
cd to dmgr profile path (WAS_INSTALL_HOME>/profiles/<DMGRPROFILE_NAME>/bin)
backupConfig.bat -nostop
For more details on backup command options, please check the following
https://www.ibm.com/docs/en/was-nd/8.5.5?topic=tools-backupconfig-command
How do I run the backupConfig and restoreConfig scripts in the WebSphere Application Server?
https://www.youtube.com/watch?v=EXAfSx1gVwc
Configure TLSv1.2 or TLSv1.3 for WebSphere Application Server SSL configuration (CellDefaultSSLsetting, NodeDefaultSSLsetting, and XDDefaultSSLsetting)
Modify all WebSphere SSL configurations by running the following manual steps from the WebSphere Application Server console:
1. Log in to the WebSphere Application Server Integrated Solutions Console.
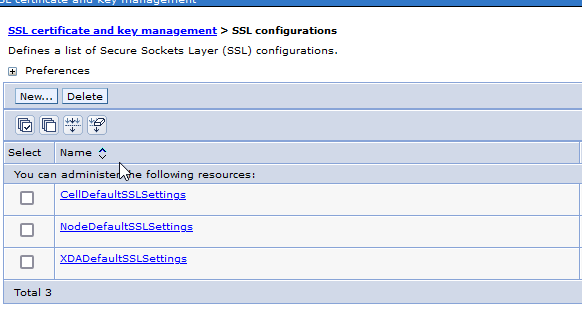
2. Click Security > SSL certificate and key management; under Related Items, click SSL configurations. (such as CellDefaultSSLsetting, NodedefaultSSLsetting, and any other SSLConfig)
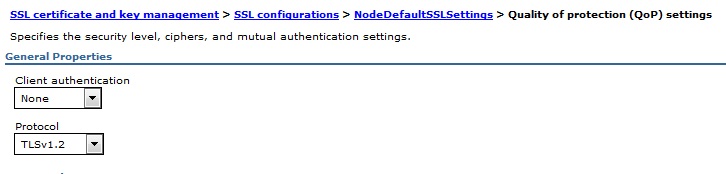
The following pictures are related to the TLSv1.2 configuration.
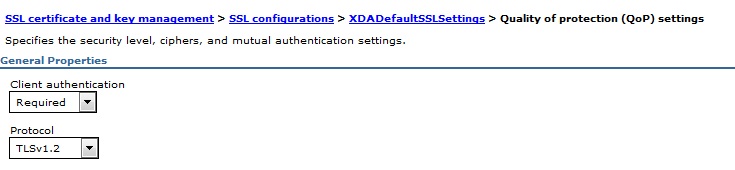
The following pictures are related to the TLSv1.3 configuration.

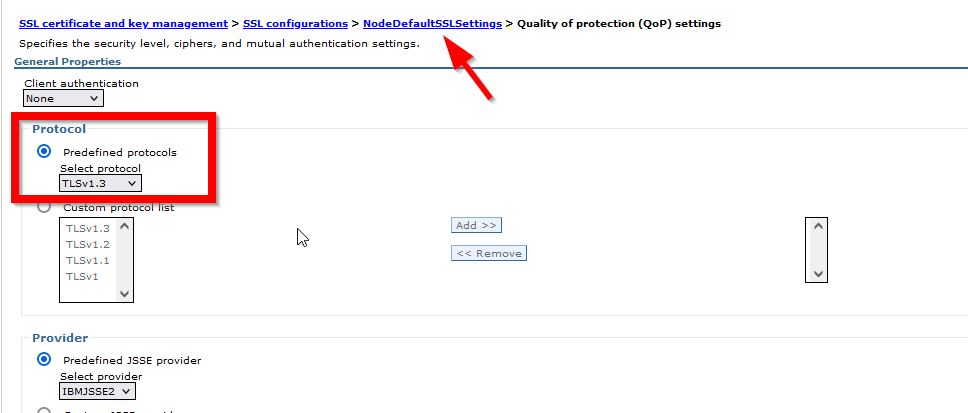
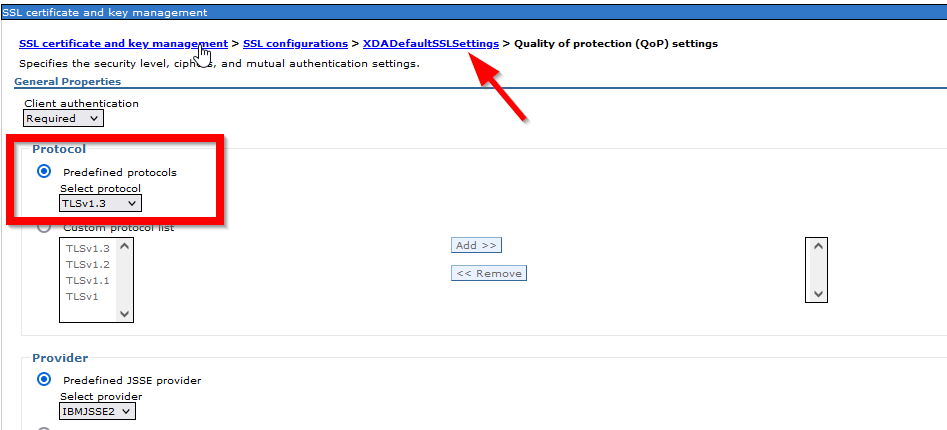
Note: For each node, it has its own NodeDefaultSSLsetting, and the above setting will APPLY BOTH inbound and outbound SSL Communication
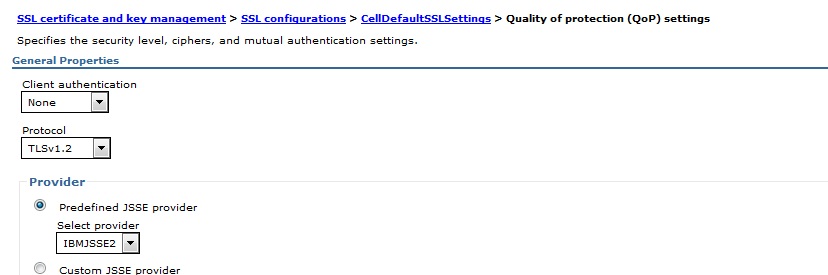
3. Select each SSL Configuration described above, then click Quality of protection (QoP) settings under Additional Properties.
4. On the Quality of protection (QoP) settings panel, select TLSv1.2 or TLSv1.3 (depend on your security requirement) from the pull-down list in the box named Protocol and change the protocol to TLSV1.2
5. Click Apply and Save.
Configure TLSv1.2 or TLSv1.3 for the DMGR & Node ssl.client.props
Update the ssl.client.props configuration file for the dmgr and node
Note: Backup this configuration file before making any changes in the ssl.client.props.
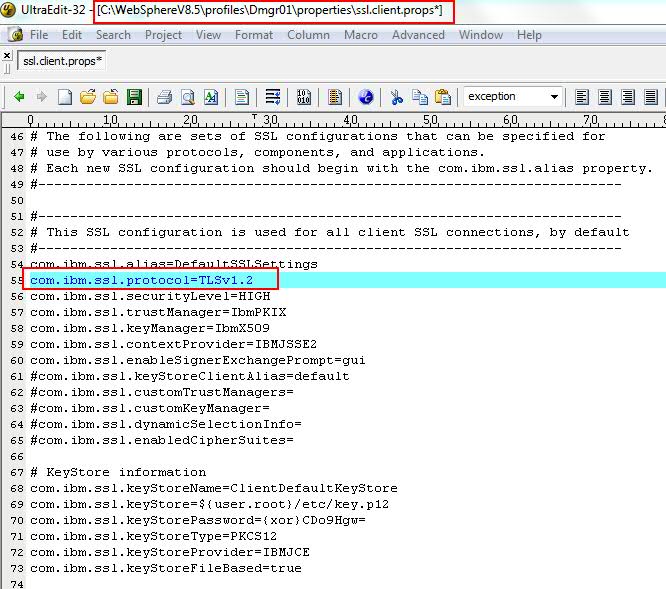
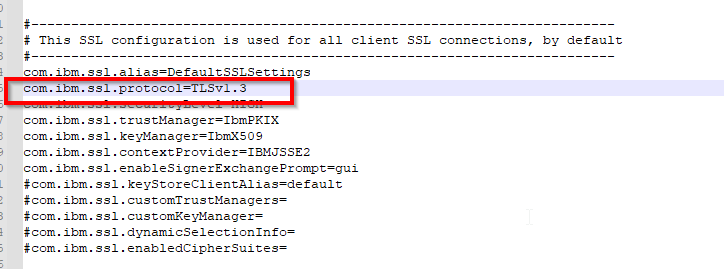
The SSL protocol is set with the com.ibm.ssl.protocol property in the ssl.client.props file.
<WAS_INSTALL_HOME>/profiles/<PROFILE_NAME>/properties and edit the ssl.client.props file and set the com.ibm.ssl.protocol value to TLSv1.2
For example, modify com.ibm.ssl.protocol=TLSv1.2 This must be done for each ssl.client.props file under the following directories:
For Node example WAS_install\profiles\AppSrv01\properties
For DMGR example WAS_install\profiles\Dmgr01\properties
The following picture is related to the TLSv1.2 configuration.
The following picture is related to the TLSv1.3 configuration.
Note: If neither of these is unable to stop properly due to permission issues or some other issue, you will have to manually kill each of these by logging on to the machines and killing the appropriate deployment manager and nodeagent, Application servers processes
1. Stop the Deployment Manager
cd <WAS_INSTALL_HOME>/profiles/<DMGRPROFILE_NAME>/bin and Use the stopManager command
2. Stop the Application Server
cd <WAS_INSTALL_HOME>/profiles/<NODEPROFILE_NAME>/bin and Use the stopServer servername
3. Stop the Node Agent
cd <WAS_INSTALL_HOME>/profiles/<NODEPROFILE_NAME>/bin and Use the stopNode command
4. Start the dmgr
cd <WAS_INSTALL_HOME>/profiles/<DMGRPROFILE_NAME>/bin and Use the startManager command
5. Sync the node with dmgr using syncNode command before going to start the node agents
cd <WAS_INSTALL_HOME>/profiles/<NODEPROFILE_NAME>/bin and use the syncNode.bat <deploymgr host> <deploymgr port>
syncNode.sh <DMgr_hostName> <SOAP_PORT_of_DMGR> -username <username> -password <password>
dmgr_host is the host name of the Deployment Manager
dmgr_port is the SOAP port of the deployment manager (the default is 8879). Please make sure your dmgr soap port.
uid and pwd are the DM administrator user name and password
Please see this video How can I manually synchronize a node with the Deployment Manager in WebSphere Application Server?
https://www.youtube.com/watch?v=VZNJMgdw-oA
6. Start the node agent
cd <WAS_INSTALL_HOME>/profiles/<NODEPROFILE_NAME>/bin and Use the startNode command
Logon to Dmgr administrative console and check the Node/Server availability and then synchronize nodes in the administrative console
7. You can start the application server from the console.
How to verify WebSphere Application Server using TLSv1.2 protocol
You can perform testing using a browser or external tool such as OpenSSL.
Test with Browser
Configure the browsers to support only TLS 1.2 or TLSv1.3 and access the admin console or application.
1. To configure Internet Explorer version 8 and later, complete these steps:
a. In Internet Explorer, click Tools > Internet Options.
b. In the Internet Options dialog box, click the Advanced tab.
c. Scroll to the Security section, select the Use TLS 1.2 or TLSv1.3 checkbox, and click OK.
2. To configure Firefox version 24 and later, complete these steps:
a. Open a Firefox browser and enter about: config in the address bar.
b. When prompted, click I'll be careful, I promise! and accept the warning.
c. Search for security.tls.version.max.
d. Double-click security.tls.version.max and change the value to 3 to configure the browser to support TLS1.2.
Tip: Value of 1 supports TLS1.0. Value of 2 supports TLS1.0 and TLS1.1. Value of 3 supports TLS1.0, TLS1.1, and TLS1.2.
Test with External Tools such as OpenSSL
You can use OpenSSL s_client to connect to WebSphere Application Server using an SSL port like a console SSL port or Application server SSL port
openssl s_client -connect webspherehostname:consolesslport -tls1_2
example
openssl s_client -connect webspherehostname:9443 -tls1_2
openssl s_client -connect webspherehostname:9443 -tls1_3
If it is connected to the WebSphere Application Server system, then it will display the certificate chain in the command prompt and the handshake details. Based on this, you will know that the WebSphere Application Server system is configured to support TLVs1.2.
Note: The above steps apply to other protocols, such as TLSV1.2 to SSL_TLSV2
Frequently asked questions (FAQ) or Questions and Answers (Q&A)
Question: Is TLSv1.3 supported in WebSphere Application Server 8.5.5? What's the minimum fix pack?
Answer: TLSv1.3 support from JDK1.8 Service refresh 7 fix pack 15, and IBM recommends installing the latest Websphere Application Server fixpack and JDK level.
https://www.ibm.com/support/pages/recommended-updates-websphere-application-server
Question: Is TLSv1.2 supported in WebSphere Liberty Profile 8.5.5? What's the minimum fix pack?
Answer: Liberty can be configured with any JDK. So it depends on what JDK version is configured with the Liberty profile. If you are using IBM JDK v1.6 jdk SR11 then it is supported. if you are using the below version of this JDK then it is not supported
TLSv1.2 is introduced on JDK 1.6 Sr10. which mean it starts from WAS7.0.0.23 ( JDK1.6 SR10 FP1)) onwards
see the following details
JSSE enhancements The following enhancements were made in the JSSE in IBM SDK for Java™ V6 service refresh 10:
The IBMJSSE2 provider now supports Transport Layer Security (TLS) 1.1 as described in RFC 4346. The most important update is protection against cipher block chaining (CBC) attacks.
**The IBMJSSE2 provider now supports TLS 1.2 as described in RFC 5246. Among other things, this RFC specifies different internal hashing algorithms, adds new cipher suites, and contains improved flexibility, particularly for negotiation of cryptographic algorithms**.
Question: Which cipher suites support the TLSv1.2 protocol?
Answer: Cipher suites with SHA384 and SHA256 are available only for TLS 1.2 or later more details, Please see the following link
Cipher suites
https://www.ibm.com/support/knowledgecenter/SSYKE2_8.0.0/com.ibm.java.security.component.80.doc/security-component/jsse2Docs/ciphersuites.html
Question: Do I have to enable FIPS strict mode to use TLSv1.2?
Answer: No. You can configure WebSphere Application Server to use TLSv1.2 without FIPS.
Question: WebSphere Application Server is acting SSL client. Does the Remote SSL server have to use TLSV1.2 as well to work?
Answer: Yes, both the Client side and Server side must use TLSv1.2 for SSL communication.
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
26 December 2022
UID
ibm11077951