Troubleshooting
Problem
Android devices that do not have user configured Google accounts are still becoming locked with Factory Reset Protection (FRP).
Symptom
Upon factory reset, an Android device, which had no previous user Google accounts configured, asks for an account credentials to be entered in order for activation to continue.
Cause
In almost every case this is the result of an incomplete security feature being implemented in the device policy.
In the Android Enterprise Settings, under Security there is a feature called Enable Factory Reset Protection. If this feature is enabled, it will cause devices to become locked to any account that is configured, including accounts MaaS360 creates.
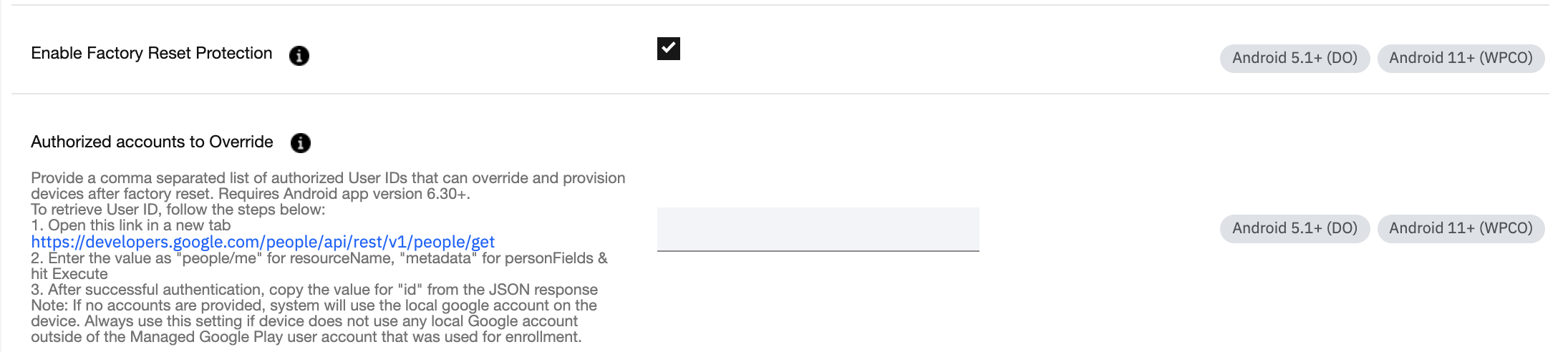
In the Android Enterprise Settings, under Security there is a feature called Enable Factory Reset Protection. If this feature is enabled, it will cause devices to become locked to any account that is configured, including accounts MaaS360 creates.

The root cause of the issue is the Authorized accounts to override field is left empty. As the Google account created by MaaS360 has no traditional user credentials that can be entered to override FRP, this leaves the device in a perpetually locked state, requiring firmware flashes or OEM assistance to unlock.
With the 10.83 release in September 2021 (date TBD), MaaS360 will update policy publishing guidelines so that if this field is left blank in the policy, the policy will not publish successfully. The admins will either need to generate accounts to override, or disable the feature in policy.
With the 10.83 release in September 2021 (date TBD), MaaS360 will update policy publishing guidelines so that if this field is left blank in the policy, the policy will not publish successfully. The admins will either need to generate accounts to override, or disable the feature in policy.
Resolving The Problem
Option 1
Disable the security feature in the policy. Setting the Enable Factory Reset Protection feature to "off" does not prevent users from leveraging the service, it simply prevents it from being on by default, and therefore prevents the device from potentially being locked to an account with no credentials. Only manually input credentials will be able to configure FRP.
Disable the security feature in the policy. Setting the Enable Factory Reset Protection feature to "off" does not prevent users from leveraging the service, it simply prevents it from being on by default, and therefore prevents the device from potentially being locked to an account with no credentials. Only manually input credentials will be able to configure FRP.
Option 2
Leave the feature enabled and create a recovery account by following the links in the feature description. This will enable an account with a usable password to be placed on the devices via policy. Just be sure to keep the password for the override account in a secure password manager, especially if you don't anticipate using it often.
Portal Wipe Action
Regardless of which course of action above is utilized, admins can, and should, make it a habit to wipe devices from the portal with a wipe action, rather than using the settings on the device. This will present admins with the ability to override FRP as part of the wipe, taking any potential locks off the device as it resets.
Portal Wipe Action
Regardless of which course of action above is utilized, admins can, and should, make it a habit to wipe devices from the portal with a wipe action, rather than using the settings on the device. This will present admins with the ability to override FRP as part of the wipe, taking any potential locks off the device as it resets.
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB24","label":"Security Software"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSYSXX","label":"IBM MaaS360"},"ARM Category":[{"code":"a8m0z000000070yAAA","label":"POLICY"}],"ARM Case Number":"","Platform":[{"code":"PF003","label":"Android"}],"Version":"All Versions"}]
Was this topic helpful?
Document Information
Modified date:
16 August 2021
UID
ibm16481887