Release Notes
Abstract
With the 10.83 release, MaaS360 brings in the enhancements in the User Risk Management that are currently offered as a BETA version for customers to try out in combination with the Endpoint Security. Contact IBM MaaS360 Customer Support team to avail Endpoint Security and try out these additional capabilities with user risk management.
Content
- New Risk Rules in the Risk Rule Configurator
- Detailed view of the risk incidents in the Security Dashboard
- Options for administrators to update threshold values in the risk rules
- Reset to default in the risk rule configurator
New Risk Rules in the Risk Rule Configurator
The User Risk Management offers the following four new risk rules.
- Malicious email received
- Malicious SMS received
- Windows privileges violations
- Risky app permissions
Note:
- In case the device is not refreshed or not connected to the internet and if the email with a malicious URL is received on the device during this time, then, such an incident is not reported to MaaS360. In this case, the incident is not reported in the security dashboard and no risk rule action is taken although the risk rule is enabled.
- For this risk rule to function, the Endpoint Security Service must be enabled on the Services page and the Endpoint security policy setting Mark emails with malicious URLs must be enabled in the security policy under the Phishing settings.
Malicious SMS received: This rule checks if any SMS with malicious URLs has been reported on the device. The higher the number of malicious SMS's received on the device, the higher the risk score and severity. Based on the organization's need, an administrator can configure the threshold values for the count of malicious SMS received rule descriptions. Note: You cannot set overlapping threshold values under rule descriptions for this rule name. By default, the defined severity is based on <=2 malicious SMS received, >=3 AND <= 5 malicious SMS received, or more than five malicious SMS received on the device. Whenever a malicious SMS is received on the device, the incident is reported to MaaS360, and based on this risk rule configuration, a risk incident is created and a risk score is added. This risk rule is applicable on Android devices only.
Note:
- In case the device is not refreshed or not connected to the internet and if SMS with a malicious URL is received on the device during this time, then, such incident is not reported to MaaS360. In this case, the incident is not reported in the security dashboard and no risk rule action is taken although the risk rule is enabled.
- For this risk rule to function, the Endpoint Security Service must be enabled on the Services page and the Endpoint security policy setting Flag SMS with malicious URLs must be enabled in the security policy under the Phishing settings.
Windows privileges violations: This rule checks if any violations have occurred wherein administrator privileges are found on user accounts of the device. When this rule name is enabled, whenever any defined administrator privileges are encountered on a standard user's account, then the incident is reported to MaaS360, and based on this risk rule configuration, a risk incident is created and a risk score is added. You can configure the windows privileges under the Endpoint security policy setting > Privileges. Configure permissions to be detected as risky on user accounts and remediation actions to be taken when such excess privileges are encountered on user accounts.
This risk rule is applicable on Windows devices only. One risk incident is created against any windows privilege violations that are configured for one endpoint security policy. If one or more endpoint security policies are configured and if windows privilege violations are detected, then one risk incident is created against each of those security policies where the violations are detected.
Note: For this risk rule to function, the Endpoint Security Service must be enabled on the Services page.
The rule set is categorized under device-based risk rules as the risk score that is associated with these risk incidents decreases immediately (becomes zero) when all the windows privileges violations that are associated with the risk incident are remediated on the user account and removed from the Security Dashboard.
Risky app permissions: This rule checks if any applications on Android devices have Device Administrator permissions. When this rule name is enabled, the applications on the device are checked whether administrator permission is present. if this permission is encountered on the applications on the device, then the incident is reported to MaaS360, and based on this risk rule configuration, a risk incident is created and a risk score is added. You can configure the Device Administrator as app permission that must be considered as risky under the Endpoint security policy setting > App permissions. Configure the permissions to be managed and action to be taken on the device when the permission is encountered on the device. Note: In this release, under 'permissions to be managed' in the App permissions, only Device Administrator app permission is supported under the 'risky app permission' rule name for detecting the risk.
This risk rule is applicable on Android devices only. One risk incident is created against device administrator application permission that is configured for one endpoint security policy. If one or more endpoint security policies are configured and if device administrator application permissions violation is detected, then one risk incident is created against each of those security policies where the violations are detected.
Note: For this risk rule to function, the Endpoint Security Service must be enabled on the Services page.
The rule set is categorized under device-based risk rules as the risk score that is associated with these risk incidents decreases immediately (becomes zero) when all the risky app permissions that are associated with the risk incident are remediated on the device and removed from the Security Dashboard.
Detailed view of the risk incidents in the Security Dashboard
The summary view of risky devices for a user shows details such as device name, risk contribution, managed status, incidents, filter by, bell icon, and more details. With the click of More, a detailed view of all incidents is displayed for a user device. You can also view the total number of risk incidents that are associated with a user device. Each incident shows incident details, severity, the first time when the incident was observed, and the status of the incident as open.
In 10.83, an additional option View details are made available for each risk incident. With the click of View details, useful details related to the risk incident are available that helps the administrator to analyze and fix the security issues that are causing the risk incident. You can also click the incident that slides out more details that are specific to the risk incident. Currently, these additional details are available for risk incidents that are created for the following risk rules: Malicious email received, Malicious SMS received, Windows privileges violations, and risky app permissions.
Viewing an example of the detailed view of risk incidents for a user
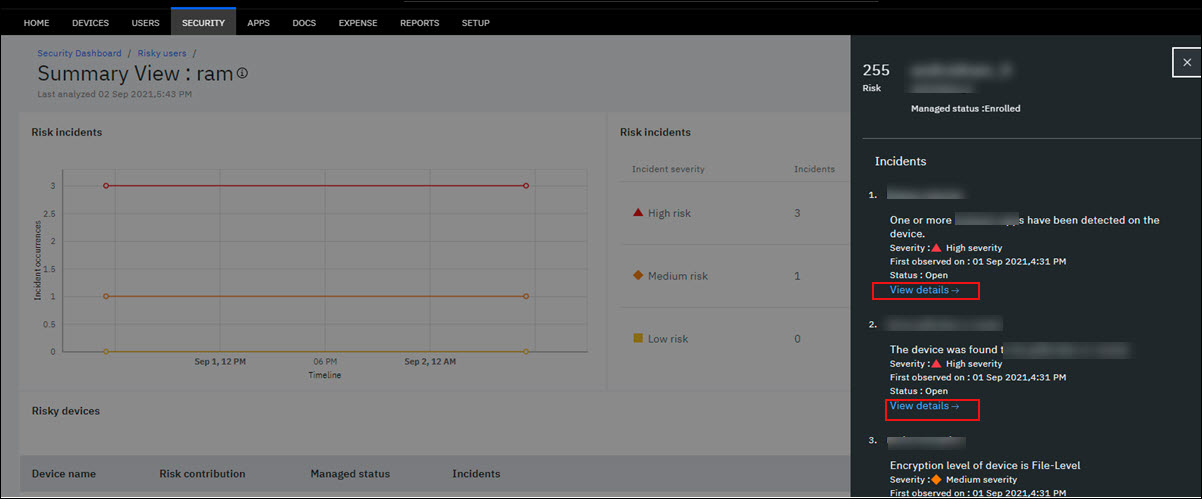
Examples:
For windows privileges violations, additional details on which administrator privileges are detected on which user accounts are shown along with user details.
For risky app permissions violations, additional details such as app ID, app name, app version, date when the incident occurred are shown for every excess app permission that is detected on the device.
Viewing an example of the detailed view of risk incidents for excess app permissions detected on a device
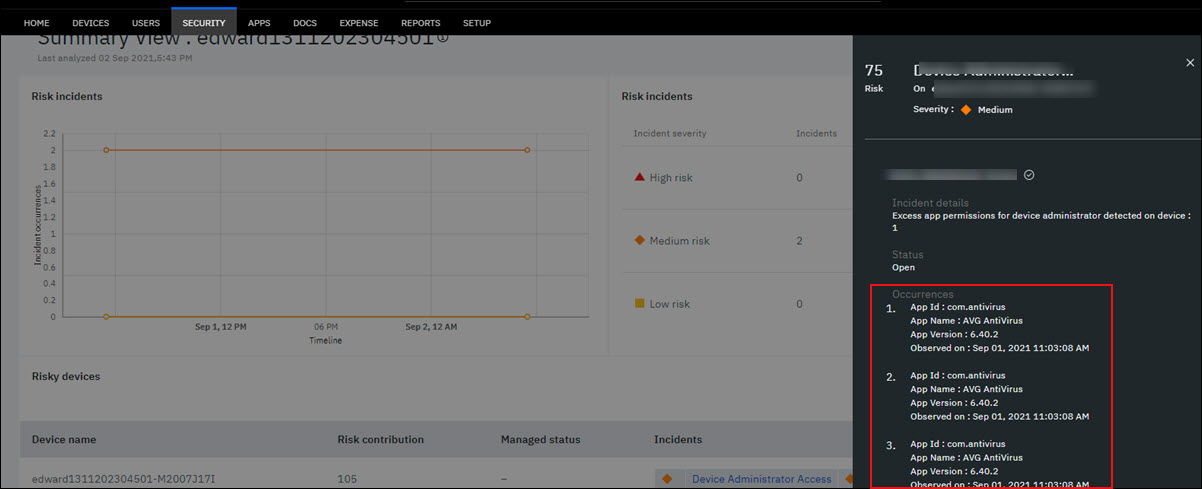
In the risk rule set, the rule names have predefined conditions that include default threshold values (numeric or text). Based on the organization's need, an administrator can configure the threshold values of the risk rule descriptions for the rule names. Currently, an administrator can edit only numeric threshold values to define the rule descriptions.
Example: Administrator can set the following numeric threshold values for malicious email received rule name.
| Malicious email received | Severity | Enabled |
| No. of Malicious email received <= 5 | Low | Yes |
| No. of Malicious email received >=6 AND No. of Malicious email received <= 10 | Medium | Yes |
| No. of Malicious email received >15 | High | Yes |
Note:
- You cannot set an overlapping numeric threshold value under rule descriptions. Example: No. of Malicious email received cannot be <=5 in the first rule description and >=5 as well in the second rule description.
- A lower limit cannot exceed the upper limit threshold value. Example: You cannot have a rule that is defined as No. of Malicious email received >=6 AND No. of Malicious email received <=5.
Viewing an example of editing threshold values for malicious email received risk rule

The following list of rule names is available for administrators to define the numeric threshold values.
- Critical security patch missing
- Blocked URL access (Secure Browser)
- Device inactivity
- Malicious email received
- Malicious SMS received
- Out of compliance events
Reset to default settings in the Risk Rule Configurator
The Risk Rule Configurator includes a rule set each of which that has a predefined value in the rule descriptions and severity. By default, all rule names in the risk rule configurator are enabled. Administrators have the flexibility to disable or enable any of the rule sets and also enable or disable a particular rule description under a rule name. You can also define the severity as low, medium, and high for individual rule descriptions under a rule name.
Based on organization needs, the administrator can also edit the numeric threshold values under rule descriptions. To change threshold values for risk rules, see the topic, Capability for administrators to change threshold values of risk rules. Using the Rest to the default option, an administrator can revert all threshold values in the rule descriptions to default. The severities of the rule descriptions also revert to default and all rule descriptions are enabled. The default state refers to the values that appeared during the first time you logged in to the risk rule configurator.
In the Risk Rule Configurator, click Reset to default, and click Continue to confirm risk rule values to be reset to default.
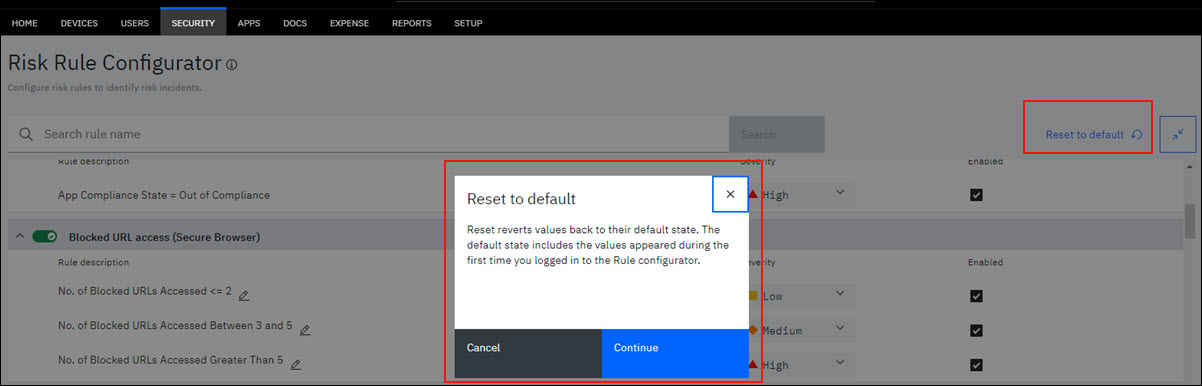
Was this topic helpful?
Document Information
Modified date:
09 September 2021
UID
ibm16487715