Troubleshooting
Problem
A DataPower SQL injection filter blocks requests that are considered likely to alter SQL queries with the goal of obtaining sensitive data. A filter action protects against threats, but it may potentially reject valid requests containing SQL keywords. The DataPower SQL injection filter action is designed to reject requests containing SQL keywords. DataPower services that need to accept some requests that contain SQL keywords, but reject others, may need a customized processing policy for those services to meet business requirements. The default filter may require customization specific to your data traffic.
Symptom
A request like the one below, containing the state abbreviation for Oregon, "OR", will, by design, be rejected by an SQL injection filter because OR is an SQL keyword.
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:sim="http://www.example.org/SimpleSOAP/">
<soapenv:Header/>
<soapenv:Body>
<sam:sayHello>
<sam:city>Portland</city>
<sam:state>OR</state>
</sam:sayHello>
</soapenv:Body>
</soapenv:Envelope>
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:sim="http://www.example.org/SimpleSOAP/">
<soapenv:Header/>
<soapenv:Body>
<sam:sayHello>
<sam:city>Portland</city>
<sam:state>OR</state>
</sam:sayHello>
</soapenv:Body>
</soapenv:Envelope>
The DataPower log will include some or all of the following messages, depending on the log level specified:
| [xmlparse] | [debug] | Parsing document: 'store:///SQL-Injection-Patterns.xml' |
| [xmlparse] | [debug] | Finished parsing: store:///SQL-Injection-Patterns.xml |
| [xmlfilter] | [info] | Reject set: Message contains restricted content |
| [xsltmsg] | [error] | ***SQL INJECTION FILTER***: Message from x.xx.xxx.xxx contains possible SQL Injection Attack of type 'SQL Keyword Injection' Offending content: 'OR'. Full Message: |
Cause
In the first request above in the Symptom section, "OR" is part of a valid request as the state abbreviation for Oregon; however, "OR" is an SQL keyword that can be used in SQL injection attacks. Depending on the backend application logic, a request like the following could be a security threat:
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:sim="http://www.example.org/SimpleSOAP/">
<soapenv:Header/>
<soapenv:Body>
<sam:sayHello>
<sam:city>Boston</city>
<sam:state>MA' OR '1'='1</state>
</sam:sayHello>
</soapenv:Body>
</soapenv:Envelope>
The DataPower SQL injection filter action is designed to reject both example requests. A DataPower service that could potentially receive both of these sample requests requires customization to accept the valid request and reject the security threat.
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:sim="http://www.example.org/SimpleSOAP/">
<soapenv:Header/>
<soapenv:Body>
<sam:sayHello>
<sam:city>Boston</city>
<sam:state>MA' OR '1'='1</state>
</sam:sayHello>
</soapenv:Body>
</soapenv:Envelope>
The DataPower SQL injection filter action is designed to reject both example requests. A DataPower service that could potentially receive both of these sample requests requires customization to accept the valid request and reject the security threat.
Diagnosing The Problem
Examine DataPower log to understand the message being rejected by the filter and the offending content in the message.
Resolving The Problem
Any modifications to the provided filter could potentially increase susceptibility to threats. The risk introduced by changing the service processing policy has to be very carefully evaluated. Creating a modified copy of the SQL-Injection-Filter stylesheet to allow the rejected content, such as "OR," is not recommended. 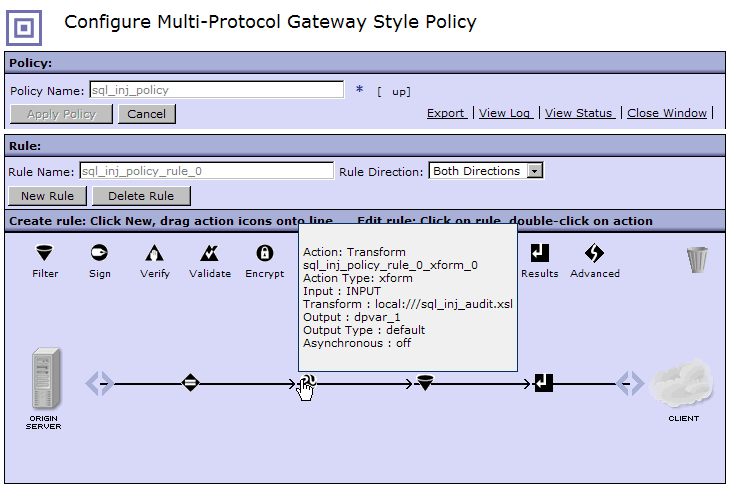

One approach to consider is to use a transform action that can look for and allow expected, valid input, such as <sam:state>OR</state> , reject obvious problem data, and then use the SQL injection filter to scan for cases not handled in the transform action.
- Add a transform action before the filter action in the service processing policy with a variable as the output context, for example, dp_var1. The transform action will do additional security threat checking in advance of the SQL injection filter action. The SQL injection filter will act on the output from the transform action, rather than on the original input request.

- In the stylesheet associated with transform action:
-
- Include code to audit the element that would ordinarily be rejected by the filter, but can contain valid data.
- In this specific example, stylesheet code to verify that the length of the <sam:state>OR</state> text is only two bytes, or a check to verify the <sam:state> element contains a valid state abbreviation could be included in the styleseheet. Stylesheet code that checked <sam:state> elements for a length of two
-
- would not find a problem with: <sam:state>OR</state>
but would find an issue with: <sam:state>MA' OR '1'='1</state>
- would not find a problem with: <sam:state>OR</state>
-
- If the stylesheet code finds a possible threat: Use dp:reject to reject the request. For this example, if the length of the <sam:state> element text is longer than two, a dp:reject would be issued to terminate the transaction.
- If the stylesheet determines the input is valid: Include code to remove the SQL keyword from the input. In this example, "OR" could be removed from the <sam:state> element.
-
-
- <?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:sim="http://www.example.org/SimpleSOAP/">
<soapenv:Header/>
<soapenv:Body>
<sam:sayHello>
<sam:city>Portland</city>
<sam:state></state>
</sam:sayHello>
</soapenv:Body>
</soapenv:Envelope>
- <?xml version="1.0" encoding="utf-8"?>
-
- Keep the SQL injection filter action, which can continue to use the standard stylesheet, store:///SQL-Injection-Filter.xsl, as the next action in the processing policy. Modify the input context for the filter action so that it will now act on the output from the transform action in variable dp_var1. The SQL injection filter will check the remainder of the input request for possible threats.

-
- Change the input context of the processing action after the filter action from PIPE to INPUT. Input context INPUT specifies use of the original input request for the processing action after the filter. The transform action validated the original input, the SQL injection filter action checked the original input minus the "OR" removed from the <sam:state> element. Requests that pass both checks will continue to be processed by the result action, which will send the original input to the backend.

Related Information
[{"Business Unit":{"code":"BU053","label":"Cloud & Data Platform"},"Product":{"code":"SS9H2Y","label":"IBM DataPower Gateway"},"ARM Category":[{"code":"a8m50000000CdoYAAS","label":"DataPower->MGMT (MM)->APIM \/ APIC"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)","Line of Business":{"code":"LOB45","label":"Automation"}}]
Was this topic helpful?
Document Information
Modified date:
13 August 2020
UID
swg21444739