Configuring an MDM policy in the MaaS360 Portal
The administrator can configure an MDM policy to require single sign-on and checks for conditional access on apps before those apps are downloaded to a managed device.
The Enterprise single sign-on setting in the Apps workflow allows only the administrator to select apps that use single sign-on and conditional access in the MaaS360® MDM policy. This setting does not enable single sign-on and conditional access on the mobile device. The administrator configures an iOS MDM or an Android MDM policy in the MaaS360 Portal and then selects the apps that must use single sign-on and conditional access.
To allow apps in an MDM policy for single sign-on and conditional access, follow these steps: 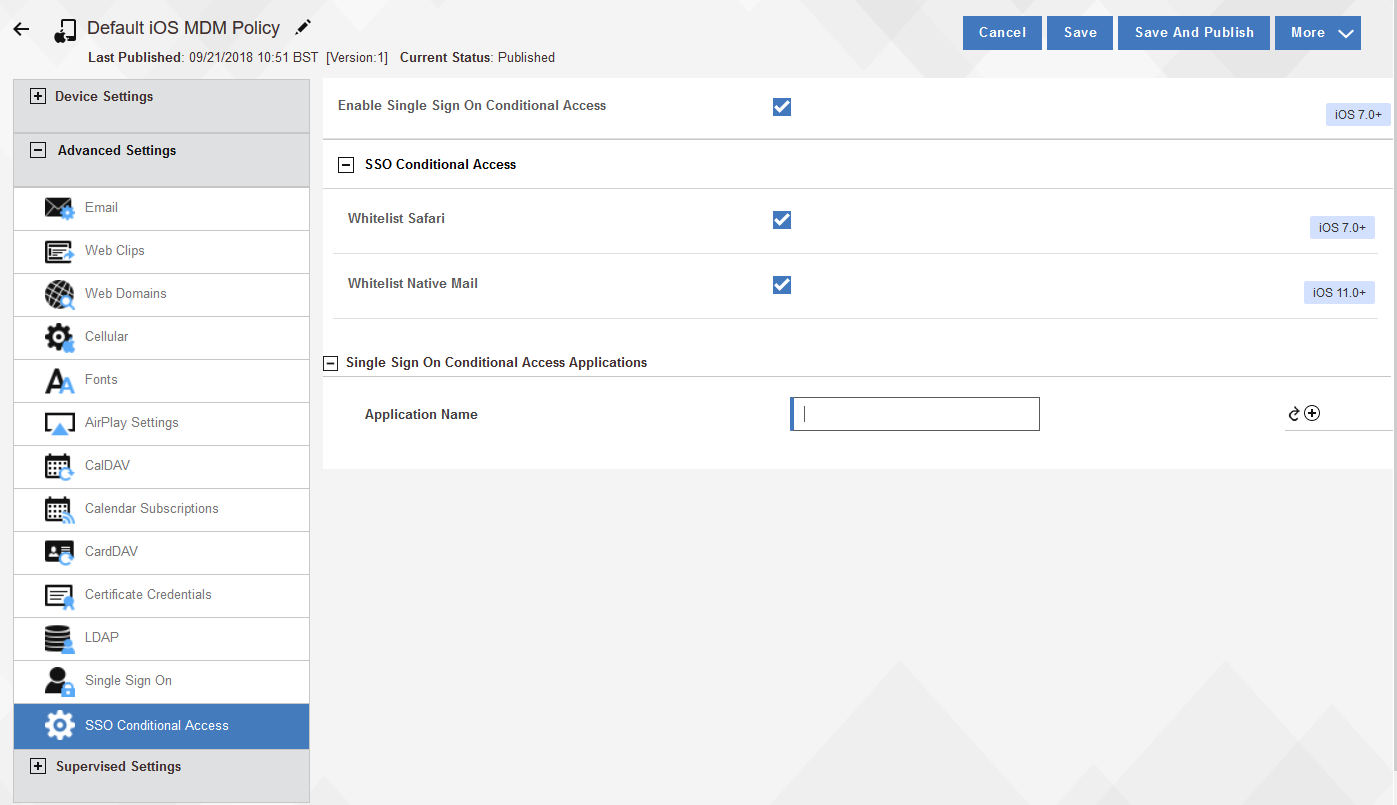
- In an iOS MDM policy, go to . The workflow automatically completes policy information when the administrator enters a partial app name. Save and publish the policy.
- In an Android MDM policy, go to . The workflow automatically completes policy information when the administrator enters a partial app name. Save and publish the policy.
- In a Windows MDM policy, go to and select Yes to enable. You do not have to allow apps that require single sign-on. By default, all Windows browser applications (Internet Explorer, Edge, Firefox, Chrome) and all native applications are allowed to use single sign-on if those apps are configured in the Verify portal. Save and publish the policy.

Note: The administrator should configure and run test policies first before making changes to the
production policies.
What to do next: Configure the SSO payload on a device