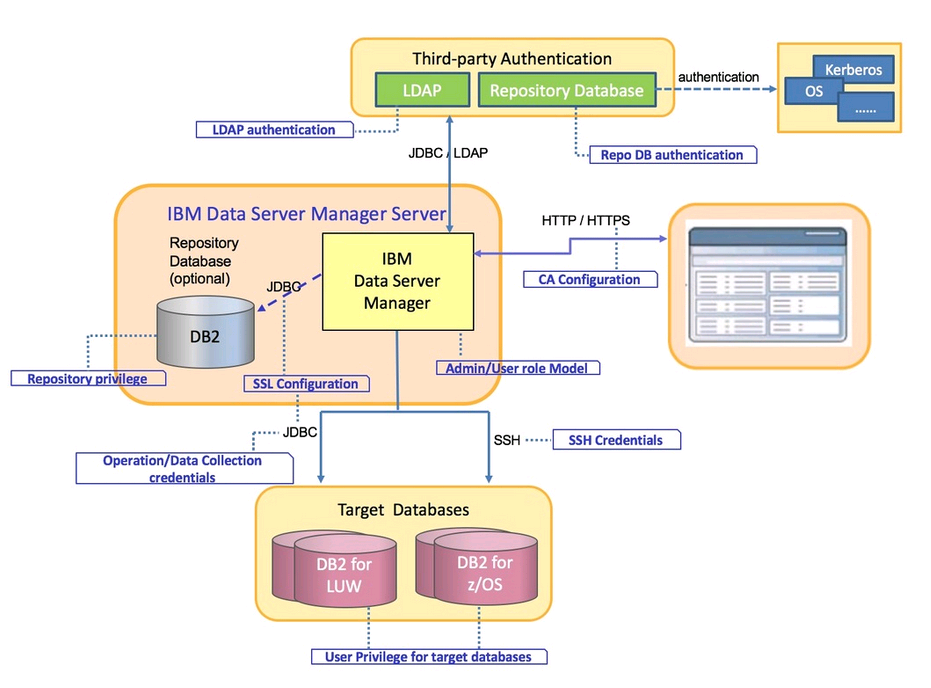
Security Architecture of IBM Data Server Manager (DSM)
Access to DSM features, and the data that DSM manages, is controlled through authentication and authorization.
DSM can be accessed using the secure HTTPS protocol, as well as unsecured HTTP.
Access to DSM is managed either by DSM itself or by authenticating facilities that reside outside of DSM, like an LDAP server or repository database. Access within DSM (authorization)is managed by assigning user roles and privileges. User privileges and operation/data collection credentials are used to ensure the security for target databases.
The diagram below provides a high-level view of DSM security.