Custom search base support for LDAP group and user entity in SCIM group and user APIs
From the foundational services version 3.21 and later, you can use custom search base for LDAP group entity in SCIM group APIs. And, from the foundational services version 3.22 and later, you can use custom search base for LDAP user entity in SCIM user APIs. For now, the custom search base for the LDAP group entity and user entity are supported only through APIs, not from your product UI.
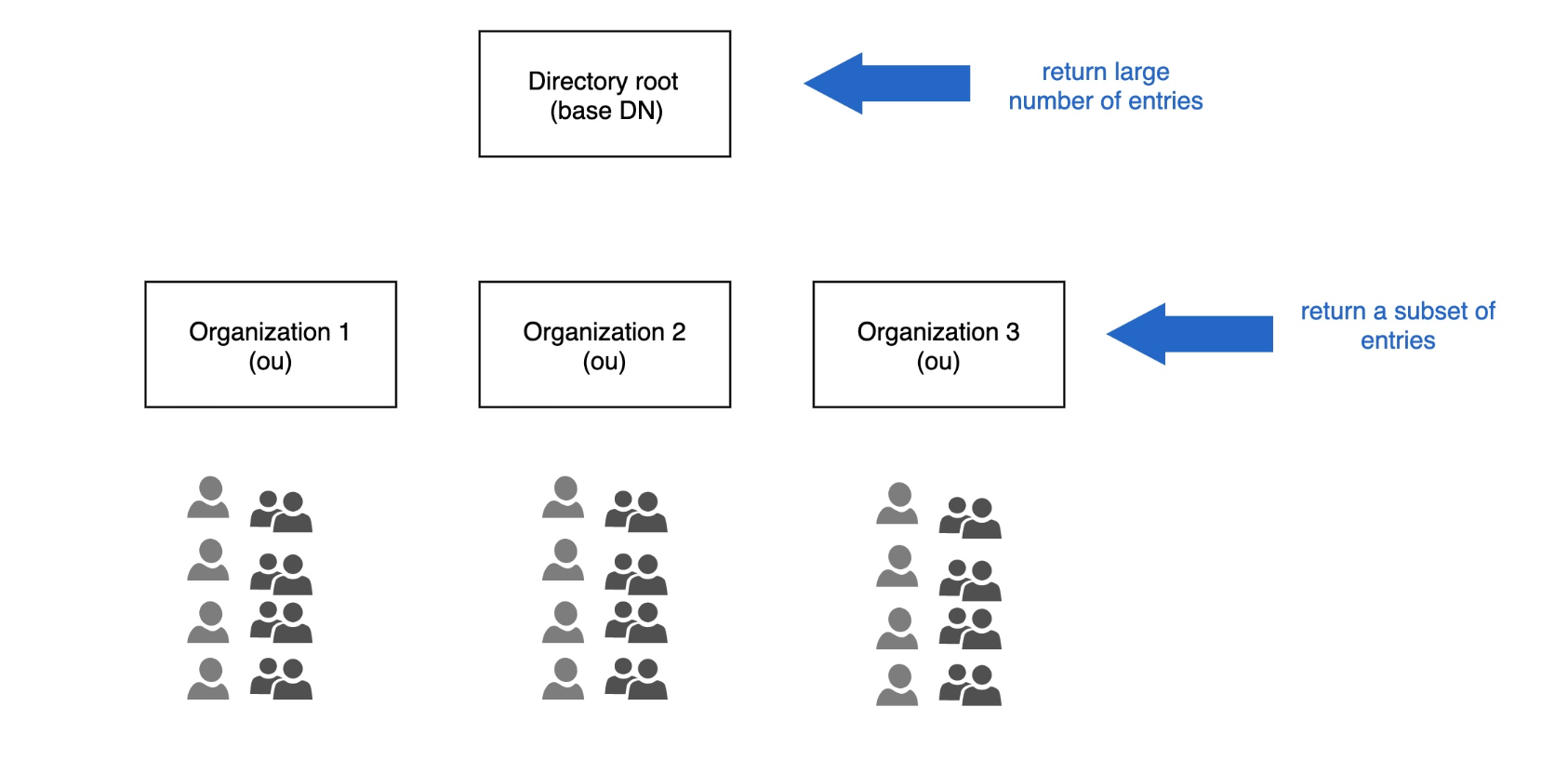
The structure of the LDAP server is organized as a tree hierarchy. The leaves of the tree represents an individual user account or a group with a common name (cn) and other attributes. The classification of the LDAP tree as follows:
-
The root directory structure of the LDAP server is the Base DN. Base DN is the distinguished name of the search base. It is further classified into sub-classes such as country (c), domain component (dc) and organization name (o). For example: dc=abc,dc=com.
-
The subtree of the LDAP server is Organizational Unit (ou) that allows you to perform a group search in a specific search base.
In the foundational services version 3.20 and earlier, if you have a large number of users/groups in the LDAP server, then the result set of your query can exceed the server-side page limit of the LDAP server. To overcome this limitation, custom search base is introduced with the foundational services version 3.21 and later. The custom search is useful in a scenario when you have multiple organizations in your LDAP server and the custom search base allows you to isolate each organization in separate namespace, and search the LDAP group and user under the organizations.
Note:
-
The custom search base specifies the sub tree of the LDAP server for the search call for the given entity type that overrides the base DN in search operations. For example, if the base DN is o=ibm,c=us and the search base for the group entity type is defined to be ou=iUsers,o=ibm,c=us, then all search calls for group will be made under subtree, ou=iUsers,o=ibm,c=us. Multiple search bases can be configured for the same entity type.
-
Using custom search base for LDAP user entity in SCIM user APIs, you can be able to configure search bases per LDAP connection. The corresponding search bases is used over BaseDN for the user search.
Enabling custom search base for LDAP group by using the directory management APIs
The Directory management API is enhanced with the LDAP_GROUP_SEARCHBASE_LIST parameter to support custom search base for LDAP group entity. The LDAP_GROUP_SEARCHBASE_LIST parameter defines a list of search bases for LDAP
groups. Its data type should be the list. And, it is an optional parameter. You can use this parameter if required. To enable the custom search base for SCIM groups APIs, add the LDAP_GROUP_SEARCHBASE_LIST field with the list of search
bases. For example:
"LDAP_GROUP_SEARCHBASE_LIST":["OU=searchbase1,DC=ibmtest,DC=com","OU=searchbase2,DC=ibmtest,DC=com","OU=searchbase3,DC=ibmtest,DC=com"]
The following API shows how to enable the custom search base for LDAP group entity while creating an LDAP connection:
- API version
- 1.0.0
- API URI components
-
- Scheme
HTTPS
- Host IP
Cluster Master Host
- Port number
Cluster Master API Port
- Path
idmgmt/identity/api/v1/directory/ldap/onboardDirectory
- Command
POST
- Command output format
application/json
curl -k -X POST 'https://<cluster_address>/idmgmt/identity/api/v1/directory/ldap/onboardDirectory'
--header "Authorization: bearer $ACCESS_TOKEN" \
--header 'Content-Type: application/json'
-d
'{
"LDAP_ID": "msad",
"LDAP_URL": "ldap://corp.abc.com:389",
"LDAP_BASEDN": "DC=ibmtest,DC=com",
"LDAP_BINDDN": "CN=Administrator,cn=Users,DC=ibmtest,DC=com",
"LDAP_BINDPASSWORD": "password in base64 encoded",
"LDAP_TYPE": "Microsoft Active Directory",
"LDAP_USERFILTER": "(&(sAMAccountName=%v)(objectclass=person))",
"LDAP_GROUPFILTER": "(&(cn=%v)(objectcategory=group))",
"LDAP_USERIDMAP": "user:sAMAccountName",
"LDAP_GROUPIDMAP":"*:cn",
"LDAP_GROUPMEMBERIDMAP": "memberOf:member"
"LDAP_GROUP_SEARCHBASE_LIST":["OU=searchbase1,DC=ibmtest,DC=com","OU=searchbase2,DC=ibmtest,DC=com","OU=searchbase3,DC=ibmtest,DC=com"]
}'
To use the LDAP directory management APIs, you need to get the host details, and the base64-encoded password for the "LDAP_BINDPASSWORD" parameter. For more information, see Creating an LDAP connection.
By using Directory management API, you can also enable the custom search base for LDAP group while updating the existing LDAP directory. For more information, see Update an LDAP directory.
Enabling custom search base for LDAP user by using the directory management APIs
The Directory management API is enhanced with the LDAP_USER_SEARCHBASE_LIST parameter to support custom search base for LDAP user entity. The LDAP_USER_SEARCHBASE_LIST parameter defines a list of search bases for LDAP users.
Its data type should be the list. And, it is an optional parameter. You can use this parameter if required. To enable the custom search base for SCIM user APIs, add the LDAP_USER_SEARCHBASE_LIST field with the list of search bases.
For example:
"LDAP_USER_SEARCHBASE_LIST":["OU=searchbase1,DC=ibmtest,DC=com","OU=searchbase2,DC=ibmtest,DC=com","OU=searchbase3,DC=ibmtest,DC=com"]
The following API shows how to enable the custom search base for LDAP user entity while creating an LDAP connection:
- API version
- 1.0.0
- API URI components
-
- Scheme
HTTPS
- Host IP
Cluster Master Host
- Port number
Cluster Master API Port
- Path
idmgmt/identity/api/v1/directory/ldap/onboardDirectory
- Command
POST
- Command output format
application/json
curl -k -X POST 'https://<cluster_address>/idmgmt/identity/api/v1/directory/ldap/onboardDirectory'
--header "Authorization: bearer $ACCESS_TOKEN" \
--header 'Content-Type: application/json'
-d
'{
"LDAP_ID": "msad",
"LDAP_URL": "ldap://corp.abc.com:389",
"LDAP_BASEDN": "DC=ibmtest,DC=com",
"LDAP_BINDDN": "CN=Administrator,cn=Users,DC=ibmtest,DC=com",
"LDAP_BINDPASSWORD": "password in base64 encoded",
"LDAP_TYPE": "Microsoft Active Directory",
"LDAP_USERFILTER": "(&(sAMAccountName=%v)(objectclass=person))",
"LDAP_GROUPFILTER": "(&(cn=%v)(objectcategory=group))",
"LDAP_USERIDMAP": "user:sAMAccountName",
"LDAP_GROUPIDMAP":"*:cn",
"LDAP_GROUPMEMBERIDMAP": "memberOf:member"
"LDAP_USER_SEARCHBASE_LIST":["OU=searchbase1,DC=ibmtest,DC=com","OU=searchbase2,DC=ibmtest,DC=com","OU=searchbase3,DC=ibmtest,DC=com"]
}'
To use the LDAP directory management APIs, you need to get the host details, and the base64-encoded password for the "LDAP_BINDPASSWORD" parameter. For more information, see Creating an LDAP connection.
By using Directory management API, you can also enable the custom search base for LDAP user while updating the existing LDAP directory. For more information, see Update an LDAP directory.